Frequently Asked Questions
What is a word search?
A word search is a puzzle where there are rows of letters placed in the shape of a square, and there are words written forwards, backwards, horizontal, vertical or diagonal. There will be a list of words for the player to look for and the goal of the player is to find those words hidden in the word search puzzle, and highlight them.
How do I choose the words to use in my word search?
Once you’ve picked a theme, choose words that have a variety of different lengths, difficulty levels and letters. You don’t need to worry about trying to fit the words together with each other because WordMint will do that for you!
How are word searches used in the classroom?
Word search games are an excellent tool for teachers, and an excellent resource for students. They help to encourage wider vocabulary, as well as testing cognitive abilities and pattern-finding skills.
Because the word search templates are completely custom, you can create suitable word searches for children in kindergarten, all the way up to college students.
Who is a word search suitable for?
One of the common word search faq’s is whether there is an age limit or what age kids can start doing word searches. The fantastic thing about word search exercises is, they are completely flexible for whatever age or reading level you need.
Word searches can use any word you like, big or small, so there are literally countless combinations that you can create for templates. It is easy to customise the template to the age or learning level of your students.
How do I create a word search template?
For the easiest word search templates, WordMint is the way to go!
Pre-made templates
For a quick an easy pre-made template, simply search through WordMint’s existing 500,000+ templates. With so many to choose from, you’re bound to find the right one for you!
Create your own from scratch
- Log in to your account (it’s free to join!)
- Head to ‘My Puzzles’
- Click ‘Create New Puzzle’ and select ‘Word Search’
- Select your layout, enter your title and your chosen words
- That’s it! The template builder will create your word search template for you and you can save it to your account, export as a Word document or PDF and print!
How can I print my word search template?
All of our templates can be exported into Microsoft Word to easily print, or you can save your work as a PDF to print for the entire class. Your puzzles get saved into your account for easy access and printing in the future, so you don’t need to worry about saving them at work or at home!
Can I create a word search in other languages?
Word searches are a fantastic resource for students learning a foreign language as it tests their reading comprehension skills in a fun, engaging way.
We have full support for word search templates in Spanish, French and Japanese with diacritics including over 100,000 images.
Since the PC industry started in the 1970’s, hackers have created viruses to attack them and cause damage. These threats have been created for various reasons, ranging from financial gain to a simple challenge for the hacker. Here is a list of prevalent system threats over the past 50 years.
| Virus name | Date(s) | Type | How It Infects | Typical Damage Caused | |
| Creeper | 1971 | Experimental self-replicating TENEX operating system Worm | Gained access using the ARPANET | Displayed the message “I’m the creeper, catch me if you can!” | |
| Rabbit | 1974 | Fork bomb denial-of-service attack | Uses the fork system call, and can fork endlessly | Makes multiple copies of itself on a single computer until it clogs the system, reducing system performance. This finally reaches a threshold and crashes the computer. | |
| Elk Cloner | 1982 | Apple II virus | The first virus observed “in the wild.” It displayed a message but caused very little damage. | ||
| Brain | 1986 | MS-DOS computer virus | Floppy disk or diskette | The virus slows down the floppy disk drive and makes seven kilobytes of memory unavailable to DOS. | |
| Vienna | 1987 | Computer virus | Floppy disk or diskette DOS .com-infecting virus | Causes a warm reboot when the program is run. | |
| Lehigh | 1987 | Computer virus | DOS virus that infects via floppy disk or diskette | After 4 infections, it overwrites the boot sector and file allocation table. | |
| Stoned | 1987 | Boot sector virus family | It only infects 360 kilobyte 5.25 inch floppies and hard drives | The infected computer will beep and display the message “Your PC is now stoned! LEGALIZE MARIJUANA!” Any files with directory entries on that sector will be lost. It can also cause the disk’s FAT to be corrupted. | |
| Cascade | 1987 | Computer virus | Floppy disk or diskette | It causes a “falling letters” effect on the screen, and may also cause some noise. | |
| Jerusalem | 1987 | DOS file infector virus | Floppy disk or diskette | It infects DOS.EXE files. Delivers two payloads, one that is annoying but relatively harmless and the other destructive. The non-destructive one creates a ‘black window’ on the screen. Then the system slows down due to a time-wasting loop installed on each timer interrupt. The destructive payload activates on any Friday the 13th, deleting any program run on that day. Sometimes this causes the files to consume all available storage space. | |
| SCA | 1987 | Amiga boot sector virus | 3.5 and 5.25-inch floppy disk or diskette | ||
| Christmas Tree | 1987 | Mass-mailing worm | Email with the subject line “Let this exec run and enjoy yourself!” The user must execute the program by typing “christma” or “christmas.” | Paralyses a network when executed and displays an ASCII Christmas tree. It then reads the files “NAMES,” “NETLOG,” and files containing the addresses of communication partners. It emails itself to every address in these files. | |
| MacMag | 1987 | Classic Mac OS computer virus | Compuserve forum | Infects any disks inserted into the computer. Replicates until 3/2/1988, when it displays a message from MacMag and then deletes itself. | |
| nVIR | 1987 | Classic Mac OS computer virus | Floppy disk, diskette, or a network | Crashes or slows a system and causes printing errors. | |
| SCA | 1987 | Amiga Boot sector virus | Floppy disk or diskette | Displays a message on the screen, but is mostly harmless. May destroy a legitimate non-standard boot block. | |
| Morris Worm | 1988 | Computer worm | Exploits security flaws in Unix systems | Launches denial of service attacks. | |
| Ping Pong | 1988 | DOS boot sector virus | Floppy disk or diskette | Harmless to most computers. Shows a small “ball” bouncing around the screen in both text mode (the ASCII bullet character “•”) and graphical mode. Systems may crash during the ball’s appearance on the screen. | |
| Byte Bandit | 1988 | Amiga boot sector virus | 3.5 and 5.25-inch floppy disk or diskette | It causes the screen to go black. | |
| Scores | 1988 | Classic Mac OS computer virus | Floppy disk or diskette | Infects the System, Scrapbook, and Notepad files that are run and crashes programs. | |
| Swap | 1989 | Boot sector virus | Floppy disk or diskette | It causes “falling letters” effect and may also cause some noise. infects any diskette that is inserted into the system | |
| Ghostball | 1989 | Multipartite computer virus | Floppy disk or diskette | Drops a copy of the Pingpong virus on diskettes. | |
| AIDS | 1989 | Trojan, ransomware | Email lists | Displays a notice asking for $189 to be sent to a post office box in Panama to get a decryption program. | |
| Alabama | 1989 | DOS computer virus | Infects .EXE files. Files infected increase in size by 1,560 bytes. Displays message 1 hour after execution. | ||
| ANTI | 1989 | Classic Mac OS computer virus | The first Mac OS virus not to create additional resources. It only patches existing CODE resources. Causes small overall effects. | ||
