- Define
- Relate
- List
- Discuss
- See
- Hear
- unLove
Definitions
from The American Heritage® Dictionary of the English Language, 5th Edition.
- noun Malicious computer software that interferes with normal computer functions or sends personal data about the user to unauthorized parties over the Internet.
from Wiktionary, Creative Commons Attribution/Share-Alike License.
- noun computing Software which has been designed to operate in a malicious, undesirable manner.
Etymologies
from The American Heritage® Dictionary of the English Language, 4th Edition
from Wiktionary, Creative Commons Attribution/Share-Alike License
Blend of malicious and software
Support
Help support Wordnik (and make this page ad-free) by adopting the word malware.
Examples
-
The term malware, derived from «malicious software,» refers to any software specifically designed to harm your computer or the software it’s running.
Working together to fight malware
-
The term malware, derived from «malicious software,» refers to any software specifically designed to harm your computer or the software it’s running.
Archive 2008-04-01
-
The term malware, derived from «malicious software,» refers to any software specifically designed to harm your computer or the software it’s running.
Congratulations to our U.S. and Canadian Anita Borg Scholars
-
The term malware can be used to describe a program that is as harmless as an annoying pop-up box that attempts to direct a user to a website in order to increase the website’s traffic.
Citizendium, the Citizens’ Compendium — Recent changes [en]
-
The first is that it does indeed represent a significant innovation in malware; the fact that it targets a specific piece of technology – the Siemens controller – that plays a critical role in the industrial infrastructure of every advanced country is new and troubling.
Meet the Stuxnet, so much subtler than a tactical nuclear device
-
The malware is in Unreality Mag’s third party ad server — it’s a rogue ad in rotation with regular ads, so you don’t always see it, but if you visit Unreality Mag often enough, you’ll find it.
Top Ten A.I. Characters (redux)
-
ScanSafe says the malware is still active on parishilton. com, and some 15,000 other sites are similarly compromised.
That’s not hot: Hacked celeb sites pose security threat
-
The malware is in Unreality Mag’s third party ad server — it’s a rogue ad in rotation with regular ads, so you don’t always see it, but if you visit Unreality Mag often enough, you’ll find it.
Top Ten A.I. Characters (redux) » E-Mail
-
Anyways, malware is the first thing that comes to mind when you say it started opening up a ton of windows unsolicited — especially if they were, ahem, of a prurient nature.
Jean’s Knitting
-
Seems to me, this seeding malware is a direct violation of the laws on computer privacy/security in the US.
MediaSentry Super-Secret Squirrel tech
English[edit]
Etymology[edit]
Blend of malicious + software or from mal- + -ware.
Pronunciation[edit]
- (UK) IPA(key): /ˈmæl.weə(ɹ)/
- Hyphenation: mal‧ware
Noun[edit]
malware (usually uncountable, plural malwares)
- (computing) Software which has been designed to operate in a malicious, undesirable manner.
- Hyponyms: see Thesaurus:malware
-
2020 October 19, “U.S. Charges Russian Intelligence Officers in Major Cyberattacks”, in New York Times[1]:
-
In a follow-up attack that hit Kyiv’s power grid a year later, the suspects used a second piece of malware, called Industroyer, to cut power for an hour, the indictment said. The malware, according to experts, posed one of the greatest digital threats to critical infrastructure since Stuxnet, the computer attack by the United States and Israel that took out Iran’s uranium centrifuges in 2009.
-
Descendants[edit]
- Amharic: ማልዌር (malwer)
- Bengali: মালওয়্যার (maloōẇyar)
- → French: maliciel (calque)
- → German: Malware
- Hindi: मैलवेयर m (mailveyar)
- Japanese: マルウェア (maruwea)
- Korean: 맬웨어 (maerweeo)
- Macedonian: малвер m (malver)
- Serbo-Croatian: malver m
- Slovak: malvér m
- Thai: มัลแวร์ (mal-wɛɛ)
Translations[edit]
| A user suggests that this English entry be cleaned up. | |
|---|---|
| Please see the discussion on Requests for cleanup(+) or the talk page for more information and remove this template after the problem has been dealt with. |
software developed to cause harm to a computer system
- Afrikaans: skadelike programmatuur
- Amharic: ማልዌር (malwer)
- Arabic: برنامج ضار
- Armenian: վնասագիր (vnasagir), վնասակար ծրագրային ապահովում (vnasakar cragrayin apahovum), վնասարար ծրագրաշար (vnasarar cragrašar)
- Azerbaijani: ziyankar proqram, ziyanverici proqram
- Basque: software kaltegarria
- Belarusian: шкоднасная праграма f (škódnasnaja prahrama)
- Bengali: মালওয়্যার (bn) (maloōẇyar), ক্ষতিকর সফটওয়্যার (khotikor śophoṭoōẇyar)
- Bulgarian: злонамерен софтуер m (zlonameren softuer)
- Chinese:
- Mandarin: 流氓軟件/流氓软件 (zh) (liúmáng ruǎnjiàn), 惡意軟件/恶意软件 (èyì ruǎnjiàn)
- Czech: malware (cs) m, škodlivý software (cs) m
- Danish: malware ?, skadelig software ?
