These responses only contain half of the answer. There are generally 2 ways to embed a virus into an office document.
Macros:
Macros are snippets of Visual basic code generally containing functions that can enhance the document maybe for complex counting or auto filling or many other reasons. Macros can do a lot like download files from the internet, and install trojans or other viruses. Macros sometimes require you to click a button or «enable» them before they’ll execute but this can depend on your security settings. You should never trust macros from the internet without understanding them at a basic level, the best advice is to disable macros and enable them on a case by case basis.
Exploits:
The other way documents can contain viruses is via exploits, software exploits are generally due to an error made during the development of the program and once discovered are often patched. Exploits are often stored in saved files like word documents or excel sheets. Exploits are made up of 2 parts, the actual exploit and the payload what happens when word for example opens a file containing an exploit is the document looks normal until a certain bit where it may contain something more complex like a shape, in word 2003 there was an exploit in the shape processor where crafted shape data would allow code in the remaining of the document to execute and install pretty much anything it wants, a common technique is code that downloads more virus files from the internet and then starts sending information about your computer back to the attacker, they will often receive your keystrokes, maybe passwords or they might try and inject code into websites you visit making you transfer money without your knowledge. There are ways to combat exploits though. If you can you should use some exploit mitigation software like emet but your antivirus may do exploit mitigation also. The second thing you can do arguably more important than the first is keep all your software up to date. As exploits get discovered, developers will update their applications to not be affected. So it is important to keep things updated and be suspicious of files sent to you from unknown sources.
Loading

Да-да, те самые книги и руководства про успешный успех от нелюбимых вами инфоцыган, в лёгкую могут таить под капотом реальную угрозу для вашей безопасности. Особенно если качаете вы это добро с какого-нибудь сливапа или только что созданного паблика в телеграме. Тут вероятность нарваться на дерьмецо возрастает в разы.
Что ж, друзья, думаю суть понятна. Давайте нынче не будем долго запрягать и сразу перейдём к практике. А то мне ещё утром на участок надо бежать, поправки путинские принимать. Вбрасывать там, фальсифицировать. Ну вы знаете, всё как обычно. Мы там это, с колен вроде как встаём, так что низя опаздывать. Уж не обессудьте за столь лаконичное вступление. Погнали.
Шаг 1. Создаём на рабочем столе новый вордовский документ. Так и назову его – гавнокурс, чтобы все инфоцыгане, включая вашего покорного слугу, обладающего самоиронией, были довольны.

Шаг 2. Открыв док переходим на вкладку «Вставка» и ищем пункт интеграции «Видео из интернета». В открывшемся окне вводим для примера название youtube-канала и кликаем по иконке поиска.

Шаг 3. Вставлю для демонстрации рандомное видео со своего проекта.

Шаг 4. Отлично. Видос в файле. Примерно так их вставляют в качестве доп. материалов к основной статье различные интернет-гуру. Теперь можно закрывать документ, не забывая при этом сохранить изменения.

Шаг 5. Далее запускаем WinRAR и вызвав контекстное меню вордовского файла, переходим к его внутреннему содержимому.

Шаг 6. Нас интересует файлик «document.xml». Он содержит в себе дополнительные настройки для текста и, собственно, сам текст нашего документа. Вытаскиваем его на рабочий стол

Шаг 7. И открыв в нотпаде или блокноте ищем строчку со ссылкой на youtube-видео. Вот она.

Шаг 8. Ну а дальше, мы вольны творить что душе угодно. Давайте, забавы ради встроим код логгера для выяснения местоположения и IP-адреса потенциальной жертвы. Для этого заходим на iplogger.org и вставляем любую ссылку в первое окно. Жмём «получить код».

Шаг 9. Копируем получившуюся ссылку для сбора IP в буфер обмена.

Шаг 10. И вставляем её вместо ссылки на видео в нашем XML-файле.

Шаг 11. После внесения изменений закрываем редактор файла с последующим сохранением.

Шаг 12. И возвращаем его на место закинув в окно WinRAR’a. Окей.

Шаг 13. Давайте проверим, что же мы намудрили. Открываем гавнокурс и подводим ползунок к видосу. Программа показывает, что при нажатии, будет запущен видеоролик с ютуба. Ничего подозрительного. Уверяю, 88% юзверей даже не почуют подвоха.

Шаг 14. Однако при открытии, вместо долгожданного видео, на экране выскакивает ошибка. Тут человек, как правило думает, что мол, ну и ладно. Подумаешь видос не работает, главное книжку скачал на халяву.

Шаг 15. Мы же, тем временем, можем вернуться на сайт iplogger и в разделе «Статистика посещений», посмотреть IP-адрес с которого была зафиксирована попытка просмотра.

Шаг 16. Также тут можно прочекать геолокацию, вплоть до дома.

И это, ещё самое безобидное, что можно было внедрить. Вы ведь помните, я тут не армию злоумышленников выращиваю, а объясняю основы инфосека в обучающих целях для понимающей аудитории. Но настоящий блэк хэт будет вставлять далеко не безобидный логгер для выяснения вашего адреса. Он встроит ратник, вирусную программу или какого-нибудь хитро вые***ый java-script.
Данная фиха работает в пакетах MSOffice, начиная с версии 2013 года. И в данный момент, её до сих пор не пофиксили. Я специально скачал для записи самый последний апдейт, дабы убедиться в проверке функционала. И да, я дико извиняюсь за кликбейт, но вы порой правда просите сделать очень узкие темы, которые в интернете никому на*уй не сдались. Поэтому приходится как-то выкручиваться и перефразировать.
Однако, уверяю вас, это сделано умышленно и даже банальное знание IP-адреса может сыграть на руку грамотному пентестеру. Так, в следующем видео, я покажу, как зная внешний IP-адрес роутера, можно провести по нему полноценную DDoS-атаку. Но эт только если соберёте 500 лайков под этим роликом. Денчику нужны ваши лойсы. А ещё я коллекционирую души в виде подписок. Так что если ты, друг мой впервые забрёл на канал, то не тупи а.
Кликай на грёбаный колокол и в твоей ленте регулярно будут появляться годнейшие гайды на тему этичных взломов, пентестинга и самой что ни на есть информационной безопасности. С олдов по традиции, жду комментарии, касательно того, что бы вы встроили в такой документ, перейди вы, чисто теоретически на тёмную сторону. Мне будет весьма интересно узнать, чего же вы жаждите на самом деле.
Ну а у меня на сегодня всё. В заключении, хочу пожелать вам удачи, успеха и самое главное безопасного обучения. Берегите себя и свои тачки, скачивайте материалы только на официальных сайтах инфоцыган и никогда не попадайтесь на такие уловки. Помните, что халявный сыр – бывает только в мышеловке. А за всё, действительно годное и крутое – приходится платить либо временем, либо рублём, либо дважды. С вами, как обычно, был Денчик. До новых встреч, камрады. Всем пока.

Microsoft Word will greatly benefit from specialized antivirus software to protect its files.
by Milan Stanojevic
Milan has been enthusiastic about technology ever since his childhood days, and this led him to take interest in all PC-related technologies. He’s a PC enthusiast and he… read more
Updated on March 31, 2023
Fact checked by
Alex Serban
After moving away from the corporate work-style, Alex has found rewards in a lifestyle of constant analysis, team coordination and pestering his colleagues. Holding an MCSA Windows Server… read more
- The security tools below come with advanced AI scanning and malware removal.
- Looking for a Microsoft Word antivirus with a free download? We included such apps below.
- Keep in mind that choosing an anti-malware program with an included VPN keeps you extra safe.
Microsoft Word users may have at one time or another experienced threats that infiltrated their computer systems by a simple opening of a file attachment or downloading from an unknown source.
The general degree of danger for such vulnerabilities is determined by the ease of exploitation, the prevalence of such programs, possible consequences of the attack, and the availability of prepared countermeasures.
The consequences of such attacks are serious because once the attacker has access, he gets the same privileges that you, the user, has on your computer system, including files and documents.
This article looks at the best Microsoft Word antivirus software to protect your Windows 10 PC and your documents against exploitation and threats.
Can Word files be infected?
Yes, any Word files can be corrupted by difficult viruses and malware. In fact, you can have a virus infection within any Word document, especially in case you’re not using an antivirus for Microsoft Office 365.
It’s worth mentioning that Microsoft Word files may contain viruses because of a macro virus that can corrupt your entire operating system.
What’s the best Microsoft Word antivirus?
ESET NOD32 Antivirus – Multilayered files security
Eset NOD32 protects all your sensitive files running on the Windows 10 operating system.
This cross-platform antimalware protection safeguards against infection, with the Eset NOD32 Technology working with Exploit Blocker and Advanced Memory Scanner to neutralize sophisticated threats.
Malicious attachments can contain threats often embedded into emails as phishing or scam emails to trick you into opening infected Word documents.
Such emails have enticing subject lines trying to give you free stuff or scare you into opening the document.
Such documents look harmless but install the malware in the background or display useless information but it may be too late.
Microsoft Word software that has policies that deal with macros and attachments is the best way to combat this type of malware delivery.
Some benefits you can enjoy with this Microsoft Word antivirus include data protection with specialized cleaners, optimization for virtual environments, storage scans, log collection, simple licensing, and it is light on your system.
Let’s see some of the program’s key features:
- Powerful multilayered security
- Minimal power usage
- Transfer your license
- Install and forget