| Lamer Exterminator | 1989 | Amiga boot sector virus | Storage media | Writes bootblocks 84 times with the “LAMER!” string. | |
| SevenDust | 1989 | Classic Mac OS polymorphic virus | Various storage media | Deletes non-application files. | |
| WDEF | 1989 | Classic Mac OS computer virus | Floppy disk or diskette | ||
| Form | 1990 | DOS boot sector virus | Floppy disk or diskette | It causes clicking noises and severe data damage. It will infect any media inserted into the machine. | |
| 1260 | 1990 | DOS polymorphic virus | Floppy disk or diskette | Infects DOS executable files. | |
| 4K | 1990 | DOS virus | Floppy disk or diskette | Infected systems will hang on September 22 of each year, which is also the date of birth of Bilbo Baggins. | |
| AIDS | 1990 | DOS virus | AIDS is the first virus known to exploit the DOS “corresponding file” vulnerability. | ||
| AIDS II | 1990 | DOS virus | Targets .EXE files. Displays message and plays a song. | ||
| Ambulance | 1990 | DOS virus | Infects .EXE files. | ||
| CDEF | 1990 | Classic Mac OS Computer virus | Floppy disk or diskette | Infects application and system files. It causes various levels of damage. | |
| MDEF | 1990 | Classic Mac OS Computer virus | Storage Media | Infects menu definition resource fork files. | |
| Ontario | 1990 | DOS file infector virus | Floppy disk or diskette | Infects .COM, .EXE. and .OVL files. Increases file size by 512 bytes, 1023 bytes. Corrupts the hard drive over time. | |
| Scott’s Valley | 1990 | DOS file infector virus | Floppy disk or diskette | Infects .COM and .EXE files. Causes system slowdown. | |
| Whale | 1990 | DOS Polymorphic virus | Floppy disk or diskette | Infects .COM, .EXE files. Simulates rebooting a system. May display the message: “THE WHALE IN SEARCH OF THE 8 FISH I AM ‘~knzyvo}’ IN HAMBURG address error D9EB,02.” It also causes a system slow down. |
|
| Zuc | 1990 | Classic Mac OS computer virus | Storage media, internet, or a network | ||
| Michelangelo | 1991 | DOS boot sector virus | Floppy disk or diskette | Overwrites all data on the hard disk with random characters. Infects sector 28 on 1.2-megabyte floppy disks. Ran on March 6th, Michelangelo’s birthday. Makes data irretrievable by the user. | |
| Ada | 1991 | DOS virus | Targets .COM files, usually COMMAND.COM. Beeps from system speaker, hangs the system, shows “Disk full” error. | ||
| Eliza | 1991 | DOS virus | Infects .COM and .EXE files. Low-level threat. | ||
| Koko | 1991 | DOS virus | Storage media | Payload activates on July 29 and February 15. It can erase data on the user’s hard drive. Displays a message. | |
| Ontario.1024 | 1991 | DOS file infector virus | Floppy disk or diskette | Infects files and corrupts hard drives over time. | |
| Freddy Krueger | 1992 | Memory resident infector | Diskettes or connected computer | Deletes infected files. It will also infect any program run by the user. | |
| Bomber | 1992 | DOS polymorphic memory-resident computer virus | Diskettes or connected computer | Works via a “patchy infection” technique. The beginning of the virus code contains the unencrypted text: COMMANDER BOMBER WAS HERE. | |
| 5lo | 1992 | DOS computer virus | Infects .EXE files only. Total free system memory will decrease by 2K. | ||
| Acid | 1992 | DOS, Windows 95, 98 virus |
Inserted storage media | Infects COM file, and .EXE files. Disk directory listing will not be altered. Programs have the first 792 bytes overwritten with Acid’s own code. | |
| Acme | 1992 | DOS, Windows 95 virus |
Infects another .EXE in the current directory by making a hidden .COM file with the same base name. | ||
| ABC | 1992 | DOS Computer virus | It causes keystrokes on the infected computer to be repeated. | ||
| ARCV-n | 1992 | DOS Computer virus | Infects .COM and .EXE files. Displays text messages. | ||
| INIT 1984 | 1992 | Classic Mac OS computer virus | Storage media, email, internet connection | Triggered at bootup on Friday the 13th. Infects startup INIT files. Changes file names to random strings. It has a low threat level. | |
| Ontario.2048 | 1992 | DOS file infector virus | Floppy disk or diskette | Infects files and corrupts hard drives over time. | |
| Abraxas | 1993 | DOS, Windows 95, 98 virus |
Infects COM file. Overwrites files, displays “ABRAXAS” in ASCII art and plays a series of sounds. | ||
| OneHalf | 1994 | Polymorphic DOS boot virus | Diskettes or connected computer | Will display the message: “Dis is one half…..Press any key to continue …” | |
| Natas | 1994 | DOS multipartite, stealth, polymorphic virus | Floppy disk or diskette | Affects .COM and .EXE files. | |
| SMEG engine | 1994 | DOS polymorphic virus engine | Creates other viruses. | ||
| Concept | 1995 | Macro virus for MS Word | CD’s released by some major corporations. Email mass mailings | Affects MS Word documents. | |
| Bizatch | 1995 | MS Windows 95 virus | CD’s, diskettes or connected computer | On the 31st of any month, it displays a message box praising the VLAD group and listing the current members of VLAD. | |
| Hare | 1995 | DOS, Windows 95, Windows 98 virus |
Storage media, email, internet connection | Infects .COM and .EXE files, master boot record of hard disks, and boot sector of floppy disks. Activates on August 22 and September 22. Erases hard disk and displays the message: “HDEuthanasia by Demon Emperor.” | |
| Ply | 1996 | DOS non-encrypted polymorphic virus | CD’s, diskettes or connected computer | Infects all .exe files it finds. | |
| Laroux | 1996 | Microsoft Excel virus | CD’s, diskettes or connected computer | Adds the Excel macro “laroux” to PERSONAL.XLS. The virus will then infect any Excel workbook available. | |
| Staog | 1996 | Linux virus | CD’s, diskettes or connected computer | Never been wild, and had no destructive payload. No damage caused. | |
| Alcon | 1997 | DOS computer virus | Overwrites random files on a disk causing damage over time. | ||
| Esperanto | 1997 | DOS, MS Windows, classic Mac OS, multi-processor virus. | Storage media, email, internet connection | Infects .COM and .EXE files. Runs when computer is started. Displays a message on 26 of July. | |
| CIH | 1998 | File virus | Pirated software, a “PWA-cracked copy” of Windows 98 | Makes it impossible to boot from the hard drive. It may be impossible to recover some of the lost data. Nothing may be displayed when the user starts the computer. The virus can only spread on Windows 95, 98 and ME systems. | |
| Happy99 | 1999 | Email / newsgroup worm | Email or news post with attachment named “Happy99.exe” | No destructive payload and never caused any damage. | |
| ExploreZip | 1999 | Mass-mailer worm | Email mass mailings | Destroys certain files, disrupts email systems. | |
| CTX | 1999 | Computer virus | Spreads via the Cholera worm | Overwrites parts of .exe files. | |
| Kak | 1999 | JavaScript worm | Uses a bug in Outlook Express to spread itself | Uses SHUTDOWN.EXE to initiate a shutdown and show a popup with the text “Kagou-anti-Kro$oft says not today!” A minimized window appears on startup with the title “Driver Memory Error.” Another message may pop up saying “S3 Driver Memory Alloc Failed!” This happens on day 1 of each month at 6:00 pm. | |
| Marker | 1999 | MS Word Polymorphic, Macro virus | Internet, various storage media | Infects Word Documents. Keeps a log of infected computers. | |
| Pikachu | 2000 | Email worm | An email arrives titled “Pikachu Pokemon” and the body of the e-mail includes the text “Pikachu is your friend.” | Adds the lines “del C:WINDOWS” and “del C:WINDOWSsystem32” to the file “autoexec.bat.” Commands would be executed at the next boot, attempting to delete two critical directories of the Windows operating system. However, users would be given a prompt asking whether or not they wanted to delete those folders. | |
| Navidad | 2000 | Windows mass-mailer worm | Displays messages in Spanish and makes the system unusable. Spreads further through email clients. Adds NAVIDAD.EXE as an attachment. Adds an icon in the system tray. | ||