- Dutch: malware (nl) m, schadelijke software m
- Esperanto: fiprogramaro
- Estonian: pahavara, ründevara
- Finnish: haittaohjelma (fi)
- French: maliciel (fr) m, logiciel malveillant m
- Georgian: მავნე პროგრამა (mavne ṗrograma), საზიანო პროგრამა (saziano ṗrograma)
- German: Schadsoftware (de) f, Malware (de) f, Schadprogramm (de) n
- Greek: κακόβουλο λογισμικό n (kakóvoulo logismikó), επιβλαβές λογισμικό n (epivlavés logismikó)
- Hebrew: תוכנות מזיקות f, תוכנה זדונית f
- Hindi: मैलवेयर ? (mailveyar), दुर्भावनापूर्ण सॉफ़्टवेयर ? (durbhāvnāpūrṇ sŏfṭaveyar)
- Hungarian: rosszindulatú szoftver, kártevő szoftver, kártékony szoftver
- Indonesian: perangkat perusak, perangkat lunak berbahaya, perangkat lunak jahat
- Italian: malware (it) m, software dannoso m
- Japanese: マルウェア (maruwea), 悪意のソフトウェア (akui no sofutowea), 不正ソフトウェア (fusei sofutowea), 有害なソフトウェア (yūgai na sofutowea)
- Javanese: piranti pangrusak
- Korean: 맬웨어 (maerweeo), 악성 소프트웨어 (akseong sopeuteuweeo)
- Latvian: ļaunprogrammatūra f, ļaunatūra f
- Lithuanian: kenkėjiška programa ?
- Macedonian: злонамерен софтвер m (zlonameren softver), штетен софтвер m (šteten softver)
- Malay: perisian berniat jahat, perisian berbahaya, perisian hasad
- Maori: pūmanawa kino
- Marathi: मालवेअर m (mālvear), दूर्भावनापूर्ण सॉफ्टवेअर ? (dūrbhāvnāpūrṇa sŏphṭavear)
- Nepali: मालवेयर (mālaveyar)
- Norwegian: skadelig programvare f, skadevare f
- Persian: بدافزار (fa), نرم افزار مخرب
- Polish: szkodliwe oprogramowanie (pl) n, złośliwe oprogramowanie (pl) n
- Portuguese: malware m, programa malicioso m
- Punjabi: ਮਾਲਵੇਅਰ ? (mālveara), ਦੁਰਭਾਵਨਾਪੂਰਣ ਸੌਫਟਵੇਅਰ ? (durbhāvanāpūraṇ sauphṭaveara)
- Romanian: malware n, software rău intenționat n
- Russian: вредоно́сная програ́мма f (vredonósnaja prográmma), зловре́дная програ́мма f (zlovrédnaja prográmma), вредоно́с (ru) m (vredonós), зловре́д (ru) m (zlovréd)
- Serbo-Croatian:
- Cyrillic: малвер m, штетни со̏фтве̄р m, злонамјерни со̏фтве̄р m / злонамерни со̏фтве̄р m
- Roman: malver (sh) m, štetni sȍftvēr (sh) m, zlonamjerni sȍftvēr (sh) m / zlonamerni sȍftvēr m
- Slovak: malvér (sk) m, škodlivý softvér m
- Slovene: škodljivo programje n, zlonamerno programje n
- Spanish: malware (es) m, programa malicioso m
- Swedish: skadlig programvara c, sabotageprogram (sv) n
- Thai: มัลแวร์ (mal-wɛɛ), ซอฟต์แวร์ที่เป็นอันตราย
- Turkish: zararlı yazılım
- Turkmen: zyýanly programma
- Ukrainian: шкідлива програма f (škidlyva prohrama)
- Uzbek: zararli dastur
- Vietnamese: mã độc, phần mềm độc hại, phần mềm ác ý, phần mềm ác tính, phần mềm gây hại
- Welsh: maleiswedd f
See also[edit]
- backdoor
- exploit
- URL injection
- wabbit
- -ware
Further reading[edit]
malware on Wikipedia.Wikipedia
Czech[edit]
Etymology[edit]
Borrowed from English malware.
Noun[edit]
malware m
- (computing) malware
- Synonym: škodlivý software
Declension[edit]
Further reading[edit]
malware on the Czech Wikipedia.Wikipedia cs
Danish[edit]
Etymology[edit]
Borrowed from English malware.
Noun[edit]
malware (singular definite ?, plural indefinite malware)
- (computing) malware (software developed to harm a computer system)
- Synonym: skadelig software
Further reading[edit]
malware on the Danish Wikipedia.Wikipedia da
Dutch[edit]
Etymology[edit]
Borrowed from English malware.
Pronunciation[edit]
- IPA(key): /ˈmɑl.ʋɛːr/ (usually pronounced in a way approximating the English)
- Hyphenation: mal‧ware
Noun[edit]
malware m (uncountable)
- malware
French[edit]
Etymology[edit]
Borrowed from English malware.