ESET NOD32 Antivirus
Never worry about malware again thanks to the legendary protection offered by this antivirus.
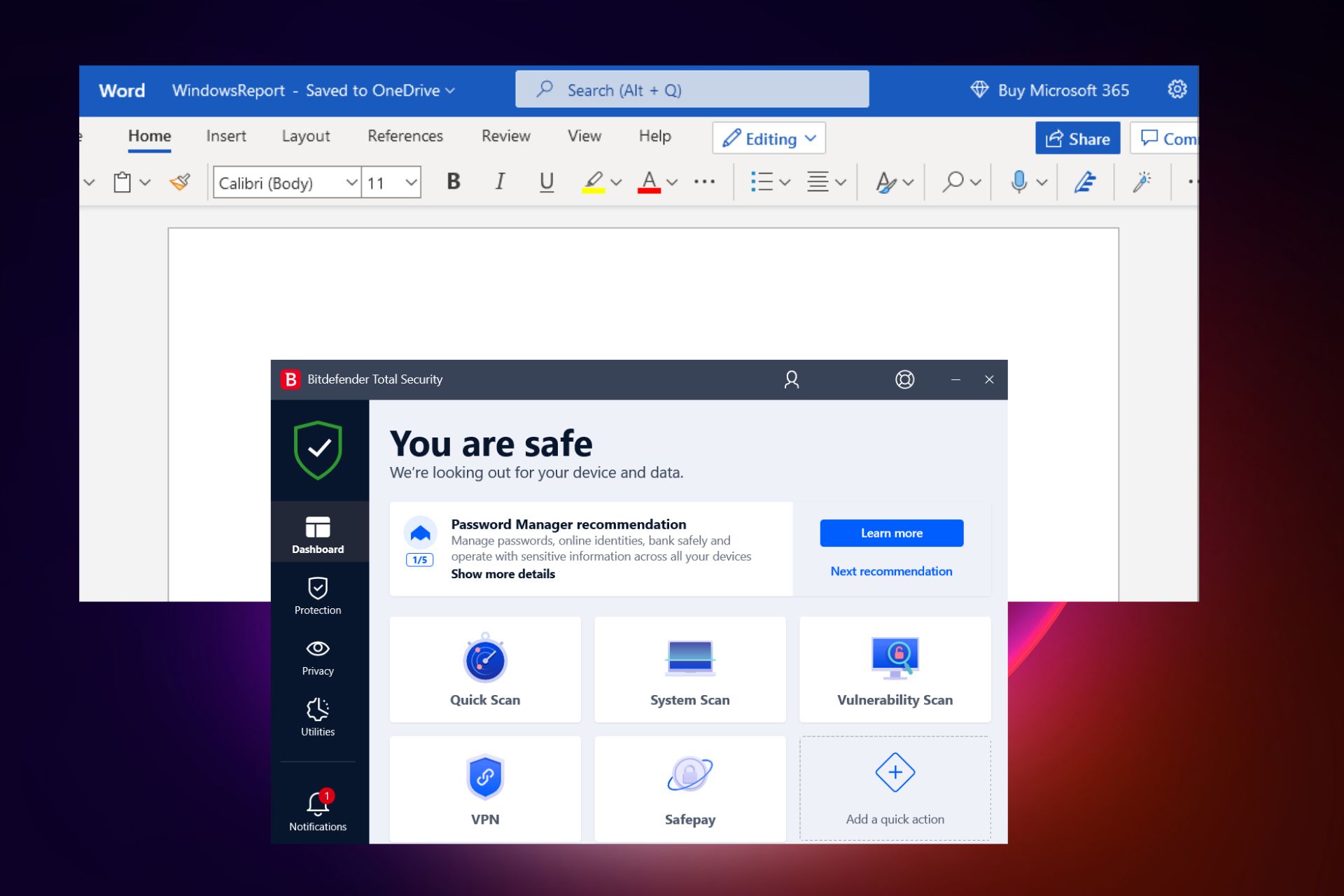
Bitdefender Antivirus Plus – Threat detection against strong malware
This antivirus delivers continuous, powerful protection against threats that may exploit Microsoft Word or other Office programs, and any other sophisticated threats.
Bitdefender Labs release signature updates to protect against unpatched Word exploits, as vulnerabilities affect Word programs, which in turn can be exploited by attackers to gain access to your systems and documents.
A good example is Backdoor PoisonIvy, which when installed, grants complete control over the affected computer to an attacker. Bitdefender antivirus detected this backdoor threat.
Other malicious files containing exploits are detected by Bitdefender and published on their website once analyses are complete.
Bitdefender features layered next-generation endpoint protection against cyber threats to detect advanced persistent threats, protect from ransomware, and defeat exploits, and zero-day attacks that are common vulnerabilities in Microsoft Word.
It also has the GravityZone Endpoint Security HD with HyperDetect with specialized local machine models and behavior analysis techniques trained to spot and detect hacking tools, malware obfuscation, and exploits.
Bitdefender’s core features include:
- Anti-phishing
- Multilayered protection
- Safe online banking
- Privacy while surfing the web
- Game, work, and movie mode

Bitdefender Antivirus Plus
Bitdefender lets you protect all your Microsoft Office programs. Claim the best deal right away!
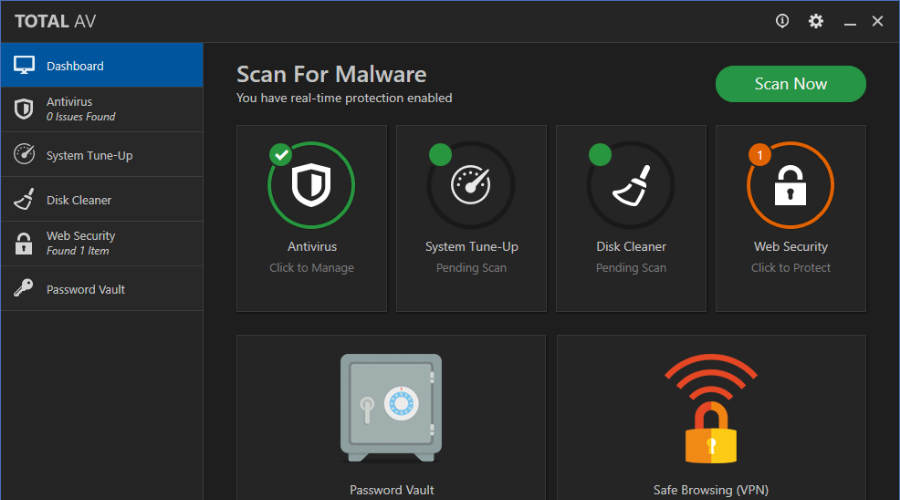
TotalAV – Continous files virus detection
TotalAV is a highly popular antivirus for real-time security against all kinds of threats such as malware infection.
Using this complex antivirus will help you stop any spyware or ransomware attacks from corrupting Office Word files on your device.
There are efficient antivirus engines that can safeguard any PC from dangerous threats phishing scams, rogue apps, or unwanted software that can corrupt your system.
You will benefit from web protection against tracking ads or data breach monitoring for reliable security against the most complex malware infections.
Plus, you have savvy features to protect your Microsoft Word documents using the Zero Day cloud scanning, a remote firewall, or system tune-up optimization.
An additional benefit is that you can schedule system scans whenever it’s needed, so your files and documents are always safe.
Let’s see some of the program’s key features:
- Anti-adware protection
- Real-time checking for download or exe. files
- Disk Cleaner tool
- Browsing data cleaner
- Great compatibility with iOS or Android

TotalAV
Fully secure Microsoft Word files against complex threats and phishing attacks with this antivirus.
Avira Free Security – Blocks malicious websites
When we talk about free antivirus software, we can’t leave Avira Free Security aside. There is so much that this tool has to offer, and all completely free, without ads or popups.
To be precise, Avira will protect your system from major threats while keeping it as stress-free as possible, so you can continue your daily activities without interruptions.
Obviously, the software uses advanced AI and machine learning to deliver the most accurate scans and remove any intruders from your device.
This antivirus choice is ideal to secure your Office Word files because it comes with intelligent tools to detect malicious websites or malware.
More than this, the free VPN will support your online privacy and keep you away from data theft and phishing attempts.
Besides all, you have the speed booster that helps you increase the overall speed and system performance.
Avira Free Security has other awesome features:
- Free VPN that secures online activities
- Anti-scams, identity, and data theft
- Has a system optimizer
- Completely free, not even running ads
- Lightweight for your system