| Anna Kournikova | 2001 | Computer worm | Email with an attachment .jpeg image that automatically sends itself to all contacts in a user’s Windows Address Book. | Caused problems in email servers due to the quantity spread. No other real damage. | |
| Klez | 2001 | Computer worm | E-mail message, spoofing. Sends itself to people in users’ address books. | Could render a victim’s computer inoperable. It could even disable virus-scanning software and pose as a virus-removal tool. | |
| Nimda | 2001 | Computer worm | Email. open network shares, back doors, and compromised websites. | Brings internet traffic to a crawl. | |
| Sadmind | 2001 | Computer worm | Network, email, CD, or diskette. | Exploits vulnerabilities in both Sun Microsystems’ Solaris and Microsoft’s Internet Information Services. | |
| Sircam | 2001 | Mass-mailer worm | Emailed out to email addresses in the host’s address book. It could also spread via open shares on a network. | Personal or private files were emailed to people who otherwise should not have received them. | |
| ZMist | 2001 | Windows metamorphic virus | Storage media, internet, or a network. | Requires 32 MB of memory. Decompiles portable .EXE files. | |
| Beast | 2002 | Trojan horse | Used the client-server model. The server is what would infect the victim’s computer. | It gave the attacker complete control over the infected computer. Infected other applications as well. | |
| Mylife | 2002 | Mass-mailer worm | Emails to all contacts in Microsoft Outlook. | Affected home users mostly. | |
| Simile | 2002 | Windows metamorphic virus | Internet, various storage media. | Displays a message, “Free Palestine!” and infects .EXE files. | |
| SQL Slammer | 2003 | Computer worm | Affected Microsoft’s SQL Server and Desktop Engine database products. | Launched denial of service attacks. Dramatically slowed down general Internet traffic. | |
| Graybird | 2003 | Trojan horse | Email, CD, diskette, USB ports, or internet connection. | Downloads files from remote web sites, records keystrokes, extracts passwords, and steals PC information. | |
| ProRat | 2003 | Trojan horse | Via a network, it uses a client and a server. | Logs keystrokes, steals passwords and gains full control over files. | |
| Blaster worm | 2003 | Computer worm | Email, CD, diskette, USB ports | Displays in Windows the following message and then automatically reboots, usually after 60 seconds: “This system is shutting down. Please save all work in progress and log off. Any unsaved changes will be lost.” | |
| Welchia | 2003 | Computer worm | Email, CD, diskette, USB ports | Floods a network, installs its own Microsoft patches. | |
| Sobig | 2003 | Computer worm | Emails with the sender address “big@boss.com” | Used as a backdoor for spammers to mass email. | |
| Swen | 2003 | Mass-mailing computer worm | Microsoft Security update, email, Internet Relay Chat, Kazaa filesharing, and newsgroups. | Tries to shut off antivirus programs and firewalls. | |
| Sober | 2003 | Computer worm | E-mail attachment, fake webpages, fake pop-up ads, and fake advertisements. | Copies itself to one of several files in the Windows directory. Adds appropriate keys to the Windows registry and can e-mail itself to all addresses in a user’s e-mail address book. | |
| Agobot | 2003 | Computer worm | Email, CD, diskette, USB ports | Perform denial-of-service attacks, steal data, send spam, and allows the attacker to access the device and its connection. | |
| Bolgimo | 2003 | Win32 computer worm | Windows patch | Downloads the patch to the user’s desktop and run the patch installer. | |
| Sasser | 2004 | Windows worm | Exploits buffer overflow vulnerability in Local Security Authority Subsystem Service (LSASS) | Slows down and crashes the computer, while making it hard to reset without cutting the power. | |
| Mydoom | 2004 | Windows worm | Appears as an email transmission error. Spreads through email address books. | Creates a backdoor that allows remote access. Launches denial of service attacks. | |
| Sasser | 2004 | Virus | Spread by email and social engineering | It causes system crashes and resource usage. | |
| Bagle | 2004 | Mass-mailing worm | Mass-email as an attachment | It is a botnet causing e-mail spam. | |
| Netsky | 2004 | Computer worm | E-mail, social engineering tactics. | Scans the computer for e-mail addresses and e-mails itself to all addresses found. | |
| Witty | 2004 | Computer worm | Via hosts connected to the internet. | Attacks firewalls and other computer security products written by specific companies. | |
| Caribe | 2004 | Computer worm | Mobile phones running Symbian OS, and through Bluetooth wireless signals. | Displays the message “Caribe” on the phone’s screen, and is displayed every time the phone is turned on. The worm then attempts to spread to other phones in the area. | |
| Vundo | 2004 | Trojan horse | E-mail attachment carrying a trojan, browser exploits, and browser plug-ins. | It causes popups and advertising for rogue antispyware programs, performance degradation, and denial of service with some websites. | |
| Santy | 2004 | Computer worm | Uses Google to spread across the Internet. | Infected servers and displayed the message “This site is defaced!!! This site is defaced!!! NeverEverNoSanity WebWorm generation X.” X is a number of the generation of the worm. | |
| Zotob | 2005 | Internet worm | Plug-and-play | Makes an infected computer a part of a botnet. | |
| Copy protection rootkit | 2005 | Rootkit | Included on music CDs sold by Sony BMG. | Creates vulnerabilities on affected computers, making them susceptible to infection by worms and viruses. | |
| Zlob | 2005 | Malware Trojan downloader | Disguised as a needed video codec in the form of ActiveX. | Random computer shutdowns or reboots showing random comments. Runs a file called “zlberfker.exe.” Redirects to porn sites and various video watching sites that show a number of inline videos. Playing the video activates a request to download an ActiveX codec that is malware. It prevents the user from closing the browser in a normal way. | |
| Nyxem | 2006 | Internet worm | Infected email attachments and network shares. | The virus removes antivirus programs from remote computers before attempting to infect them. It activates on the third day of each month. On activation, the virus overwrites data files of many common types, including Word, Excel, and PowerPoint documents; ZIP and RAR archives; and PDFs. It can destroy files on fixed and removable drives and tries but fails, to affect data on network drives. It also attempts to disable antivirus programs or deletes the antivirus programs directly. | |
| Brontok | 2006 | Mass-email worm | It arrives as an attachment to an e-mail named “kangen.exe.” | Reboots the computer. Blanks out address typed in Windows Explorer before completion. Sends itself to email addresses it finds on the computer, even faking the own user’s email address as the sender. The computer also restarts when trying to open the Windows Command Prompt. Prevents the user from downloading files. It also opens the default Web browser and loads a web page which is located in the “My Pictures” folder. | |
| Stration | 2006 | Mass-mailer worm | Disables security features, sends itself to other computers via e-mail attachments. | ||
| Kama Sutra | 2006 | Windows computer worm | Destroys common files, such as .doc, .pdf, .zip, .xls and disables antivirus software. | ||
| Oompa | 2006 | Mac OS X worm | iChat message attachment | Displays a message. Marks other files. | |
| RavMonE.exe | 2006 | Trojan horse worm | iPod videos, removeable storage drives, email attachments, internet files. | Allows unauthorized access to a computer. | |
| Storm | 2007 | Trojan horse worm | Used the click bait headline “230 dead as storm batters Europe” which accompanied a link to the “story.” | Turns computers into bots that re-distribute the email. | |