Pronunciation[edit]
- IPA(key): /ma.lwɛʁ/
Noun[edit]
malware m (plural malwares)
- (computing) malware (software developed to harm a computer system)
- Synonyms: maliciel, logiciel malveillant, (rare) logiciel nuisible, (rare) pourriciel
Further reading[edit]
logiciel malveillant on the French Wikipedia.Wikipedia fr
Italian[edit]
Etymology[edit]
Borrowed from English malware.
Noun[edit]
malware m (uncountable)
- (computing) malware (software developed to harm a computer system)
- Synonym: software dannoso
Further reading[edit]
malware on the Italian Wikipedia.Wikipedia it
Portuguese[edit]
Etymology[edit]
Unadapted borrowing from English malware.
Pronunciation[edit]
- (Brazil) IPA(key): /mawˈwɛʁ/ [maʊ̯ˈwɛh]
- (São Paulo) IPA(key): /mawˈwɛɾ/ [maʊ̯ˈwɛɾ]
- (Rio de Janeiro) IPA(key): /mawˈwɛʁ/ [maʊ̯ˈwɛχ]
- (Southern Brazil) IPA(key): /mawˈwɛɻ/ [maʊ̯ˈwɛɻ]
- (Portugal) IPA(key): /maˈlwɛɾ/
Noun[edit]
malware m (plural malwares)
- (computer security) malware (software developed to harm a computer system)
- Synonym: software malicioso
Further reading[edit]
malware on the Portuguese Wikipedia.Wikipedia pt
Romanian[edit]
Etymology[edit]
Unadapted borrowing from English malware.
Noun[edit]
malware n (plural (rare) malware-uri)
- (computing) malware
- Synonyms: software rău intenționat, (rare) software dăunător
Declension[edit]
Further reading[edit]
software rău intenționat on the Romanian Wikipedia.Wikipedia ro
Spanish[edit]
Etymology[edit]
Unadapted borrowing from English malware.
Pronunciation[edit]
- IPA(key): /ˈmalweɾ/ [ˈma.lweɾ]
- Rhymes: -alweɾ
Noun[edit]
malware m (plural malwares)
- (computing) malware (software developed to harm a computer system)
- Synonym: software malicioso
Further reading[edit]
malware on the Spanish Wikipedia.Wikipedia es
Tagalog[edit]
Etymology[edit]
Unadapted borrowing from English malware.
Noun[edit]
malware
- (computing) malware (software developed to harm a computer system)
Further reading[edit]
malware on the Tagalog Wikipedia.Wikipedia tl
Malware или «Малварь», сокращенно от английского «malicious software» — вредоносное программное обеспечение, имеющее своей целью в той или иной форме нанести ущерб пользователю или компьютеру и его содержимому. Малварь — общее название для всех видов кибер-угроз, таких как: вирусы, трояны, шпионские программы, кейлоггеры, adware и др. Malware или вредоносы — достаточно распространенный вид кибер-угроз, и столкнуться с вредоносным ПО может каждый.
Какой вред может причинить Malware моему компьютеру?
Вредоносные программы создают множество проблем пользователю — от маленьких почти незаметных неудобств до серьезного финансового вреда:
|
Как удалить Malware с компьютера?
Такая программа хорошо маскируется и может ничем не выдавать свое присутствие для пользователя. Сегодня существует множество программных инструментов для того, чтобы очистить компьютер от Malware — антивирусы и специализированные Anti-Malware программы. Однако очень многие вредоносные программы (Malware) обладают настолько высокой степенью защиты, что их практически невозможно удалить после запуска.
Как SkyDNS блокирует доступ к ресурсам, содержащим Malware?
SkyDNS предлагает альтернативный способ избежать вредоносных программ. Наша система аналитики, основанная на принципах машинного обучения, позволяет с точностью до 98% определять ресурсы, содержащие вредоносное ПО и эффективно блокировать доступ к ним. Предотвратите негативное влияние Malware еще до того, как вредоносное программное обеспечение попадет на ваш компьютер. Предлагаем ознакомиться с популярными решениями для контент-фильтрации дома, в школе или в офисе от компании SkyDNS!
There are thousands of technical terms are used for computer security, many of them are bit hard to explain in simple words, that’s why they are often used incorrectly. When it comes to Virus, malware, worm, etc. a non-tech savvy person refers them as a virus. I get lots of such comments, messages and requests on my YouTube channel where people refer everything as virus whether it is a Virus, trojan, spyware, adware or even an unknown software. Sometimes you may get pop up on various Websites that your computer is infected with Virus, and you need to scan your computer, but that is not true, such pop-ups during web browsings are ads running by different advertisers, and they want to sell their product by scaring you.
What is the difference: Virus, Malware, Trojan, Worm, Spyware, etc.
So how much do you know about Virus, Malware, Trojan, Worms, Rootkit, Adware, Ransomware, Exploit, etc? In this detailed article, I will discuss the difference between a virus, malware, trojan, etc. which will help you to find the correct solution for your computer problems.
So let’s get started.
What is Malware?
The word Malware is used for malicious software and is a general term for Virus, worm, trojan, rootkit, spyware and nearly everything which is specifically designed to harm your computer and steal information. Malware does not include buggy software, programs you don’t like, software which crashes a lot but software which are specifically created to harm our PC.