Avira Free Security
Why should you worry about stolen data and viruses? Avira will handle everything for you.
Panda DOME Essential – real-time firewall security
This antivirus pools advanced protection technologies, detection, and remediation features, to classify 100 percent of running processes on all endpoints.
It features endpoint protection from a centralized platform to protect against all forms of malware and spam. It also has contextual intelligence used to reveal patterns of malicious behavior and generate defensive strategies to counter any known or unknown threats.
Panda DOME Essential offers standard functionality with three types of scans including real-time, on-demand, and scheduled scans.
As a Microsoft Word antivirus, Panda can delete the virus or threat, rename affected files or documents, or alternatively, ignore the file or document.
If you regularly send out or receive Microsoft Word files, you can configure Panda to detect and eliminate macro viruses automatically, including in compressed files.
It is easy to use, install and maintain, minimizes resource usage, gives guaranteed service availability, and constant system monitoring.
Here are the program’s best features:
- Real-time protection
- Free VPN
- Scanning of external devices
- Windows antivirus and firewall
- Wi-fi protection

Panda DOME Essential
Panda offers great Microsoft Word protection without slowing down your system. Eager to try it out?
Kaspersky – Great protection for Word
Kaspersky has easy management from a cloud-based console if you’re a corporate or enterprise entity.
The Kaspersky antivirus for Windows Workstations is a Microsoft Word antivirus that is fully compatible with Microsoft Office 2003, 2007, and 2010.
Features include cloud endpoint security with strong protection and easy management, advanced world-class cybersecurity for business, and ready-to-scale protection against every type of threat your company faces, on-premise or cloud.
Its multi-layered protection is powered by machine learning and human expertise and offers granular security management.
You’ll also benefit from secure communication and collaboration, and enhanced mobile security and device management.
It also includes a security operations center to detect and remediate threats and Fraud Prevention for proactive detection of cross-channel fraud in real time.
It’s comprehensive practical reporting (APT Intelligence) feature lets you increase your awareness and knowledge of high-profile, targeted attacks.
Kaspersky’s Automatic Exploit Prevention technology helps protect you and your documents against zero-day threats common in Microsoft Word (or Office).
This technology is based on the analysis of exploits’ behavior and data from the most frequently attacked apps.
Take a look at Kaspersky’s most notable features:
- Multilayered security
- Lightweight and optimized
- Intuitive and simple UI
- Security operations center
- Fraud prevention

Kaspersky
Always be ahead of online threats and malicious software thanks to Kaspersky.
Sophos – Stoping trojan malware
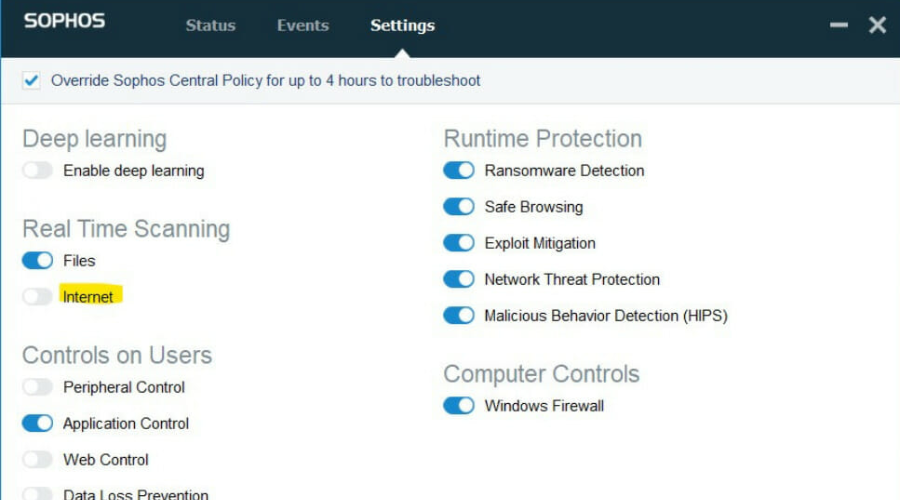
Sophos is your best Microsoft Word antivirus as it is simple to set up and easy to manage and maintain while providing advanced, powerful server-specific protection for your apps and data.
It features anti-ransomware, app whitelisting, advanced anti-malware, and HIPS, with easy, centralized management of security for all servers.
It also comes with CryptoGuard to stop ransomware from encrypting critical business data, malicious traffic detection, and Synchronized Security for accelerated threat discovery, application, and device control.
Many attackers have been leveraging the zero-day vulnerability in Microsoft’s Dynamic Data Exchange (DDE) trick to deploy remote-access Trojans (RATs).
Sophos Intercept X protects customers from zero-day vulnerabilities by stopping attacks using the DDE that attack Microsoft Word and Office in general, because attackers could exploit it to turn malware without using macros.
Let’s take a look at the tool’s core features:
- Malware scanning and removal
- AI threat detection
- Web and privacy protection
- Premium support
- Parental web filtering
- Security management

Sophos
Scan, block, quarantine, and remove all malware and viruses from your devices with Sophos.
Avast Free Antivirus – AI detection tools
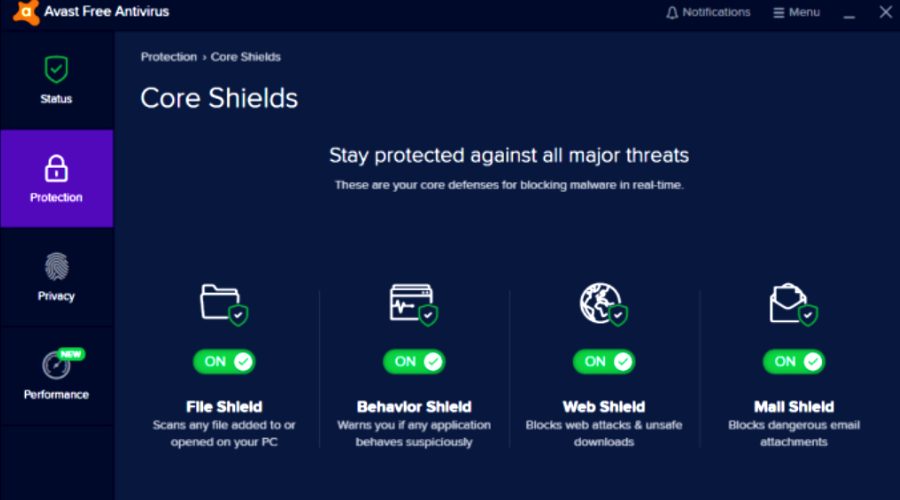
Avast Free Antivirus is a completely free virus protection choice that relies on advertisements to gain revenue. Additionally, you can upgrade it to one of the paid versions for extra awesome features.
Nonetheless, even the free version includes Avast’s advanced AI scanning that will protect your files from all kinds of old and new viruses and other useful tools.
One such tool is the PC cleaner which will remove any bloatware from your machine, thus optimizing and making it work faster.
Moreover, the software is easy to set up and mostly automatized, which means it will run periodic system scans and keep an eye out for suspicious activity by itself.
Let’s see some more of its key features:
- Effortless security
- Fresh and intuitive interface
- Do Not Disturb mode
- Behavior shield keeps an eye on suspicious files