| Alureon | 2007 | Botnet trojan | Manual download, rogue software bundle | Steals data through network traffic, blocks Task Manager and desktop, Windows Update, disables antivirus programs. It also redirects search engines to fraud sites. | |
| Conficker | 2008 | Windows worm | Uses flaws in the OS to create a botnet. | Installs software that will turn the computer into a botnet slave. Includes scareware to obtain money from users. | |
| Mocmex | 2008 | Trojan horse | Digital photo frame | Collects passwords for online games, recognizes and blocks antivirus protection. | |
| Torpig | 2008 | Botnet | Trojan horses, emails | Collects sensitive personal and corporate data such as bank accounts and credit card information. | |
| Bohmini.A | 2008 | Trojan horse | Malvertising via the social networking site Facebook. | Turns the computer into a bot or remotely controls it. | |
| Fun | 2008 | Windows virus | Email attachment | Sends email with attachments as a response to any unopened emails in Outlook Express. | |
| Zeus | 2009 | Trojan horse | Drive-by downloads or phishing scams | Endangers FTP accounts and computers. Theft of login credentials. Performs various criminal tasks, usually man-in-the-browser keylogging and form grabbing. | |
| Daprosy | 2009 | Trojan worm | Local area network (LAN) connections, spammed e-mails, USB mass storage devices. | Steals online-game passwords in internet cafes. | |
| MegaPanzer | 2009 | Trojan horse | Network and internet connections | Intercepts Skype and voice over IP traffic on Windows XP systems. | |
| Kenzero | 2009 | Computer virus | Online via peer-to-peer networks (P2P) | Monitors the browsing history of users. | |
| Stuxnet | 2010 | Computer worm | Via an infected USB flash drive | Used in cyberwarfare. Affected Iran’s nuclear program. | |
| Waledac | 2010 | Mass-mailer worm | Email mass- mailings | Sends spam emails and malware, harvests password info. | |
| Psyb0t | 2010 | Computer worm | Routers and high-speed modems. | Affects data and internet traffic flow. | |
| here you have | 2010 | Trojan horse | Sends a copy of itself to everyone in the Windows Address Book, Microsoft Outlook address book and delivers a payload. | ||
| SpyEye | 2011 | Malware | Attacks web browsers on Windows PCs. | Uses keystroke logging and form grabbing to steal user credentials for malicious use. | |
| Anti-Spyware 2011 | 2011 | Trojan horse | Poses as an anti-spyware program. | Disables security-related processes of anti-virus programs, blocks access to the Internet, and prevents updates. | |
| ZeroAccess | 2011 | Trojan horse | Malvertising, affiliate scheme. | Downloads other malware on an infected machine from a botnet while remaining hidden using rootkit techniques. | |
| Duqu | 2011 | Computer worm | Microsoft Word document | It looks for information that could be useful in attacking industrial control systems. | |
| Flame | 2012 | Malware | LAN or USB | Records keyboard activity, network activity, screenshots, and skype conversations. | |
| Shamoon | 2012 | Computer virus | Spreads using a network. | Overwrites the master boot record of the infected computer, making it unusable. | |
| NGRBot | 2012 | Computer worm | IRC network for file transfer. | Steals user information, infects HTML pages, blocks security updates, monitors network activity. | |
| CryptoLocker | 2013 | Trojan horse | Infected email attachments, Gameover Zeus botnet. | Encrypts files on a user’s hard drive, then prompts them to pay a ransom to the developer in order to receive the decryption key. | |
| Gameover ZeuS | 2013 | Peer-to-peer botnet | Through use of the Cutwail botnet. | Steals users’ login details on popular web sites that involve monetary transactions. Used for banking fraud and distribution of the CryptoLocker ransomware. | |
| Linux.Darlloz | 2013 | Computer worm | Internet of things, PHP vulnerability. | Infects routers, security cameras, set-top boxes. | |
| Regin | 2014 | Trojan horse | Spoofed web pages | Downloads extensions of itself, making it difficult to be detected via anti-virus signatures. Used as a tool for espionage and mass surveillance. | |
| BASHLITE | 2015 | Linux malware | Local network | Launch distributed denial-of-service attacks. | |
| MEMZ | 2016 | Trojan horse | Internet | Moves the mouse cursor slightly, opens up humorous Google searches on the user’s web browser, and opens various random Microsoft Windows programs. | |
| Locky | 2016 | Ransomware malware | Email, exploit kits, Word and Excel attachments with malicious macros, DOCM attachments, and zipped JS Attachments. | Demands a payment of between 0.5 and 1 bitcoin that victims must pay to decrypt their files. | |
| Tiny Banker | 2016 | Trojan malware | Networks | Man-in-the-browser attacks and network sniffing. | |
| Mirai | 2016 | Botnet malware | Internet, online consumer devices. | DDoS attacks infecting the Internet of Things. | |
| Mirai | 2016 | Linux Malware | Hacker forums as open-source. | Turns Linux system into a bot for a botnet. Launches Internet of Things Denial of service attacks. | |
| Petya | 2017 | Trojan ransomware | Fake job emails. | Destroys user data. | |
| Xafecopy | 2017 | Trojan horse | Mobile payments on websites. | Charges the user’s mobile carrier bill and subscribes to unwanted paid services. | |
| Wannacry | 2017 | Ransomware | SMB port | Charges ransom of $300 to undo. | |
| Xafecopy | 2017 | Android Trojan | Downloadable apps, battery optimizers. | Clicks on web pages to subscribe that charge money to the user’s phone bill. | |
| Thanatos | 2018 | Ransomware | Deceptive advertising | Charges a $200 USD ransom payment to one of the listed Bitcoin, Ethereum, or Bitcoin Cash addresses. | |
| Titanium | 2019 | Trojan horse | Internet | Remains undetected, steals, and spies on user. | |
| AntiCMOS | 1994-1995 | DOS computer virus | Due to a faulty virus code, it will not erase CMOS information as designed. | ||
| Melissa | 1999-present | Microsoft Word macro virus | Mass email. Primarily affects Microsoft Word and Outlook-based systems. | Mass mails itself using contact lists. Disables safeguard features on Microsoft Outlook and Microsoft Word. | |
| ILOVEYOU | 2000-present | Computer worm | Email messages and mailing lists. | Overwrites files, sends itself to all addresses in the Microsoft Outlook address book. | |
| Code Red | 2001-present | Computer worm | Targets Microsoft IIS web server buffer overflow workflow issue. | Eats up system resources, launches denial of service attacks, and leaves the message: “Hacked By Chinese!” | |
| Code Red 2 | 2001-present | Computer worm | Exploits a security hole in Microsoft’s Internet Information Server (IIS) webserver software. | Creates a backdoor that allows further attacks. | |
| Bifrost | 2004-present | Backdoor Trojan horse | Server client | Remote user can execute arbitrary code at will on the compromised computer. Some file attributes changed to “Read Only” and “Hidden.” | |
| Rustock | 2006-2011 | Botnet | Trojan horses, emails | Sends spam messages with trojan horses and incorporates machines into the botnet. | |
| Koobface | 2008-2010 | Computer worm | Spread via infected social media posts. | Targets mostly Facebook. It gets users to download malware. | |
| CryptoLocker | 2013-2014 | Trojan horse ransomware | Various ways including email | Users must pay a ransom to undo by a certain deadline. | |
| Commwarrior | Symbian Bluetooth worm | Bluetooth and MMS | Spreads through MMS and Bluetooth to other devices. Little damage caused. |
This list represents a large portion of known computer viruses over the past 50 years that have attacked PC’s and devices around the world. The process of virus creation is not slowing down, so having strong antivirus software installed on your system is crucial to protecting it from any future attacks.