The most common word used for any bad software, however, we use the term “malware” now. A virus is a program which can self-replicate itself after infecting a computer, it attach itself to other programs and get installed while installing the genuine software. After the execution of viral code it may destroy host files and starts infecting files into a PC, from there it creates a replica of itself and travels from PC to PC via external drive, the Internet, and malicious websites.
Like a biological Virus goes from one human to another and it spreads through the environment, touch, cough, etc. In the same way, a computer virus spread itself from files to files and then from one device to another. Computer virus attaches themselves to executable files and can attack into several parts of windows like the registry, services, or a specific software, some of them can attack MBR (master boot record), autorun scripts, BIOS and MS Office macros.
Overall, a virus is designed to break into your computer, destroy files and the right software, corrupt your files, make your computer completely inoperable which may lead to the complete format of your PC.
You can always make your PC safe using a good antivirus program with latest update and virus definition, always avoid suspicious files from email and rouge websites.
Worm
Worms are similar to the Virus, but a worm doesn’t need a host program to execute itself, worms are the standalone program. It uses a computer network to spread itself, and it relies on network loophole and security failure to travel from one host to another automatically and usually don’t requires user intervention. Since worms don’t require any initiation they can spread speedily across the network, infecting every PC in their path, Worms are most well know type of malware which affects more computers than a virus can.
Here are few well know worms like ILOVEYOU which transmitted through emails and cost businesses 5.5 billion US dollar in damage. The Code Red worm damaged 359,000 websites around the globe, SQL Slammer slowed down the entire web for an extended period, and the Blaster worm would force your PC to reboot continuously.
Today’s security standards make it difficult for a worm to infect user’s PC via network, but none of the security measures can guarantee that they would be able to stop any future worm. However, make sure your Firewall is on and use good security software to avoid probable worm attacks.
Trojan Horse
Trojan is another kind of malware which looks harmless, but it contains malicious code which creates a backdoor that allows your PC to be controlled remotely. The term Trojan horse came into existence from the Troy Story where the Greeks used a wooden horse to infiltrate Troy.
Unlike virus trojan doesn’t replicate itself, a trojan gets installed by users unknowingly. Once Trojan has infected your PC it can be used for different malicious purpose, like sending out spams, attacking a network or computer, DDoS attack on any website, spreading viruses, deleting files, stealing data, activating and spreading other malware.
In simple words, trojan creates backdoor which gives access to malicious users, once they are able to control your PC they can do whatever they want.
So how these Trojans can get access to your system? If you ever tried to download a crack, keygen or any program to get the full version of any software then you might get affected by such trojan, think why would anyone create a crack for software? What they are getting in return? First, they may get advertising revenue from the crack hosting sites, but such scammer has bigger goals they create trojan and attach them to cracks and keygen, once you install a crack you also install those trojans which put your computer at high risk.
So avoid using cracks, keygen or patch for any software.
Spyware
Spyware is another type of malware which collects data from your PC without your knowledge and permission, spyware runs in the background and collects your personal information like your browsing pattern, sites you visit, email, cookies, saved data into browsers, website passwords and even credit card details.
Spyware is similar to the Trojan horse in that users unknowingly install the product when they install some other software or freeware. Spyware exists as an independent program then can track your keystrokes, snoop on other files, change your default homepage, monitor your activity, stealing your personal information and send back them to the creators. Your data can be used in several malicious ways which include selling your data, targeted advertising, scams, spam or identity theft.
Adware
Adware is a bit different from spyware the primary intent of adware is to show different advertisements, pop-up window, flash ads, links to rogue websites, redirecting to different links, change homepage and default search engine, slows down browsing speed, causes frequent browser crash.
Adware monitors your browsing pattern, cookies, interest and sends them back to the creators where they re-target the users with relevant ads; technically adware is not a virus.
Whenever you install freeware these adware comes along with them; these are sponsored programs which make the main program free to use in exchange of ads when you uninstall the free program the ads will stop running on your computer.
Adware is considered as a legitimate alternative to the consumers who don’t want to pay for the software, games, programs and other free utilities. But sometimes we mistakenly install many Adware at the same time which becomes annoying, and some of them are tricky to remove.
Scareware
Scareware is another type of malware that uses social engineering to cause shock, anxiety or perception of threat and trick users to buy unwanted and potentially dangerous software.
Scareware generates pop-ups which resemble Windows system messages like particular error message saying there are problems found in your PC, registry error found, Computer at serious risk, virus found, etc. These pop-up messages are designed in a way which looks like they come from user’s operating system when they are actually a web page.
Scareware tricks users to download or buy fake antivirus, a firewall application, registry cleaner or a PC optimizer, usually a rogue software which has minimal to no use. This scareware may generate continuous pop-ups saying “Your Computer is infected with spyware or malware click here to fix it” now if a user clicks on any of such buttons they may end up installing rogue software which itself may be a malware.
Best practice to stay away from scareware is to ignore every popup saying such lame things while surfing the web, and do not click here and there on such pages. Scareware spreads by malvertising where a genuine ad company gets tricked by the advertiser which leads into spreading scareware.
Ransomware
Ransomware is a type of malware which prevents users from accessing their system. Ransomware locks down the system and asks for ransom through certain online payment methods in order to unlock the user’s computer.