Avast Free Antivirus
This trustful antivirus provides essential protection in light, powerful, and free software.
Which Microsoft Word antivirus do you use? Could it be the powerful BullGuard or Panda since it can detect macro viruses automatically?
If you are unhappy with Windows Defender, you have a thorough list of the best antivirus programs with unlimited validity for Windows 10.
Share with us your favorite and your experience with it in the comments section below.
Newsletter
На самом деле правильнее было бы назвать эту статью «Как хакеры скрывают вирусы в документах Office а Microsoft на это наплевать» Но давайте по порядку.
В последних версиях Microsoft Office по умолчанию документы сохраняются в формате, основанном на Office Open XML, но Microsoft не во всем следует открытому стандарту. Вариант Microsoft часто называют MOX, Microsoft Open XML. Этот самый MOX имеет уязвимости, создающие угрозы безопасности. В этой статье мы подробно разберем одну из таких дыр, которая на момент статьи так и не закрыта.
Еще по теме: Лучшие сайты для поиска уязвимостей
Почти сразу после публикации чернового варианта OOXML началась битва за его стандартизацию. Вот краткая хронология версий.
В 2016 году были выпущены дополнения к 5-ой версии: ISO/IEC 29500-1:2016 и ISO/IEC 29500-4:2016. Работа над стандартом продолжается, а компания Microsoft допускает все больше проприетарных особенностей его реализации в последних версиях Office. Хуже того: Microsoft не признает старые уязвимости, оставляя их в новых версиях. Вы не поверите, но описываемая в данной статье уязвимость известна с Office 2013 и актуальна вплоть до Office 2019.
ECMA-376 включает в себя три различные спецификации для каждого из трех основных типов документов Office — WordprocessingML для текстовых документов, SpreadsheetML для электронных таблиц и PresentationML для презентаций. Мы будем использовать WordprocessingML.
Я возьму на себя смелость указать на два критичных с точки зрения безопасности недостатка MOX, унаследованных от OOXML:
- возможность легкого редактирования внутренней структуры документов;
- отсутствие проверок на злонамеренную модификацию.
По сути, MOX и OOXML — это XML в ZIP. Это отличный hacker-friendly-формат, поскольку найти и заменить свойства объектов в нем исключительно просто даже без использования HEX-редакторов и прочих специфических утилит. Достаточно встроенной в Windows поддержки ZIP и «Блокнота». Весь код легко читается глазами и правится, как текст. Ни сверки контрольных сумм, ни каких-то иных специфических проверок при этом не выполняется. Word лишь проверяет целостность документа, которая не нарушается при подменах с соблюдением правил синтаксиса.
Если в документ вставлен объект, загружаемый с внешнего ресурса (например, ссылка на видео), то в соответствующей секции создается легко читаемая (и так же просто изменяемая) гиперссылка. Это прямая дорога к фишингу или запуску троянов в один клик.
Статья предназначена для профессиональных пентестеров, руководителей службы CISO (информационной безопасности), а так же для «белых хакеров». Ни автор статьи, ни редакция сайта spy-soft.net не несут ответственности за любой возможный вред, причиненный материалами данной статьи,
Описание уязвимости
В базе уязвимостей MITRE есть много однотипных записей вида: «Microsoft Office… do not properly validate record information during parsing of (Excel spreadsheets / Word documents, Power Point presentations)… which allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted file)». Проще говоря, проблемы парсинга XML в MS Office неисчерпаемы, как атом.
Я уже рассматривал одну из них в статье «Перехват хеша с помощью документа NTLMv2-SSP». Сейчас я познакомлю вас с другой атакой, также слегка изменив внутренности Word.
Начиная с Office 2013 в OOXML стал доступен класс WebVideoProperty. Он используется в разметке при вставке в документ онлайн-видео и описывает параметры его воспроизведения через набор атрибутов.
Нас интересует атрибут embeddedHtml. Он используется для вставки сторонних объектов и содержит ссылку на них (например, на видео с YouTube). Из-за того что данный параметр «знает», откуда открывать картинку видеозаписи, его невозможно опустить при парсинге.
Поиск объекта подмены
Давайте выполним простую атаку подмены и пощупаем уязвимость своими руками. Запускаем Word (требуется версия 2013 или выше, так как нам нужна полная поддержка ISO/IEC 29500 Strict) и открываем меню «Вставка».
В появившемся окне в строчке напротив YouTube я просто вписал слово «видео» и выбрал первую понравившуюся картинку. Вставка ролика отобразилась на листе документа типичной превьюшкой.
Сохраним и закроем его. Обратите внимание, что размер файла почти не изменился. У меня он занимал несчастные килобайты. Значит, вставленное видео не сохраняется локально, а всегда запрашивается из интернета по известной ссылке.
Следующим шагом нам надо заглянуть в нутро документа. Меняем расширение .docx на .zip, открываем любым архиватором и видим содержимое.
В папке word нам нужен файл document.xml. Разархивируем и откроем его на редактирование (подойдет и простой Notepad, хотя Notepad++ намного удобнее из-за подсветки синтаксиса).
В скудной документации о классе WebVideoProperty указано, что в теле документа он именуется wp15:webVideoPr. Находим эту секцию и смотрим ее содержание.
Конструкция изначально выглядит следующим образом:
|
embeddedHtml=«<iframe id="ytplayer" src="https://www.youtube.com/embed/k85mRPqvMbE" frameborder="0" type="text/html" width="816" height="480" />» |
Атрибут embeddedHtml содержит iframe YouTube, который при замене на HTML или JavaScript будет выполняться. А это не что иное, как уязвимость!
Эксплуатация уязвимости
Если внимательно посмотреть на содержимое секции, то можно заметить, что символы < и > заменены на < и >. Это способ записи символьных данных без использования раздела CDATA. Они указывают парсеру на то, что эта часть документа не содержит разметки. Так же мы должны поступить со всеми нашими спецсимволами.
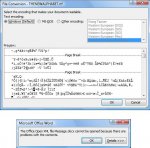
Еще стоит отметить, что все параметры отделены друг от друга точкой с запятой. Если мы пропустим хотя бы одну из них, то при открытии документа произойдет ошибка проверки целостности файла. Правда, Word облегчает задачу, подсказывая, где именно мы ошиблись (см. скриншот).
Давайте удалим все, что находится между кавычками, и попробуем вставить свой HTML-код. Сначала добавим отображаемую часть ссылки:
В нашем случае она будет выглядеть следующим образом:
|
embeddedHtml=«<H1>Хакер</H1>» |
Теперь подменим исходную ссылку на ролик с YouTube своей. Например, загрузим какой-нибудь файл на компьютер жертвы.
В качестве «вредоносного сервера» я поднял дистрибутив Ubuntu 16.4 с Apache2 и положил в каталог /var/www/html два файла: условного зловреда и простую HTML-страницу со ссылкой на него. IP-адрес сервера в локальной сети — 192.168.1.20.
Далее нам необходимо все это указать в embeddedHtml:
|
embeddedHtml=«<a href="http://192.168.1.20/1.html" frameborder="0" type="text/html" width="816" height="480" >Xакер</a>» h=«480» w=«816» |
Теперь сохраним наш измененный файл и запустим его.
Для первой проверки я подготовил имитацию жертвы — компьютер с Windows 10 (1803) и MS Office 2016 Professional Plus VL x86, который мы и будем атаковать.
После запуска файла не видно ничего необычного. Открывается документ со вставленным видеороликом. При наведении курсора отображается корректная ссылка на него. Но, если нажать на воспроизведение, вместо видео отобразится наша ссылка.
В реальном сценарии вместо хакер лучше написать что-то более подходящее для фишинга. Например, Click to begin playback.
Может быть, со времен Office 2016 уязвимость уже пофиксили? Давайте проверим, сработает ли этот способ в Microsoft Office Pro Plus 2019 и Windows 10 (1803).
Открываем тот же файл и пробуем запустить видео. Слово «хакер» так же подчеркнуто и выступает в качестве ссылки. При клике на него открывается браузер Edge с нашей страницей на «злом сервере». На ней все та же ссылка для загрузки зловреда.
Примечания
Стоит уточнить ряд важных моментов. Трюк работает, если пользователь просто нажимает левой клавишей мыши на кнопку Play в превьюшке вставленного в документ видео. Так делает большинство, но продвинутые могут кликнуть с зажатой клавишей Ctrl. В этом случае начнется воспроизведение видео.
Почему так происходит?
При нажатии левой кнопки мыши с клавишей Ctrl и без нее Word обращается к разным секциям документа. В первом случае он считывает подмененную ссылку из worddocument.xml и предлагает выполнить переход по ней. Во втором — считывает оригинальную ссылку на видеоролик из word_relsdocument.xml.rels и запускает его.
Если же подменить адрес в обеих секциях, фишинговая ссылка будет отображаться при наведении курсора мыши на превь ролика. Такой грубый вариант атаки сработает только с самыми невнимательными пользователями.