Эксперты в сфере кибербезопасности обнаружили новый тип вирусов, которые заражают персональные компьютеры без наличия макросов. Вредоносные программы проникают в устройства пользователей с помощью документов Microsoft Office.
По мнению специалистов портала ARStechnica, злоумышленники применяют технологию Dynamic Data Exchange. С её помощью текстовые документы используются для выполнения кода, который скрывается в других файлах.
- Как вирусы прячутся в документах Microsoft Office
- Принцип функционирования макровирусов для Microsoft Office
- Как отыскать объект подмены
- Выводы
Базовую схему можно описать следующим образом: документ открывается пользователем, файл подключается к удаленным серверам, а после этого загружает и устанавливает на ПК первую часть вредоносного программного обеспечения. Антивирусные утилиты не видят какой-либо опасности на этом этапе.
После того, как подобная возможность взлома была обнаружена, корпорация Microsoft опубликовала данные о том, как пользователи могут защищаться от атак, осуществляемых с помощью пакета Microsoft Office. Наиболее эффективный способ обеспечить безопасность – быть предельно осторожным с неизвестными уведомлениями, отображающимися во время открытия документов Microsoft Office.
Если существует потенциальная опасность, перед пользователями откроется диалоговое окно следующего вида.
После того, как пользователи кликнут по кнопке «Yes», отобразится следующая подсказка.
Необходимо четко понимать, что вирус начнёт загружаться только после того, как человек два раза кликнет по кнопке «Yes».
Помимо всего прочего инструкция от специалистов корпорации Microsoft содержит в себе информацию о том, как продвинутые пользователи могут самостоятельно модифицировать параметры реестра операционной системы Windows, а также деактивировать функцию автоматического обновления данных из одного файла в другой.
Большая часть макровирусов для Microsoft Word сразу после запуска переносит свой код внутрь глобальных макросов конкретного файла. После закрытия программы каждый глобальный макрос записывается в отдельный DOT-файл. В результате этого получается так, что вредоносное программное обеспечение активируется тогда, когда Microsoft Word начинает загрузку глобальных макросов.
Далее вирус переопределяет один или сразу несколько классических макросов, а также перехватывает команды, необходимые для взаимодействия с документами. Во время вызова таких команд документы, к которым идёт обращение, заражаются. Одновременно с этим все файлы конвертируются в формат «Template», что запрещает дальнейшую модификацию формата документа.
Еще один метод внедрения вредоносного программного обеспечения основывается на так именуемых файлах «Add-in» – это служебные дополнения к пакету Microsoft Office. Так «NORMAL.DOT» не модифицируется, а при запуске программы загружаются вирусные макросы. Данный метод буквально целиком копирует заражение глобальных макросов.
Важно! Вирус также может быть внедрён в те документы, которые располагаются в корне каталога «STARTUP». В такой ситуации Microsoft Word в автоматическом режиме подгружает шаблонные файлы из данного каталога.
Для выявления «дырявости» своего «Офиса», необходимо выполнить несложный этап подмены и самостоятельно прощупать уязвимость. Нужно запустить Microsoft Word, не ниже версии 2013, потому как потребуется абсолютная поддержка ISO/IEC, а затем открыть вкладку «Вставка».
В открывшемся окне в строке рядом с пунктом YouTube можно просто вписать слово «Видео», а далее выбрать любое понравившееся изображение. Вставка видео будет отображена при помощи традиционной «превьюшки». Файл необходимо сохранить и закрыть.
Обратите внимание! Размер созданного документа очень редко меняется и составляет всего лишь несколько десятков килобайт. Это может значить лишь одно – ролик не сохраняется локально, а лишь запрашивается из сети по имеющейся ссылке.
Следующий шаг – открытие «внутренностей» файла. Пользователям нужно изменить расширение на ZIP, а затем открыть получившийся документ с помощью любого архиватора.
После открытия содержимого в папке word нужно отыскать файл под названием document.xml. Его необходимо разархивировать и открыть для последующего редактирования. Для этого можно использовать стандартную программу «Блокнот».
Данный файл будет содержать в себе данные о том, что в его теле класс называется wp15:webVideoPr. Необходимо найти данную секцию и внимательно просмотреть её содержимое.
В атрибуте embeddedHtml присутствует iframe YouTube, который выполняется при смене расширения на HTML. А это и есть та самая уязвимость!
Главный источник вредоносного программного обеспечения, как и всегда – это всемирная паутина. Наибольшая численность заражения происходит во время обмена документами Microsoft Word. Пользователь этого популярного редактора с наличием макровируса, сам того не подозревая, пересылает заражённые файлы своим адресатам, а они распространяют их дальше.
Во второй половине июля 2019 года компания Microsoft выпустила очередное обновление для пакета Microsoft Office. По словам разработчиков, проблема вирусной уязвимости Word-документов была полностью исправлена.
Стоит отметить интересный факт, свидетельствующий о том, что для более чем 80% выявленных уязвимостей «заплатки» разрабатываются и становятся доступны уже в день их обнаружению. Именно по этой причине необходимо регулярно обновлять используемую операционную систему и программное обеспечение.
Дайте знать, что вы думаете по этой теме материала в комментариях. За комментарии, лайки, дизлайки, подписки, отклики низкий вам поклон!
A computer virus in the digital world is similar to any burglar or thief in the real world. Because of that, everyone who uses a computer or laptop has to be cautious while using the internet.
Internet is the primary reason any virus or worms enter your personal devices. Malware stays the main web-based danger that presents enormous risks to PCs, particularly when associated with the web. This is the reason behind the advancement of many antivirus tools, including online virus scanners for files.
How can you say whether the attachment document you got by email or downloaded from an unknown site is protected from running and not tainted by a virus? You would most likely depend on the antivirus that comes on your PC to let you know if it’s protected or not. The truth is that antivirus tools are never a great option in identifying and forestalling all viruses.
Since each antivirus software is unique, sensibly examining a dubious file or folder you’ve recently downloaded from a risky web page with different antivirus would not be feasible. Nonetheless, you can’t typically install numerous antivirus software on your PC, or, more than likely, there would be clashes making your PC slower than ever. An answer to this issue is to utilize the best online virus scanner.
What do you mean by an Online Virus Scanner?