Some of the ransomware encrypt files in the system hard drive, which makes it very hard to decrypt the data without the encryption key, paying ransom to the creator may or may not provide you the encryption key like crypto locker which encrypts individual files and folder.
Some ransomware only locks the system and do not encrypt the user’s data; such ransomware can be removed easily by a tech savvy user by booting the Windows computer in safe mode or using bootable antivirus disk.
Ransomware can affect MBR (Master boot record) which makes is tough to boot into the system without paying the ransom. However, there is no guarantee that they will unlock the system after paying the ransom, one of the famous ransomware was FBI Moneypak, which locks the system and asks for payment, it was widely spread into the US and Canada in 2012-2014.
Ransomware spread through trojans, scareware, email attachments, infected and pirated programs and from compromised websites and threaten users that they have been involved in illegal activities and pretend to be some legal entities.
Rootkit
A rootkit is a software or set of application typically malicious that enables administrator-level access to a computer or computer network. Rootkit get activated every time you boot into operating system since they activated before an operating system gets completely booted up which makes it very hard to detect by antivirus.
Rootkit can get to a computer by a Trojan, suspicious email attachments or by compromised websites after getting user level access to the system either by breaking a password or by exploiting any vulnerability into the system. Once a rootkit is installed it allows the installation of hidden files, hidden user accounts, processes and attackers can mask intrusion and get root access to the system.
A rootkit can monitor traffic, keystrokes, can create a backdoor for malicious usages by hackers, and it can remove installed programs and security suits in order to prevent the detection.
Bots
The bot is a short name for “robot” and is an automated process/script which interacts with other computer or network services; bot is a software program which automates different tasks over the Internet using specially written scripts.
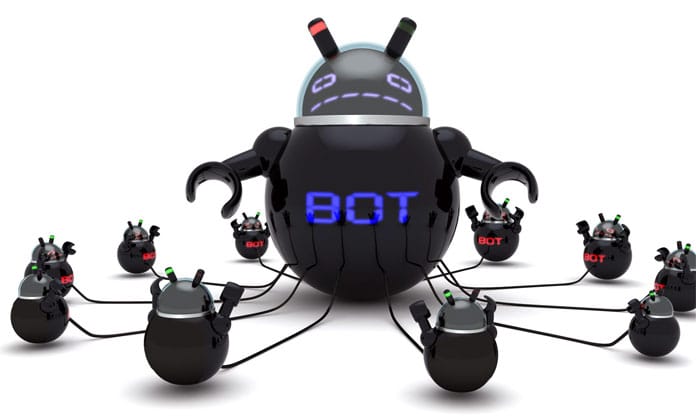
The central server is called “botnet” which connects with the several host computers using a bot, botnet can command every host computer for the different malicious purpose like denial-of-service attack, spreading malware, keystroke monitoring, spreading spams, collect passwords, gather financial information or generating massive traffic using host computers.
Bots do not work alone, once the army of bot affects the large number of computer they can be controlled by a master computer called command and control server and attackers can instructs them to work on their behalf using the master computer.
Vulnerability
Humans are prone to make mistakes which may lead to serious flaws. A computer vulnerability is a flaw in the software, operating system or service occurs by programming errors which allow cyber criminals to attack the system. Vulnerability leaves it open to the potential for exploitation in the form of unauthorized access or malicious behavior such as viruses, worms, Trojan horses, bots, ransomware, and other forms of malware.
Vulnerability consists of 3 main parts, a system flaw, attackers access to the flaw and capability to exploit the flaw in a system. First, an attacker finds the holes in a software of operating system then get the access to that security hole and then delivers malicious codes.
Exploit
Exploits take advantage of a particular vulnerability in the system, exploits in computer security refers to a piece of software or a sequence of commands that take advantage of vulnerability to carry out some form of malicious intent, such as Trojan horses, denial-of-service attack, worms or viruses.
When the vendor of software or operating system finds that an exploit is taking advantage of weakness in their software/OS, they issue a fix or patch in response. The user needs to update their software or Operating system to make it secure against the exploit. Failing to install a patch or fix for a given problem exposes the user to a security breach.
Combating Virus, Worms Trojan, Adware, Spyware, Ransomware, etc
Now you have a clear idea about the different type of malware, and what they can do to your computer, it is advised that always install a good antivirus which has high detection rate and can provide you protection from all known threat and should be able to block unknown threats also.
Never install any kind of crack keygen or pirated software, beware while visiting torrent, porn, gambling and other sensitive sites. Always keep your system updated with latest security patches and make sure the firewall is turned ON. While installing freeware keep an eye on what else they are offering apart from main software, do not click next and next too fast during installation.
Also Read-
- 10 Best Free Antivirus for Windows 7, 8 & 10 in 2016.
- Things to Know Before Buying Best Antivirus Software.
Definition from Wikipedia.org/wiki & Damage data by worms from lifehacker.com
This post is also available in: हिन्दी (Hindi) العربية (Arabic)
What is Malware?