Также заметь, что при нажатии левой кнопкой мыши с Ctrl откроется браузер, установленный по умолчанию. Если же просто кликать, то (вредоносная) ссылка всегда будет открываться в браузере. Это еще один вектор атаки при проведении пентеста.
В зависимости от версий ОС и Office, а также настроек безопасности у жертвы могут сработать другие компоненты защиты. Например, Office 2010 ограниченно поддерживает OOXML. Он предложит разрешить редактирование документа прежде, чем позволит кликнуть на превью видео. В Windows 7 IE выдаст предупреждение при открытии ссылки.
С Windows 10 наблюдается совсем другая картина. В настройках по умолчанию (а у потенциальной жертвы они, как правило, такие) ни IE, ни Edge ни о чем не предупреждают. Ссылка открывается без дополнительных действий. Отсюда можно сделать парадоксальный вывод о том, что новая операционная система оказалась более уязвима к подобным атакам.
Для дополнительной проверки я открывал файл с измененной ссылкой в следующих офисных пакетах:
- Open Office 4.1.6;
- Libre Office 6.1.3;
- Soft Maker Office 2018.
Все они официально поддерживают OOXML, причем в точном соответствии со стандартом ISO/IEC 29500. Ни один из них не подвержен рассмотренной уязвимости, поскольку все вольности Microsoft игнорируются. Получает, что пользователь лучше защищен благодаря отсутствию поддержки проприетарной функции вставки онлайн-видео… но ведь, кроме роликов, в документы можно вставлять и другие объекты.
Выводы
В данном примере мы рассмотрели, как модифицировать XML-разметку офисных документов, чтобы выполнить подмену ссылки и подсунуть жертве зловреда. При проведении пентеста вместо пугающей надписи «Хакер» можно подобрать что-нибудь более привлекательное. Например, указать, что для воспроизведения ролика необходимо скачать плагин или обновить плеер. Красиво оформляем страницу загрузки, внушаем, что все безопасно, и дело в белой шляпе.
Еще по теме: Как хакеры создают трояны для Андроид
What is Word ransomware?
Word is a new file-locking virus that is actively spreading around the internet. It is noteworthy that Word is originated from another dangerous virus – Dharma ransomware. There are many Dharma virus variants and despite the difference in encryption algorithms, they all have a common goal – block access to user sensitive data and then demand money for a decryption key. Within encryption, it can also delete shadow copies of files and system restore points making file recovery almost impossible. Nonetheless, we are unable to recommend you to pay ransom for the decryption of your files, because there are no guarantees that they send you a decryption tool. In this article, you will find instructions on how to remove Word ransomware and decrypt .word files.
Crysis/Dharma family group
As we mentioned earlier, the virus affects data in such a way so you won’t be able to open files with .id-xxxxxxxx.[vm1iqzi@aol.com].word extension unless they are decrypted. Here, Word ransomware displays a pop-up window and creates FILES ENCRYPTED.txt file. Cybercriminals urge users to contact them via email to know the ransom amount and solve the problem as soon as possible. As usual, cybercriminals offer free decryption of several files to prove that they can really decrypt the victim’s files. Typically, such virus programs encrypt data securely enough so that you have no choice but to purchase decryption tools from cybercriminals. Regular backups will save you from these problems. It is worth noting that the files remain encrypted even after the removal of the ransomware, its deletion only prevents further encryption.
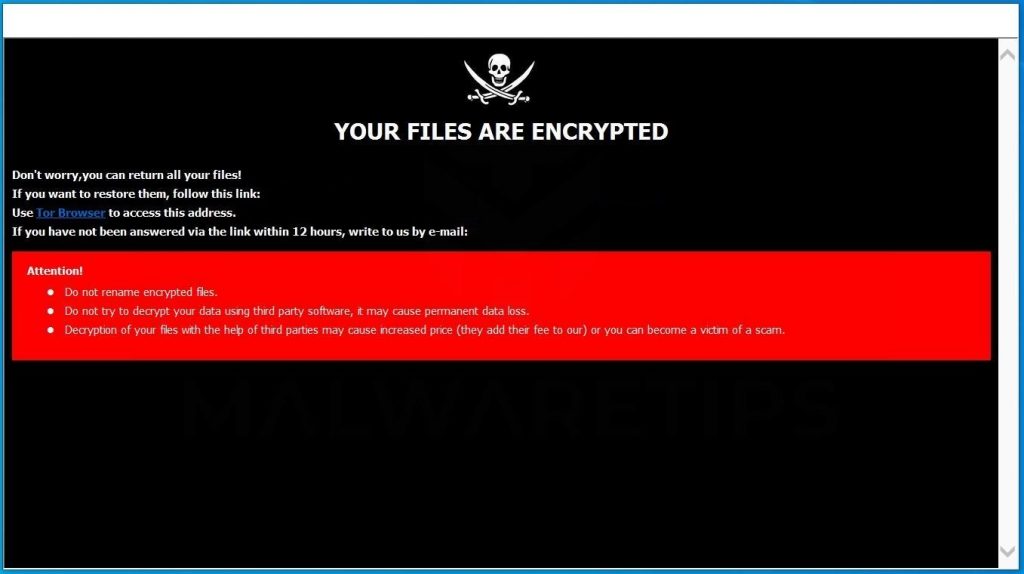
The content of the pop-up window:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail vm1iqzi@aol.com
Write this ID in the title of your message –
In case of no answer in 24 hours write us to these e-mails:vm1iqzi@aol.com
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as a guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 10Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click ‘Buy bitcoins’, and select the seller by payment method and price.
https://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
We strongly recommend not to comply with their requirements because there are no guarantees that you will obtain your files when the transaction happens. On the contrary, there is a high risk of being deceived and simply left with nothing. The only reliable way to solve the problem is to remove Word ransomware from the system using appropriate software in order to stop the malicious actions of the virus and then restore your data from the backup.
The content of FILES ENCRYPTED.txt ransom note:
all your data has been locked us
You want to return?
write email vm1iqzi@aol.com
At the last stage of the infection stage, this ransomware may delete all shadow volumes on your computer. After that, you will not be able to carry out the standard procedure for recovering your encrypted data using these shadow volumes. There are two solutions to remove Word Ransomware and decrypt your files. The first is to use an automated removal tool. This method is suitable even for inexperienced users since the removal tool can delete all instances of the virus in just a few clicks. The second is to use the Manual Removal Guide. This is a more complex way that requires special computer skills.
Screenshot of encrypted by Word virus files:
How Word ransomware gets on my computer?
Cybercriminals use various techniques to deliver the virus to the target computer. Ransomware viruses can infiltrate victims’ computers more than in one or two ways, in most cases, cryptoviral extortion attack is carried out with the help of the following methods:
| Name | Word |
| Type of threat | Ransomware, cryptovirus, file-locking virus |
| File Extension | .[vm1iqzi@aol.com].word |
| Ransom Note | pop-up window, FILES ENCRYPTED.txt |
| Contact | vm1iqzi@aol.com |
| Genealogy | DHARMA Ransomware |
| Detections | Avast (Win32:RansomX-gen [Ransom]), BitDefender (Trojan.Ransom.Crysis.E), ESET-NOD32 (A Variant Of Win32/Filecoder.Crysis.P), Kaspersky (Trojan-Ransom.Win32.Crusis.to), more detections (VirusTotal) |
| Distribution | Spam email attachments, RDP, pirated software, torrent websites, phishing sites |
| Removal Tool |
In order to completely remove ransomware from your computer, you will need to install an antivirus software. We recommend using SpyHunter |
| Recovery Tool |
The only effective method to restore files is to copy them from a saved backup. If you don’t have a suitable backup, you may use third-party recovery software such as Stellar Data Recovery |
Recommended Solution:
-
Removal Tool
-
Recovery Tool
-
Prevention Tool
Try SpyHunter
SpyHunter is a powerful tool that is able to keep your Windows clean. It would automatically search out and delete all elements related to malware. It is not only the easiest way to eliminate malware but also the safest and most assuring one.
The full version of SpyHunter costs $42 (you get 6 months of subscription). By clicking the button, you agree to EULA and Privacy Policy. Downloading will start automatically.
Download SpyHunter
Try Stellar Data Recovery
Stellar Data Recovery is one of the most effective tools that can recover lost and corrupted files — documents, emails, pictures, videos, audio files, and more — on any Windows device. The powerful scan engine can detect compromised files and finally save them to specified destination. Despite its advancedness, it’s very concise and simple so that even the most inexperienced user can figure it out.
Download Stellar Data Recovery
Try MailWasher
Email security is the first line of defense against ransomware viruses. To do this, we recommend that you use MailWasher. MailWasher blocks ransomware viruses coming through spam and phishing, and automatically detects malicious attachments and URLs. In addition, malicious messages can be blocked even before the recipient opens them. Since the main source of the spread of ransomware viruses are infected emails, antispam significantly reduces the risk of a virus appearing on your computer.
Download MailWasher
After the virus is completely removed from your system, you can begin the process of restoring your files.
How to decrypt files infected by Word Ransomware?
Most regrettably, there are no free decryption tools that will be able to decrypt files encrypted by any Dharma Ransomware variants. All of the methods listed below do not guarantee full file recovery. Nevertheless, due to the lack of other ways than to pay the ransom, we advise you to perform them, maybe they will help at least partially restore your data.
Method 1. Restore your files with the help of Recovery Tool