Essentially an online antivirus scanner is a web-based assistance that anybody can transfer documents to and have them checked with a wide range of antivirus programming software. You should simply visit the site, peruse your desired document to review, click a button to begin the upload of your document, and wait for the results.
In just a couple of seconds or minutes, relying upon the server burden and speed, the results are then shown on your internet browser for you to choose if it is compromised or not.
Suppose you suspect that your gadget is contaminated with a virus and you haven’t yet bought any paid antivirus. In that case, a free internet-based virus scanner can give a speedy and simple solution without downloading and installing any third-party antivirus software.
These online virus scanners do their process on cloud servers, so these scanners will not consume your device’s processor power to perform their task. Moreover, computational speed on those servers is unimaginable compared to your PCs. So, you can say that using online virus scanners is the best option for anyone.
Online Virus Scanner Vs. Offline Antivirus Software
We all know that at first, antivirus was introduced as offline software only. After many years of this invention, online scanners came into the market to lure the pure new customer base who believes in space-saving concepts in this world of cloud-based technologies.
There are many different aspects of how online scanners are better and different from the old-school antivirus software. Have a look at the below-mentioned reasons.
No installation required
If you use offline antivirus software, you have to download and install it in your system. This will take lots of space in your storage. While online virus scanner does not require any storage space as you can use them directly from your browser.
Free Basic Scanning
The main element of an internet-based virus scanner is that they are free. A web-based virus scanner takes no extra charges. While the filtering is free, it is accepted that the results it gives will likewise be restricted to some extent, and a user will not get a total examining bundle as compared to the offline one.
More frequent updates
One of the major benefits of an online virus scanner is that it is consistently efficient and robust with more frequent updates. It gets new updates due to the web-based community of developers who continuously contribute to several open-source software. So, a client can utilize modern web-based programming, which covers the issues that were not covered previously.
Live threat check
While using any online virus scanners, you may get the support of live checking of viruses and malware on every site you visit. Furthermore, it can also detect any SQL queries which might harm a user’s database.
Speedy and Efficient
As previously mentioned, these online virus scanners do their processing part on their high-speed cloud-based servers. The speeds of such servers cannot be compared with any normal computer. For example, if one file of 18 GB takes 20 minutes to scan on your computer with the offline antivirus software, an online scanner might take less than 5 minutes to scan that same file with more precision and efficiency.
Now, let us look through some of the best online virus scanners you can use to scan your files.
VirusTotal
VirusTotal permits you to look through its informative database using a single file, a URL, an IP address, a domain, or a file hash. On top of that, VirusTotal offers the most significant scope of tools and has possibly the most extensive databases of malignant files and file signatures of various other users.
Moreover, It was acquired by Google in September 2012. In contrast with its rivals, VirusTotal wins in pretty much every viewpoint, like speed (because of Google’s foundation) and having the engines of most antivirus.
It also comes with free open API use, URL filtering, a voting system where users can also comment, numerous language preferences, extra data on the investigated file, and different ways of sending that file to VirusTotal (web, email, program expansions, work area programs, versatile applications).
Internxt
Internxt provides one of the best and most simple web-based virus scanning tools. You have to go to their website, and there you can see one dialog box to upload any suspicious file, or you can also drag and drop that file into that section. Internxt will then do its job to find whether your file is corrupted or not by using its world-class mechanism.
Moreover, you can upload any file as big as 1 GB which is one of the best features of this site. More than 1 Million users have trusted Internxt for their files’ privacy concerns as well as more than 30 recognized institutions have acknowledged their work with awards and mentions.
Apart from being an online virus scanner, it also provides the option for cloud storage and a safe and secure synced photo gallery where you can upload and save your photos. It provides 10 GB of storage for free and for a lifetime, and its pricing starts from € 0.99 per month for 20 GB storage, and it goes up to € 9.99 per month for 2TB of storage which can be helpful for big businesses.
Opentip by Kaspersky
We go on with one more online virus scanner, Opentip, made by a renowned organization that works in the antivirus industry, Kaspersky. The process of file scanning is pretty simple with this online scanner. First, you have to upload your file to the analysis section. Then it will search with all the Kaspersky records of viruses and malware collected with the help of a large customer base of Kaspersky.
This online scanner permits you to upload and check records up to 256 MB from your device. Furthermore, it also supports target files using IPs, Hash, or URLs. It’s a straightforward service, yet you might get intrigued to take this service if you trust Kaspersky antivirus and need to utilize it to examine your files free of charge and without downloading and installing anything.
Jotti’s Malware Scan
As compared to other online virus scanner sites, Jotti is very outdated in terms of user interface and design. Though, it can still manage to do its job pretty well. It is entirely free software, so anyone can use it.
You can upload a maximum of 5 files at a time with a storage cap of 250 MB per slot. While it looks oversimplified, it is a valuable scanner for examining explicit documents, particularly installers from third-party sites and executable files and applications, before utilizing it on your device.
Moreover, it uses 14 different antivirus programs to check your file’s vulnerability report. Some of the famous scanners used by Jotti’s Malware Scan are Avast, K-7, Bit Defender, and many more. Moreover, the tool always uses the updated versions of the scanners mentioned. You should keep in mind that it shares all your personal files with its antivirus scanner partners to improve accuracy.
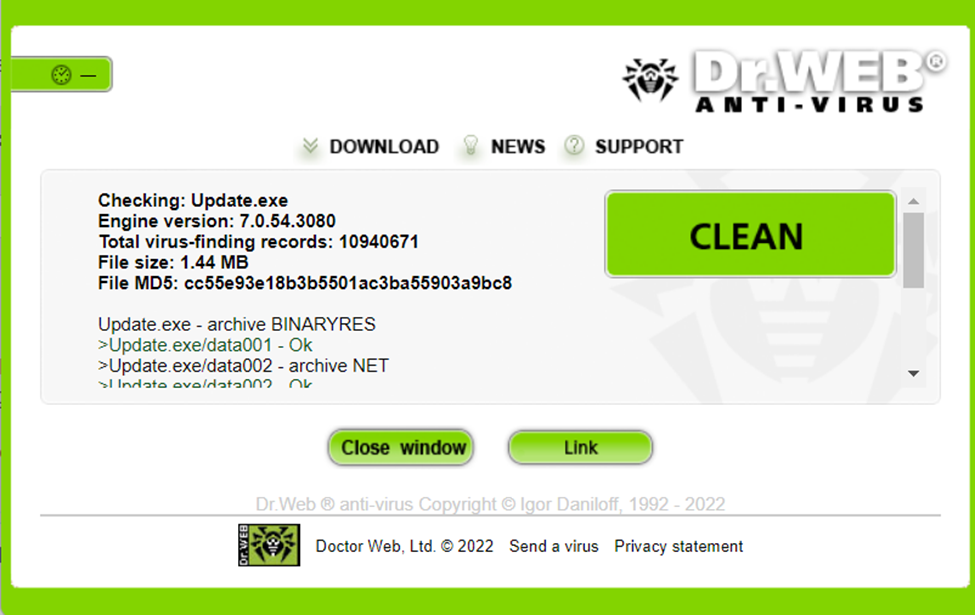
Dr. Web
The Dr. Web scanning site is one of the most superficial scanners on this list. But if you want things to be simple, this can be the best option available for you. It can support only one file at a time with a maximum size of 10 MB. If you are willing to check multiple files in one go, you have to zip those files and then upload that one single zip file for reviewing purposes.