Malware is an abbreviated form of “malicious software”. The word malicious means “having or showing a desire to cause harm to someone”. The word malware is a common term used to describe a virus, worm, trojan, or any other harmful program. This means that all viruses are malware and malware is a superset referring to any software/code that may/can cause harm to your computer.
Programs are also considered malware if they secretly act against the interests of the computer user. For example, at one point Sony music Compact discs silently installed a rootkit on purchasers’ computers with the intention of preventing illicit copying, but which also reported on users’ listening habits, and unintentionally created extra security vulnerabilities.
Who Creates Malware and Why?
Malware is created by a wide range of people such as vandals, swindlers, blackmailers, and other criminals. The main motive behind creating malware is to make money, but the other reasons may range from pranks to espionage and other serious crimes.
If you’re mystified as to why someone would want to put so much effort into attacking your computer or your mobile devices, you have to think of the type of people that create malware.
As the use of computers, mobile devices, and the Internet has grown, many people have the opportunities to benefit by creating this harmful computer malware. In the past, many of these malware creators were just pranksters trying to alleviate boredom and make a name for themselves.
While this is still true for some, but most of the malware is created for the following three main reasons:
- To make money: The malware is designed to capture information about the computer user and send it to the person or company responsible for making the malware. The information they collect is then used to target advertisements to your computer. These ads come in the form of e-mails and pop-ups on your computer. If enough computers get infected, they can earn money from all these ads displayed.
- To steal account information: The malware is also used in tricking a victim into providing personal data for identity theft which in turn is used to gain access to the victim’s crucial accounts like bank accounts.
- To cause problems and troubles for others: Some people create malware just because they enjoy causing trouble, making others suffer. Some malware can crash an entire network system and cause system outages for large companies, like banks or production companies.
Malware creation really flourishes in regions where cybercrime laws are not enforced and there are few opportunities for technically skilled people.
Classification of Malware
The classification of malware is based on the following ways:
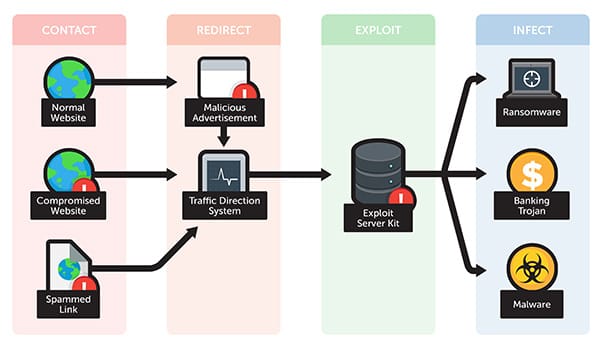
- Delivery method: The malware is classified based on its delivery method or attack methodology. These include drive-by downloads that distribute malware simply by visiting a website, phishing emails that trick victims into divulging data, man-in-the-middle attacks that take over control of a computer, or cross-site scripting where an attacker injects malicious code into the content of a website.
- Vulnerability type: The specific type of vulnerability that the malware exploits. Examples include SQL Injection used by attackers to gain access to or modify data, and domain spoofing where bad actors seduce web visitors to click on links to their ads or websites by making them look like other legitimate sites.
- The objective of the malware: For instance, Ransomware has a purely financial goal, whereas Spyware is out to capture confidential or sensitive information, and Keyloggers capture usernames and passwords.
- Target device: By the platform or device that the malware targets, such as mobile malware, or attacks that target a specific operating system.
- The approach of malware: The malware’s approach to stealth, or how it attempts to hide. Rootkits that typically replace legitimate operating system components with malicious versions are an example.
- Malware behaviour and characteristics: Specific behaviours and characteristics – like how the malware replicates and spreads, or other attributes that distinguish it from other forms of malware. This is the most common method of classifying malware.
Based on the above-mentioned characteristics, malware can be classified as:
1. Virus
A computer virus, is like a flu virus that is designed to spread from host to host and has the ability to replicate itself. Similarly, in the same way that flu viruses cannot reproduce without a host cell, computer viruses cannot reproduce and spread without programming such as a file or document.
A computer virus is a type of malicious code or program written to alter the way a computer operates and is designed to spread from one computer to another.
A virus operates by inserting or attaching itself to a legitimate program or document that supports macros in order to execute its code. In the process, a virus has the potential to cause unexpected or damaging effects, such as harming the system software by corrupting or destroying data.
2. Worm
A worm is a form of malware that operates as a self-contained application and can transfer and copy itself from computer to computer.
It’s this ability to operate autonomously, without the need for a host file or to hijack code on the host computer, that distinguishes worms from other forms of malware. Worms often use parts of an operating system that are automatic and invisible to the user.
They generally target pre-existing vulnerabilities in the operating system of the computers they attempt to infect. Many of the most widespread and destructive forms of malware have been worms.
3. Trojan
In computing, a Trojan horse (or simply trojan) is any malware that misleads users of its true intent. The term is derived from the Ancient Greek story of the deceptive Trojan Horse that led to the fall of the city of Troy.
Trojans are generally spread by some form of social engineering, for example where a user is duped into executing an email attachment disguised to appear not suspicious, (e.g., a routine form to be filled in), or by clicking on some fake advertisement on social media or anywhere else.