Download Stellar Data Recovery
-
- Run Stellar Data Recovery.
- Select type of files you want to restore and click Next.
-
- Select the drive and folder where your files are located and date that you want to restore them from and press Scan.
-
- Once the scanning process is done, click Recover to restore your files.
-
- After this, select a destination and click Start Saving to save restored data.
Since new ransomware-type viruses appear almost every day, there is no technical possibility to issue a decryptor for each virus. In this case, the recovery tool comes to the rescue. Despite the fact that this is one of the most effective methods in the absence of a decryptor, this is not 100 percent and not the only way.
Method 2. Restore the system using System Restore
Although the latest versions of Word Ransomware can remove system restore files, this method may help you partially restore your files. Give it a try and use standard System Restore to revive your data. The entire process is preferably carried out in Safe Mode with Command Prompt:
For Windows XP/Vista/7 users:
Restart your computer and before your system starts – hit F8 several times. This will prevent system from loading and will show Advanced boot options screen. Choose Safe mode with Command Prompt option from the options list using up and down arrows on your keyboard and hit Enter.
For Windows 8/10 users:
-
- Click the Start button, then select Settings
- Click Update & Security, then select Recovery and click Restart now.
- After your device reboots, go to Troubleshoot > Advanced options >Startup Settings > Restart
- After your PC restarts, you should press F5 key to Enable Safe Mode with Command Prompt.
After the system is loaded in Safe Mode with Command Prompt, do following:
-
- In the Command Prompt window, type cd restore and hit Enter.
-
- Then type rstrui.exe and hit Enter again.
-
- Once a new window shows up, click Next.
-
- Choose the date before the infection appearance and click Next again
-
- In the opened pop-up window, click Yes to start system restore.
Method 4. Roll the files back to the previous version
Previous versions can be copies of files and folders created by Windows Backup (if it is active) or copies of files and folders created by System Restore. You can use this feature to restore files and folders that you accidentally modified or deleted, or that were damaged. This feature is available in Windows 7 and later versions.
- Click the encrypted file and choose Properties
- Open the Previous Version tab
- Select the latest version and click Copy
- Click Restore
How to prevent your system from Ransomware?
No one is safe from infection with a virus that secretly encrypts your data. But in order to minimize this risk, you need to follow the rules:
1. Always make Windows updates on time and keep them up to date. Remember that these updates close the security holes in the system through which the virus can enter your computer.
2. The most efficient way to avoid data loss is of course to make a backup of all important data from your computer. It is enough just to synchronize the necessary folders with one of the cloud services, so as not to be afraid to see the text requiring the payment of bitcoins in exchange for a decryption key. It can be a cloud or a remote hard drive on the network. If you store all your files on the Internet, the likelihood of virus infection will be lower. Do not make copies to external hard drives, as this could damage them.
3. Since spam email is the most popular form of spreading ransomware-type viruses, the user should never open email attachments without first having scanned them with antivirus. Just clicking on the link or opening the attachment can damage the operating system (Windows) in a few minutes, damage important data and infect other machines with the virus.
4. All previous methods do not matter if you do not have a reliable antivirus. The presence of anti-virus protection on your computer can prevent all these unpleasant surprises. Anti-virus protection will protect you from malware, money loss, time loss, invasion of your personal life. Now the antivirus protection is so huge that it is difficult to make a choice in favor of one of them. If you have not decided who to give preference to, we suggest you familiarize yourself with our Top 5 Antivirus Software for Windows
What is .word file virus?
Also referred to as DHARMA ransomware1, it modifies your documents by means of encrypting them and demanding the ransom to be paid allegedly to restore access to them. [[email protected]].word indicates [email protected] as a channel for contacting the ransomware criminals.
The DHARMA ransomware is active again through its new cryptovirus bearing the name of .word. This particular virus family modifies all popular file types by means of adding the .word extension, thus making the data absolutely unavailable. The victims simply cannot open their important documents anymore. The ransomware also assigns its unique identification key, just like all previous representatives of the virus family. As soon the file is encrypted by the ransomware, it obtains a special new extension becoming the secondary one. The file virus also generates a ransom note providing the users want instructions allegedly to restore the data.
word Threat Main Facts
| Name | .word file virus |
| Extension | [[email protected]].word file virus |
| Type | Ransomware |
| Detection | TrojanDownloader:Win32/Cutwail.BT, VirTool:MSIL/Injector.SZ!bit, Graftor.442387 |
| Short Description | The virus modifies the documents on the attacked device through encryption and asks for the ransom to be paid by the victim supposedly to recovery them. |
| Symptoms | The file virus encrypts the data by adding the .word extension, also generating the one-of-a-kind identifier. Note that the [[email protected]].word extension becomes the secondary one. |
| Distribution Method | Spam, Email attachments, Compromised legitimate downloads, Attacks exploiting weak or stolen RDP credentials2. |
| Fix Tool |
GridinSoft Anti-Malware See If Your System Has Been Affected by .word file virus |
.word File Virus – Dharma Ransomware
What Is It and How Did I Get It?