After uploading your file, you have to click on the send button. Then one window will pop up, which will show the scan results as shown above in the image. If it shows that your file contains a malicious virus and you know it is clean, you can also report False Positive results on their site. Moreover, it also provides API, which you can use to put their service on your website for free of cost.
MetaDefender Cloud
MetaDefender is a very easy-to-use internet-based tool that filters and dissects documents, hashes, and IP addresses. It is exceptionally similar to Jotti’s Malware Scan and VirusTotal. You simply need to transfer a file or enter an IP address for scanning purposes.
One of its unique services is dissecting suspicious emails too. You can forward any suspicious mail to sanitize@metadefender.com for analysis purposes. It will return results that will assist you with deciding whether the email is safe to open or not.
Strangely, OPSWAT, the organization creating MetaDefender, likewise offers reports about the latest activities and news about security and safety. Exclusively, you can access malware flare-up reports and statistics of its related data. The site will filter the file you upload with more than 20 different antivirus software, searching for any risk, including strong names like Avira, McAfee, or BitDefender.
Hybrid Analysis
Hybrid Analysis is a fantastic online program that filters for specific dangers for free. You should bookmark it in your browser and utilize it before running any recently downloaded antivirus software on your PC.
You can upload a document of up to 100 MB into the program window or directly insert the file path. Similarly, pasting a link of the program from your browser will also work (to check without downloading it to your PC). This is the best thing because you can know whether a file is safe to download or not. Lastly, you have to click “Analyze.”
Hybrid Analysis takes this online virus scanning process one step ahead. A majority of the online scanners mentioned in this article scan your file in any antivirus software such as Avira, McAfee, Avast, and others.
But here, Hybrid Analysis takes your file to multiple online virus scanning tools such as VirusTotal, MetaDefender, and many more, which are more secure and safe comparatively. Additionally, you can scan IPs, domains, and hashes on Hybrid Analysis.
Conclusion
Indeed you can download any of the best antivirus software available, but it will cost you money and disk storage. Trying out an online virus scanner is the best alternative to such software if you only want to scan some of the files on your computer.
Checking your computer files for malware and virus threats will help keep your system safe and secure.
You may also check out the Best Antivirus Solutions for Small to Medium Businesses.
A computer virus is malicious code that replicates by copying itself to another program, computer boot sector or document and changes how a computer works. A virus spreads between systems after some type of human intervention. Viruses replicate by creating their own files on an infected system, attaching themselves to a legitimate program, infecting a computer’s boot process or infecting user documents. The virus requires someone to knowingly or unknowingly spread the infection. In contrast, a computer worm is standalone programming that does not require human interaction to spread. Viruses and worms are two examples of malware, a broad category that includes any type of malicious code.
A virus can be spread when a user opens an email attachment, runs an executable file, visits an infected website or views an infected website advertisement, known as malvertising. It can also be spread through infected removable storage devices, such as Universal Serial Bus (USB) drives. Once a virus has infected the host, it can infect other system software or resources, modify or disable core functions or applications, and copy, delete or encrypt data. Some viruses begin replicating as soon as they infect the host, while other viruses will lie dormant until a specific trigger causes malicious code to be executed by the device or system.
Many viruses also include evasion or obfuscation capabilities designed to bypass modern antivirus and antimalware software and other security defenses. The rise of polymorphic malware development, which can dynamically change its code as it spreads, has made viruses more difficult to detect and identify.
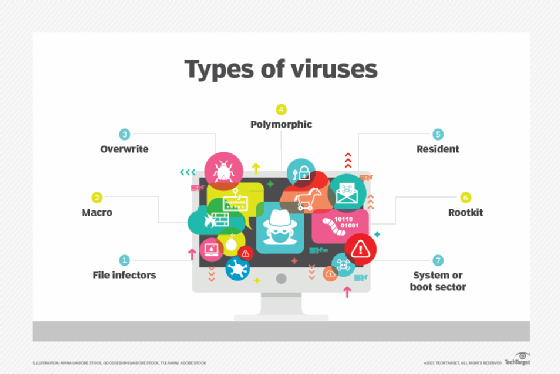
Types of computer viruses
File infectors. Some file infector viruses attach themselves to program files, usually selected COM or EXE files. Others can infect any program for which execution is requested, including SYS, OVL, PRG and MNU files. When the infected program is loaded, the virus is loaded as well. Other file infector viruses arrive as wholly contained programs or scripts sent as an attachment to an email note.
Macro viruses. These viruses specifically target macro language commands in applications such as Microsoft Word and other programs. In Word, macros are saved sequences for commands or keystrokes that are embedded in the documents. Macro viruses, or scripting viruses, can add their malicious code to the legitimate macro sequences in a Word file. Microsoft disabled macros by default in more recent versions of Word; as a result, hackers have used social engineering schemes to convince targeted users to enable macros and launch the virus.
Overwrite viruses. Some viruses are designed specifically to destroy a file or application’s data. After infecting a system, an overwrite virus begins overwriting files with its own code. These viruses can target specific files or applications or systematically overwrite all files on an infected device. An overwrite virus can install new code in files and applications that programs them to spread the virus to additional files, applications and systems.
Polymorphic viruses. A polymorphic virus is a type of malware that has the ability to change or apply updates to its underlying code without changing its basic functions or features. This process helps a virus evade detection from many antimalware and threat detection products that rely on identifying signatures of malware; once a polymorphic virus’s signature is identified by a security product, the virus can then alter itself so it will no longer be detected using that signature.
Resident viruses. This type of virus embeds itself in the memory of a system. The original virus program isn’t needed to infect new files or applications. Even if the original virus is deleted, the version stored in memory can be activated when the operating system (OS) loads a specific application or service. Resident viruses are problematic because they can evade antivirus and antimalware software by hiding in the system’s random access memory (RAM).
Rootkit viruses. A rootkit virus is a type of malware that installs an unauthorized rootkit on an infected system, giving attackers full control of the system with the ability to fundamentally modify or disable functions and programs. Rootkit viruses were designed to bypass antivirus software, which typically scanned only applications and files. More recent versions of major antivirus and antimalware programs include rootkit scanning to identify and mitigate these types of viruses.
System or boot sector viruses. These viruses infect executable code found in certain system areas on a disk. They attach to the disk OS (DOS) boot sector on diskettes and USB thumb drives or the master boot record (MBR) on hard disks. In a typical attack scenario, the victim receives a storage device that contains a boot disk virus. When the victim’s OS is running, files on the external storage device can infect the system; rebooting the system will trigger the boot disk virus. An infected storage device connected to a computer can modify or even replace the existing boot code on the infected system so that, when the system is booted next, the virus will be loaded and run immediately as part of the MBR. Boot viruses are less common now as today’s devices rely less on physical storage media.
How does a computer virus spread?
The distinguishing characteristic of a virus is it spreads from system to system after a user takes some action that either intentionally or accidentally facilitates that spread. This spread is known as virus propagation, and there are many different techniques viruses can use to propagate between systems. The simplest example occurs when a virus is contained within an executable file that a user downloads from the internet, receives in an email message or copies from a removable storage device. As soon as the user executes that file, the virus springs into action, running malicious code that infects the user’s system.