Trojans may allow an attacker to access users’ personal information such as banking information, passwords, or personal identity. It can also delete a user’s files or infect other devices connected to the network.
Unlike computer viruses, worms, and rogue security software, Trojans generally do not attempt to inject themselves into other files or otherwise propagate themselves.
4. Ransomware
Ransomware is malicious software that infects your computer and displays messages demanding a fee to be paid in order for your system to work again.
This class of malware is a criminal money making scheme that can be installed through deceptive links in an email message, instant message, or website. It has the ability to lock a computer screen or encrypt important predetermined files with a password.
5. Fileless Malware
Fileless malware is a variant of computer-related malicious software that exists exclusively as a computer memory-based artifact i.e., in RAM.
It does not write any part of its activity to the computers’ hard drive meaning that it’s very resistant to existing anti-computer forensic strategies that incorporate file-based whitelisting, signature detection, hardware verification, pattern -analysis, time-stamping, etc., and leaves very little by way of evidence that could be used by digital forensic investigators to identify illegitimate activity.
A malware of this type is designed to work in-memory, its longevity on the system exists only until the system is rebooted.
6. Adware
Adware tracks a user’s surfing activity to determine which ads to serve them. Although adware is similar to spyware, it does not install any software on a user’s computer, nor does it capture keystrokes.
The danger in adware is the erosion of a user’s privacy. — it captures the data about the user’s activity elsewhere on the internet and uses it to create a profile of that person which includes who their friends are, what they’ve purchased, where they’ve traveled, and more. That information can be shared or sold to advertisers without the user’s consent.
7. Spyware
Spyware is a broad category of malware designed to secretly observe activity on a device and send those observations to a snooper. That data can be used to track your activity online and that information can be sold to marketers.
Spyware can also be used to steal personal information, such as account passwords and credit card numbers, which can result in identity theft and fraud.
8. Rootkit
A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or an area of its software that is not otherwise allowed (for example, to an unauthorized user) and often masks its existence or the existence of other software.
The term rootkit is a compound of “root” (the traditional name of the privileged account on Unix-like operating systems) and the word “kit” (which refers to the software components that implement the tool). The term “rootkit” has negative connotations through its association with malware.
Rootkit installation can be automated, or an attacker can install it after having obtained root or Administrator access. Obtaining this access is a result of a direct attack on a system, i.e. exploiting a known vulnerability (such as privilege escalation) or a password (obtained by cracking or social engineering tactics like “phishing”).
Once installed, it becomes possible to hide the intrusion as well as to maintain privileged access. Full control over a system means that existing software can be modified, including software that might otherwise be used to detect or circumvent it.
Rootkit detection is difficult because a rootkit may be able to subvert the software that is intended to find it. Detection methods include using an alternative and trusted operating system, behavioral-based methods, signature scanning, difference scanning, and memory dump analysis.
9. Keylogger
Keyloggers are a type of monitoring software designed to record keystrokes made by a user. These keystroke loggers record the information you type into a website or application and send it back to a third party.
Criminals use keyloggers to steal information or financial information such as banking details, which they can then sell or use for profit. Law enforcement and intelligence agencies also use keylogging for surveillance purposes.
10. Bots/Botnets
A bot is a computer that has been compromised through a malware infection and can be remotely controlled by a cybercriminal. A botnet is a short form of “robot network”. The cybercriminal can then use the bot (also known as a zombie computer) to launch more attacks or to bring it into a collection of controlled computers, known as botnets.
These bots were originally designed to run as a user in the various chat rooms. They could proctor a room, booting out people who used foul language, or involved in other such activities.
The two main reasons why cybercriminals create botnets are for financial gains and/or for recognition.
11. Grayware
Grayware, also referred to as spyware, is any files or applications that can be detrimental to a computer’s performance and/or compromise its security. This can include keystroke loggers that can steal sensitive information for nefarious purposes.
Oftentimes, grayware is included as part of legitimate software installation packages and activated when the files are installed and the program is activated. The End User License Agreement (EULA) often has terms in it that explain how one’s data will be used, but most people don’t read it because of the length and legal technicality of EULAs.
Other grayware programs include programs that decipher passwords, hack computers to gain entry, remotely access computers to control them, change Internet settings to call pre-configured phone numbers with high charge rates, and adware.
12. Malwaretising
Malvertising (malicious advertising) is the use of online advertising to spread malware. It typically involves injecting malicious or malware-laden advertisements into legitimate online advertising networks and webpages.
Online advertisements provide a solid platform for spreading malware because the significant effort is put into them in order to attract users and sell or advertise the product. Because advertising content can be inserted into a high-profile and reputable website, malvertising provides malefactors an opportunity to push their attacks to web users who might not otherwise see the ads, due to firewalls, or the like.
Malvertising is attractive to attackers because it can be easily spread across a large number of legitimate websites without directly compromising those websites.
13. Backdoor
A backdoor is a typically covert method of bypassing normal authentication or encryption in a computer, product, embedded device (e.g., a home router), or its embodiment (e.g., part of a cryptosystem, algorithm chipset, etc.).