The .word ransomware is most commonly spread by means of a payload dropper. It runs the malicious script that eventually installs the file virus. The threat circulates actively on the web, considering the facts about the ransomware mentioned in the VirusTotal database. The .word ransomware may also promote its payload files through popular social networks and via file-sharing platforms. Alternatively, some free applications hosted on many popular resources may also be disguised as helpful tools, whereas they instead may lead to the malicious scripts that injected the ransomware. Your personal caution to prevent the .word virus attack matters a lot!
.word File Virus is a infection that encrypts your data and presents a frustrating ransomware notice. Below is the screenshot depicting the ransomware note:
Quotation of the scary message
All your files have been encrypted! All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail [email protected] Write this ID in the title of your message XXXXXX In case of no answer in 24 hours write us to theese e-mails:[email protected] You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files. Free decryption as guarantee Before paying you can send us up to 1 file for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.) How to obtain Bitcoins The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price. hxxps://localbitcoins[dot]com/buy_bitcoins Also you can find other places to buy Bitcoins and beginners guide here: hxxps://www.coindesk[dot]com/information/how-can-i-buy-bitcoins/ Attention! Do not rename encrypted files. Do not try to decrypt your data using third party software, it may cause permanent data loss. Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Remove [[email protected]].word File Virus (Dharma)
Reasons why I would recommend GridinSoft3
The is an excellent way to deal with recognizing and removing threats – using Gridinsoft Anti-Malware. This program will scan your PC, find and neutralize all suspicious processes4.
Download GridinSoft Anti-Malware.
You can download GridinSoft Anti-Malware by clicking the button below:
Run the setup file.
When setup file has finished downloading, double-click on the setup-antimalware-fix.exe file to install GridinSoft Anti-Malware on your PC.
An User Account Control asking you about to allow GridinSoft Anti-Malware to make changes to your device. So, you should click “Yes” to continue with the installation.
Press “Install” button.
Once installed, Anti-Malware will automatically run.
Wait for the Anti-Malware scan to complete.
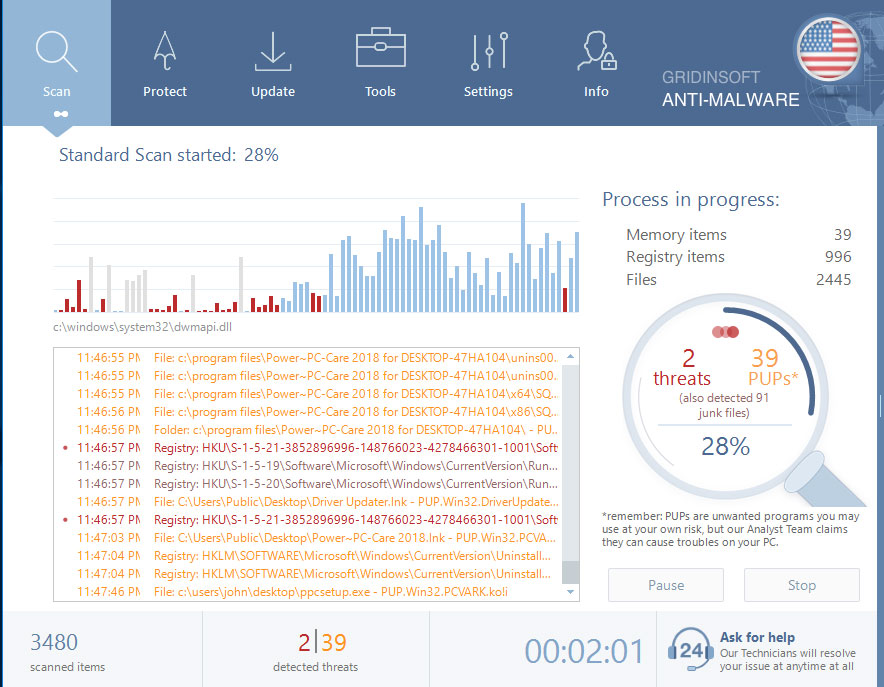
GridinSoft Anti-Malware will automatically start scanning your system for word infections and other malicious programs. This process can take a 20-30 minutes, so I suggest you periodically check on the status of the scan process.
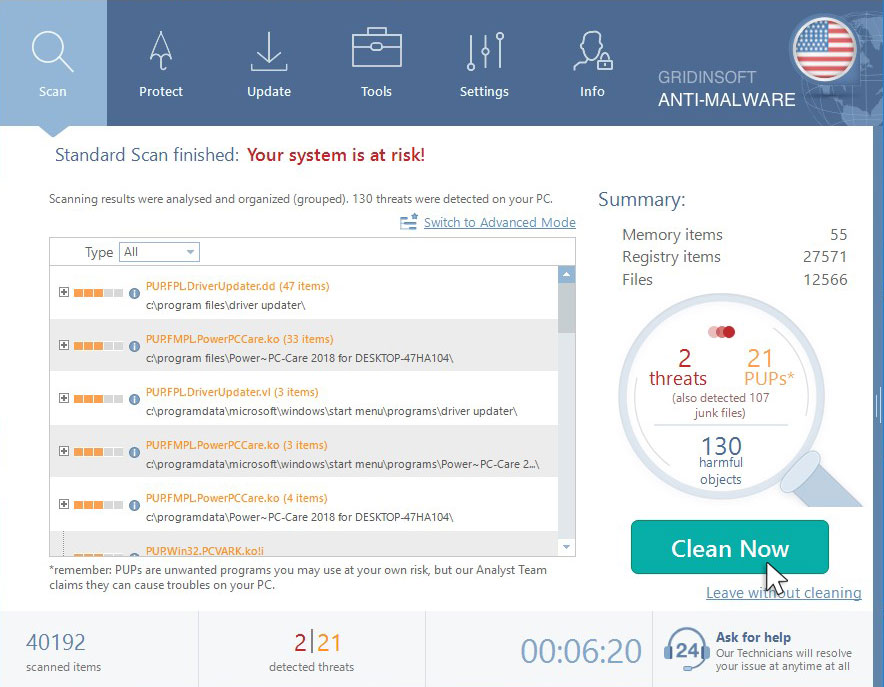
Click on “Clean Now”.
When the scan has completed, you will see the list of infections that GridinSoft Anti-Malware has detected. To remove them click on the “Clean Now” button in right corner.
You can download and use this decrypter that Kaspersky released if you were hit by .[[email protected]].word extension.
You can download and use this decrypter that Avast released or this decrypter that Kaspersky released if you were hit by .word extension.
What the next?
If the guide doesn’t help you to remove word virus, please download the GridinSoft Anti-Malware that I recommended. Also, you can always ask me in the comments for getting help. Good luck!
User Review
4.13 (8 votes)
References
- Read more about Dharma Ransomware: https://howtofix.guide/about-dharma-crysis-ransomware/
- How To Change Remote Desktop (RDP) Port: https://howtofix.guide/change-remote-desktop-port-on-windows-10/
- GridinSoft Anti-Malware Review from HowToFix site: https://howtofix.guide/gridinsoft-anti-malware/
- More information about GridinSoft products: https://gridinsoft.com/products/
You may also like
About the author
Brendan Smith
Journalist, researcher, web content developer, grant proposal editor. Efficient and proficient on multiple platforms and in diverse media. Computer technology and security are my specialties.
Word Ransomware
Ransomware called Word is a new strain of the well-known Dharma cryptovirus. As a ransomware program, Word corrupts computer operating systems and then reaches valuable personal files. As an end goal, Word ransomware has to blackmail its victims into paying a hefty ransom fee to hackers.
An infection with this ransomware will prevent you from opening important files. They will be all marked with the .word extension. Since their code is transformed by a strong cipher, they can be decrypted only with a special key that will revert back the code to its original phase.
You will be presented with two ransom notes that request a ransom payment. Our advice is to skip following hackers’ instructions as they guarantee nothing. Instead, see how to remove the Word virus from your PC and try to restore .word files with some alternative methods.
On this page:
Word RansomwareWord Virus SummaryRemove Word Ransomware
Word Virus Summary
| Name | Word also known as Dharma, CrySiS, Trojan.Ransom.Crysis.E, TrojWare.Win32.Crysis.D@6sd9xy, Trojan-Ransom.Win32.Crusis.to, Ransom:Win32/Wadhrama!hoa |
| Type | Ransomware, Cryptovirus |
| Ransom Demanding Notes | FILES ENCRYPTED.txt and a pop-up window |
| Malicious Extensions | .id-number.[vm1iqzi@aol.com].word |
| Short Description | A data locker ransomware that utilizes strong cihper algorithm to encrypt valuable files stored on the infected computer and then demands a ransom for their decryption. |
| Symptoms | Important files are locked and renamed with three specific extensions. Ransom message appears as desktop wallpaper. Another one stored by a text file appears somewhere on the system. |
| Distribution Method | Spam Emails, Email Attachments, Fake Software Updates, Corrupted Sites |
| Detection Tool |
See If Your System Has Been Affected by malware
Download Malware Removal Tool |
More Details About Word Virus Attack
An attack with the nasty Word virus begins the moment its payload file loads on a computer system. This file tends to land on target systems via shady methods like spam emails with malicious attachments, hacked sites, software cracks, fake software updates, freeware with compromised installers, and others.
Word virus’ access to your machine will enable it to run a long sequence of malicious changes. Those changes will happen in the background of all other running apps. The ransomware program is developed to compromise basic security settings.