Other viruses can spread through more complex mechanisms. In those cases, a virus running on an infected system may take action to begin its own propagation. For example, a virus might copy itself to all removable media installed on a system, attach itself to email messages sent to a user’s contacts or copy itself to shared file servers. In those cases, the lines become blurred between viruses, which require human assistance to spread, and worms, which spread on their own by exploiting vulnerabilities. The key difference is the virus will always require a human to take an action that enables that final step in the propagation process, while a worm does not require this human assistance.
Viruses can also spread between systems without ever writing data to disk, making them more difficult to detect with virus protection and virus removal mechanisms. These fileless viruses are often launched when a user visits an infected website and then run completely within the target system’s memory, carrying out their malicious payload and then disappearing without a trace.
How do computer viruses attack?
Virus propagation is only half the equation. Once a virus gains a foothold on a newly infected system, it begins to carry out whatever exploit the virus author designed it to perform. This is the payload delivery process, where the virus attacks the target system. Depending on the techniques the virus uses and the privileges of the user who created the infection, the virus may be able to take any action it desires on the target system. This is one of the main reasons that security professionals encourage organizations to follow the principle of least privilege (POLP) and not grant users administrative rights on their own systems. This type of access can magnify the damage caused by a virus.
The payload a virus carries may violate one or more of the principles of cybersecurity: confidentiality, integrity and availability (CIA triad). Confidentiality attacks seek to locate sensitive information stored on the target system and share it with the attacker. For example, a virus might search the local hard drive (HD) for Social Security numbers, credit card numbers and passwords, and then funnel those back to the attacker. Integrity attacks seek to make unauthorized modifications or deletions of information stored on the system. For example, a virus might delete files stored on a system or make unauthorized modifications to the OS to avoid detection. Availability attacks seek to deprive the legitimate user access to the system or the information it contains. For example, ransomware is a type of virus that encrypts information on the user’s HD, preventing legitimate access. It then demands the payment of a ransom in exchange for the decryption key.
Viruses may also join a system to a botnet, placing it under the control of the attacker. Systems joined to botnets are commonly used to conduct distributed denial of service (DDoS) attacks against websites and other systems.
How do you prevent computer viruses?
The following measures can help you prevent a virus infection:
- Install current antivirus and antispyware software, and keep it up to date.
- Run daily scans of antivirus software.
- Disable autorun to prevent viruses from propagating to any media connected to the system.
- Regularly patch the OS and applications installed on the computer.
- Don’t click on web links sent via email from unknown senders.
- Don’t download files from the internet or email from unknown senders.
- Install a hardware-based firewall.
What are signs you may be infected with a computer virus?
The following are indications that your computer might be infected by a virus:
- The computer takes a long time to start up, and performance is slow.
- The computer experiences frequent crashes or shutdown and error messages.
- The computer behaves erratically, such as not responding to clicks or opening files on its own.
- The computer’s HD is acting strangely — for example, constantly spinning or making continual noise.
- Email is corrupted.
- The amount of storage on the computer is reduced.
- Files and other data on the computer have gone missing.
How do you remove a computer virus?
In the event your personal computer (PC) becomes infected with a virus, you can take the following steps to remove it:
- Enter Safe Mode. The process will depend on the version of Windows you’re running.
- Delete temporary files. While in Safe Mode, use the Disk Cleanup tool to delete temporary files.
- Download an on-demand and a real-time virus scanner.
- Run the on-demand scanner followed by the real-time scanner. If neither scanner removes the virus, then it might need to be removed manually. This should only be done by an expert who is experienced at using Windows Registry and knows how to view and delete system and program files.
- Reinstall any files or programs damaged by the virus.
History of computer viruses
The first known computer virus was developed in 1971 by Robert Thomas, an engineer at BBN Technologies. Known as the Creeper virus, Thomas’ experimental program infected mainframes on the Advanced Research Projects Agency Network (ARPANET), displaying the teletype message: «I’m the creeper: Catch me if you can.»
The first computer virus to be discovered in the wild was Elk Cloner, which infected Apple II OSes through floppy disks and displayed a humorous message on infected computers. Elk Cloner, which was developed by 15-year-old Richard Skrenta in 1982, was designed as a prank, but it demonstrated how a potentially malicious program could be installed in an Apple computer’s memory and prevent users from removing the program.
The term computer virus wasn’t used until a year later. Fred Cohen, a graduate student at the University of Southern California (USC), wrote an academic paper titled «Computer Viruses — Theory and Experiments» and credited his academic advisor and RSA Security co-founder Leonard Adleman with coining the term computer virus in 1983.
Famous computer viruses
Notable examples of early computer viruses include the following:
- The Brain virus, which initially appeared in 1986, is considered to be the first Microsoft DOS (MS-DOS) PC virus. Brain was a boot sector virus. It spread through infected floppy disk boot sectors, and once installed on a new PC, it would install itself to the system’s memory and subsequently infect any new disks inserted into that PC.
- The Jerusalem virus, also known as the Friday the 13th virus, was discovered in 1987 and spread throughout Israel via floppy disks and email attachments. The DOS virus would infect a system and delete all files and programs when the system’s calendar reached Friday the 13th.
- The Melissa virus, which first appeared in 1999, was distributed as an email attachment. If the infected systems had Microsoft Outlook, the virus would be sent to the first 50 people in an infected user’s contact list. This virus also affected macros in Microsoft Word and disabled or lowered security protections in the program.
- The Archiveus Trojan, which debuted in 2006, was the first known case of a ransomwarevirus that used strong encryption to encrypt users’ files and data. Archiveus targeted Windows systems, used Rivest-Shamir-Adleman (RSA) encryption algorithms — whereas earlier versions of ransomware used weaker and easily defeated encryption technology — and demanded victims purchase products from an online pharmacy.
- The Zeus Trojan, or Zbot, one of the most well-known and widely spread viruses in history, first appeared in 2006 but has evolved over the years and continues to cause problems as new variants emerge. The Zeus Trojan was initially used to infect Windows systems and harvest banking credentials and account information from victims. The virus spreads through phishing attacks, drive-by downloads and man-in-the-browser The Zeus malware kit was adapted by cybercriminals to include new functionality to evade antivirus programs, as well as spawn new variants of the Trojan, such as ZeusVM, which uses steganography techniques to hide its data.
- The Cabir virus is the first verified example of a mobile phone virus for the now-defunct Nokia Symbian OS. The virus was believed to be created by a group from the Czech Republic and Slovakia called 29A, who sent it to a number of security software companies, including Symantec in the U.S. and Kaspersky Lab in Russia. Cabir is considered a proof-of-concept (POC) virus because it proves that a virus can be written for mobile phones, something that was once doubted.
This was last updated in March 2021
Continue Reading About virus (computer virus)
- How to protect the network from ransomware in 5 steps
- Malware quiz: Test your knowledge of types of terms
- Enterprise ransomware prevention measures to enact in 2021
- Top network attacks of 2020 that will influence the decade
- Computer viruses a bigger threat with pandemic
Dig Deeper on Threats and vulnerabilities
-
Trojan horse
By: Casey Clark
-
computer worm
By: Crystal Bedell
-
blended threat
By: Kinza Yasar
-
malware
By: Ben Lutkevich