Backdoors are most often used for securing remote access to a computer or obtaining access to plain text in cryptographic systems. From there it may be used to gain access to privileged information like passwords, corrupt or delete data on hard drives, or transfer information within auto schematic networks.
A backdoor may take the form of a hidden part of a program, a separate program code in the firmware of the hardware, or parts of an operating system such as Windows.
Although some are secretly installed, other backdoors are deliberate and widely known. These kinds of backdoors have “legitimate” uses such as providing the manufacturer with a way to restore passwords.
14. Browser Hijacker
It is a form of unwanted software that modifies a web browser’s settings without a user’s permission, to inject unwanted advertising into the user’s browser. A browser hijacker may replace the existing home page, error page, or search engine with its own.
These are generally used to force hits to a particular website, increasing advertising revenue.
Some browser hijackers also contain spyware, for example, some install a software keylogger to gather information such as banking and e-mail authentication details. Some browser hijackers can also damage the registry on Windows systems, often permanently.
There are several methods that browser hijackers use to gain entry to an operating system. Email attachments and files downloaded through suspicious websites and torrents are common tactics that browser hijackers use.
15. Crimeware
Crimeware is a class of malware designed specifically to automate cybercrime.
Crimeware (as distinct from spyware and adware) is designed to perpetrate identity theft through social engineering or technical stealth in order to access a computer user’s financial and retail accounts for the purpose of taking funds from those accounts or completing unauthorized transactions that enrich the cyberthief.
Alternatively, crimeware may steal confidential or sensitive corporate information. Crimeware represents a growing problem in network security as many malicious code threats seek to pilfer confidential information.
16. RAM Scraper
A malicious program that scans the RAM of infected devices (usually POS terminals) to steal confidential data. Most often, memory scrapers are on the prowl for bank card numbers and PIN codes. Only cards with magnetic strips are vulnerable. EMV chips are protected from this type of attack.
17. Rogue Security Software
Rogue security software is a form of malware that’s designed to trick victims into thinking their computer or device has been infected with a virus. Like legitimate antivirus products, it displays pop-up messages telling the victim that her or his computer or device has been infected with a virus. With rogue security software, however, there is no virus present.
If your computer or device is infected with rogue security software, it could cost you a substantial amount of money — assuming you fall for the trap. Rogue security software typically doesn’t steal data. Instead, it’s designed to trick you into paying for a fake removal service. After displaying a fake virus message, the software will contain instructions on how to clean your computer or device. Normally, the rogue security software will ask you to pay for a premium virus removal service or tool.
Like with ransomware, though, there’s no guarantee that paying the requested sum of money will remove the rogue security software. After making payment, the rogue security software may ask you to pay for an additional service or tool.
18. Cryptojacking
Cryptojacking is the unauthorized use of someone else’s computer to mine cryptocurrency. Hackers do this by either getting the victim to click on a malicious link in an email that loads cryptomining code on the computer, or by infecting a website or online ad with JavaScript code that auto-executes once loaded in the victim’s browser.
Either way, the cryptomining code then works in the background as unsuspecting victims use their computers normally. The only sign they might notice is slower performance or lags in execution.
19. Logic Bomb
A logic bomb is a piece of code intentionally inserted into a software system that will set off a malicious function when specified conditions are met. For example, a programmer may hide a piece of code that starts deleting files (such as a salary database trigger), should they ever be terminated from the company.
Software that is inherently malicious, such as viruses and worms, often contain logic bombs that execute a certain payload at a pre-defined time or when some other condition is met. This technique can be used by a virus or worm to gain momentum and spread before being noticed. Some viruses attack their host systems on specific dates, such as Friday the 13th or April Fools’ Day. Trojans and other computer viruses that activate on certain dates are often called “time bombs”.
To be considered a logic bomb, the payload should be unwanted and unknown to the user of the software. As an example, trial programs with code that disables certain functionality after a set time are not normally regarded as logic bombs.
20. Hybrids and Exotic Forms
Apart from these, nowadays hybrids and exotic forms which are a combination of two or more of the above also exist.
How Malware Spreads?
There are six common ways that malware spreads:
- Vulnerabilities: A security defect in software allows the malware to exploit it to gain unauthorized access to the computer, hardware, or network.
- Backdoors: An intended or unintended in software, hardware, networks, or system security.
- Drive-by Downloads: Unintended download of software with or without knowledge of the end-user.
- Homogeneity: If all systems are running the same operating system and connected to the same network, the risk of a successful worm spreading to other computers increases.
- Privilege Escalation: A situation where an attacker gets escalated access to a computer or network and then uses it to mount an attack.
- Blended Threats: Malware packages that combine characteristics from multiple types of malware making them harder to detect and stop because they can exploit different vulnerabilities.
Image Credit: Computer vector created by vectorjuice – www.freepik.com
You May Also Like

Best Lunchboxes for Students
Table of Contents Evaluation CriteriaBest Lunchboxes for Students1. Single Compartment Lunch Box2.

Best Useful Notebooks for Your Writing Needs
Table of Contents Best Notebooks For Your Writing Needs1. Bullet Journals2. Case-Bound

Best Useful Erasers for Your Drawing Needs
Table of Contents The Best Erasers1. Click or Stick Eraser2. Coloured Pencil