Then it becomes able to reach target files and encrypts their code. For the encryption, it uses a sophisticated cipher algorithm. Word virus may encode personal files of all types.
- Audio files.
- Video files.
- Document files.
- Image files.
- Backup files.
- Banking credentials, etc.
Files encrypted by Word ransomware can easily be spotted as they all have three unusual extensions. Their original names will be followed by an ID number, a hackers’ email address, and the extension .word.
It became clear that Word is a cryptovirus based on the infamous Dharma/CrySiS ransomware code. It has lots of predecessors with various strange names such as 2021, Fresh, and WSHLP. The main differences are the extensions they use to mark corrupted files and the cybercriminals’ email address. Word is controlled by fraudsters who use the email vm1iqzi@aol.com. The email helps them to communicate with their victims and extort money from them.
This email could be found in the ransom messages created by the Word virus. The main message appears as a pop-up window on PCs infected with the threat. The messages aim to trick you into buying and transferring cryptocurrency to hackers’ wallet. We know that the decryption of your .word files is of paramount importance, but we still do not recommend that you act according to hackers’ expectations.
Remove Word Ransomware
The so-called Word ransomware is a threat with a highly complex code that disrupts system security to encrypt personal files. Hence, you could securely use the infected system after removing all malicious files and objects created by the ransomware. The steps presented in the ransomware removal guide below will help you with the complete removal process. Beware that manual ransomware removal is suitable for more experienced computer users. If you don’t feel comfortable with the manual steps, navigate to the guide’s automatic part. It is also worth mentioning that personal data remains encrypted even after the complete removal of Word ransomware. Its removal only prevents it from causing further encryptions and security issues.
Step 5 from our Word ransomware removal guide presents alternative data recovery methods that may be efficient for the recovery of encrypted files. Beware that you should make copies of all encrypted files and save them on a flash drive, for example, before the beginning of the recovery process.
Gergana Ivanova
Highly motivated writer with 5+ years of experience writing for ransomware, malware, adware, PUPs, and other cybersecurity-related issues. As a writer, I strive to create content that is based on thorough technical research. I find joy in the process of creating articles that are easy to understand, informative, and useful. Follow me on Twitter (@IRGergana) for the latest in the field of computer, mobile, and online security.
More Posts
Follow Me:
Step 1: Boot Your PC In Safe Mode to isolate and remove Word Virus
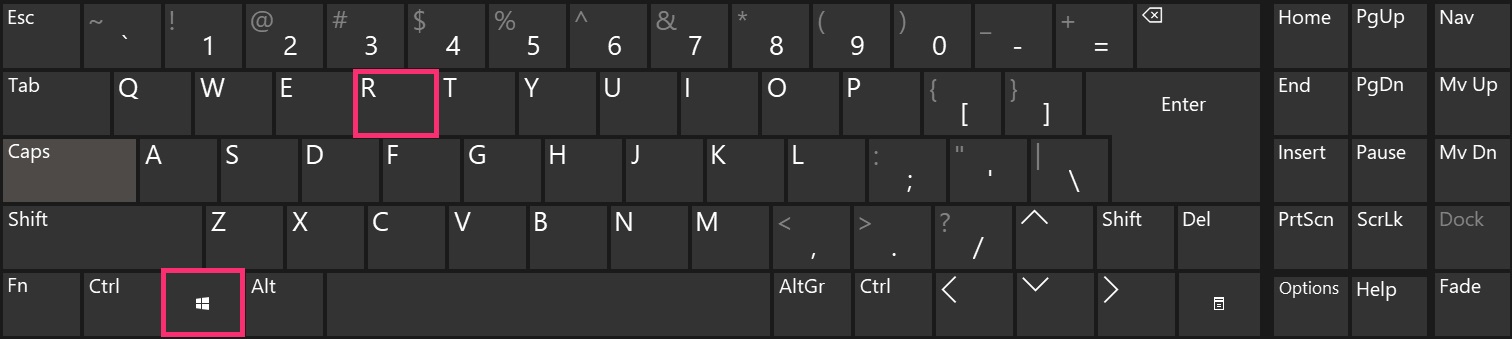
1. Hold Windows Key + R.
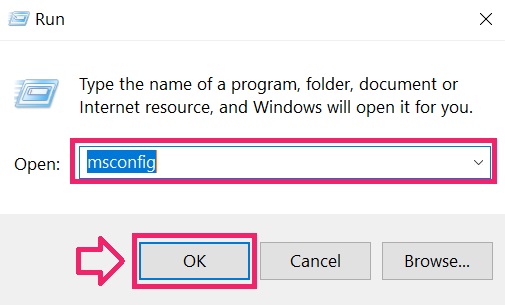
2. The «Run» Window will appear. In it, type «msconfig» and click OK.
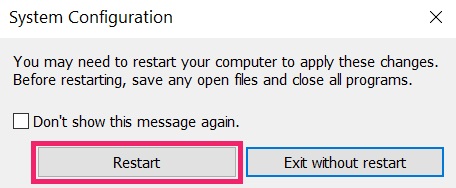
3. Go to the «Boot» tab. There select «Safe Boot» and then click «Apply» and «OK».
Tip: Make sure to reverse those changes by unticking Safe Boot after that, because your system will always boot in Safe Boot from now on.
4. When prompted, click on «Restart» to go into Safe Mode.
5. You can recognise Safe Mode by the words written on the corners of your screen.
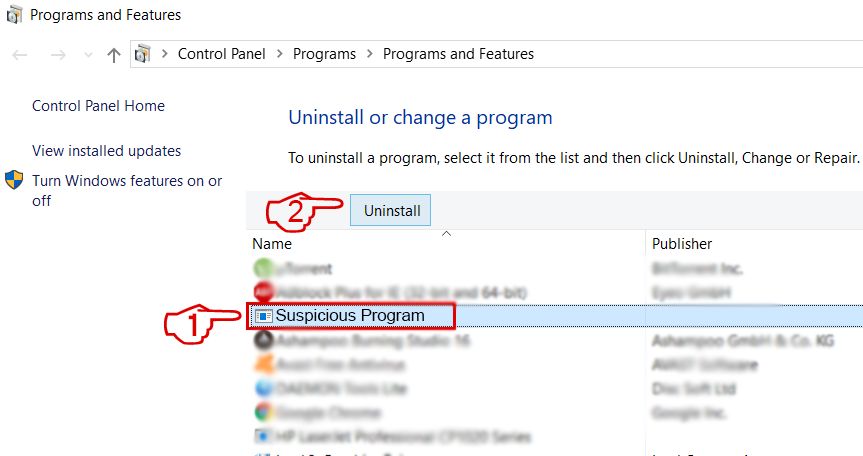
Step 2: Uninstall Word Virus and related malware from Windows
Here is a method in few easy steps that should be able to uninstall most programs. No matter if you are using Windows 10, 8, 7, Vista or XP, those steps will get the job done. Dragging the program or its folder to the recycle bin can be a very bad decision. If you do that, bits and pieces of the program are left behind, and that can lead to unstable work of your PC, errors with the file type associations and other unpleasant activities. The proper way to get a program off your computer is to Uninstall it. To do that:
1. Hold the Windows Logo Button and «R» on your keyboard. A Pop-up window will appear.
2. In the field type in «appwiz.cpl» and press ENTER.
3. This will open a window with all the programs installed on the PC. Select the program that you want to remove, and press «Uninstall»
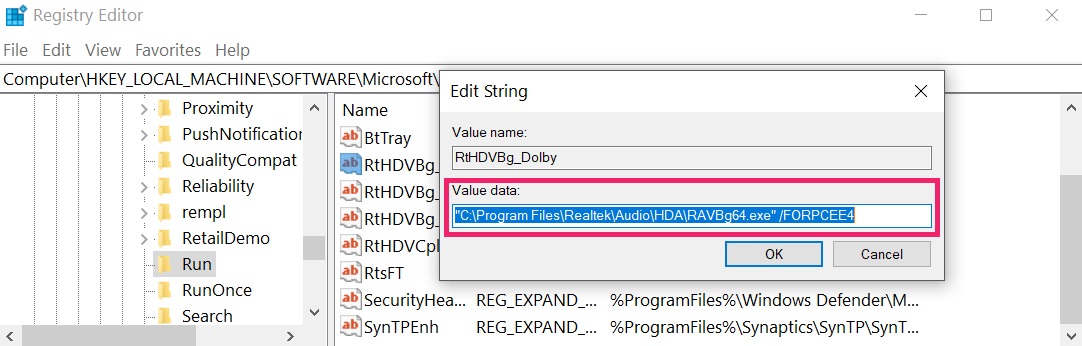
Step 3: Clean any registries, created by Word Virus on your computer.
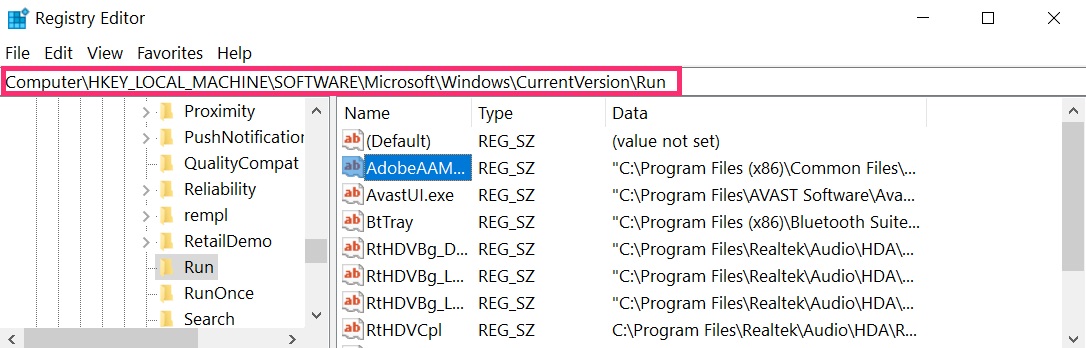
The usually targeted registries of Windows machines are the following:
- HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
- HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRunOnce
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRunOnce
You can access them by opening the Windows registry editor and deleting any values, created by Word Virus there. This can happen by following the steps underneath:
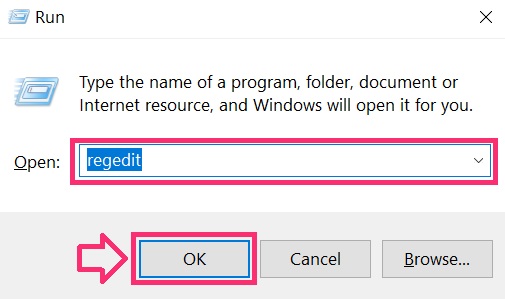
1. Open the Run Window again, type «regedit» and click OK.
2. When you open it, you can freely navigate to the Run and RunOnce keys, whose locations are shown above.
3. You can remove the value of the virus by right-clicking on it and removing it.
IMPORTANT!
Before starting «Step 4», please boot back into Normal mode, in case you are currently in Safe Mode.
This will enable you to install and use SpyHunter 5 successfully.
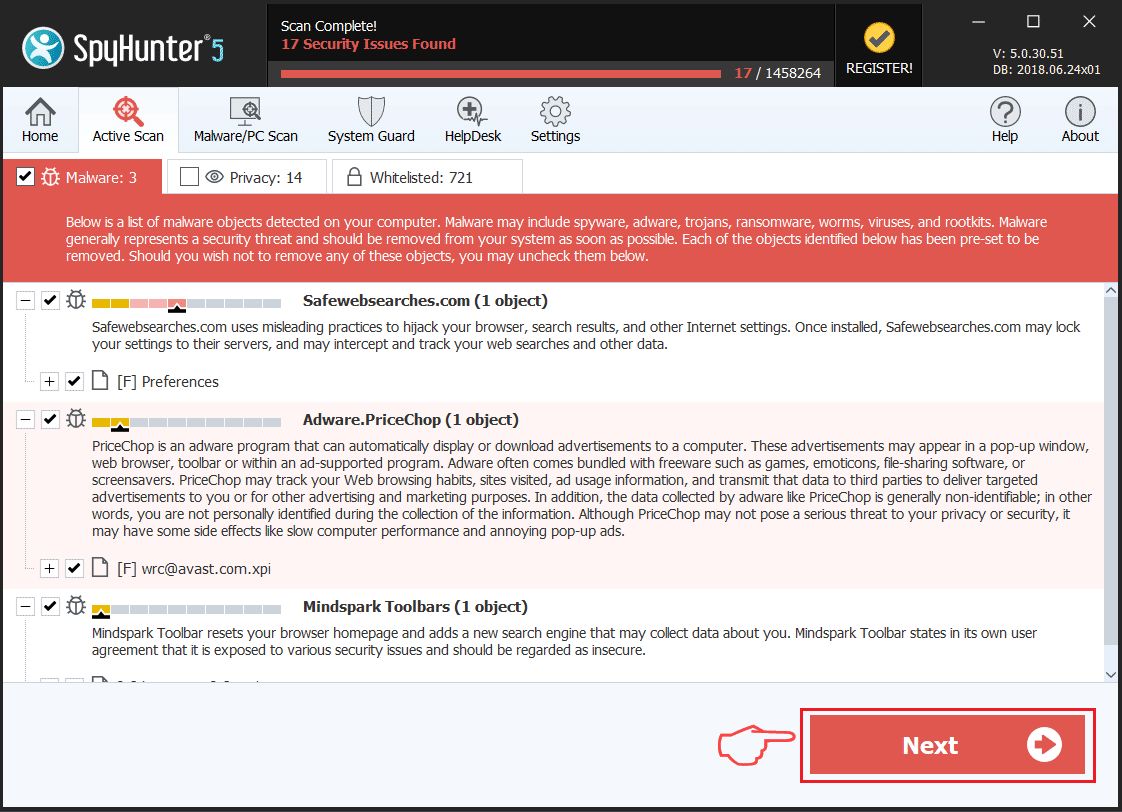
Step 4: Scan for Word Virus with SpyHunter Anti-Malware Tool
1. Click on the «Download» button to proceed to SpyHunter’s download page.
It is recommended to run a scan before purchasing the full version of the software to make sure that the current version of the malware can be detected by SpyHunter. Click on the corresponding links to check SpyHunter’s EULA, Privacy Policy and Threat Assessment Criteria.
2. After you have installed SpyHunter, wait for it to update automatically.
3. After the update process has finished, click on the ‘Malware/PC Scan’ tab. A new window will appear. Click on ‘Start Scan’.
4. After SpyHunter has finished scanning your PC for any files of the associated threat and found them, you can try to get them removed automatically and permanently by clicking on the ‘Next’ button.
If any threats have been removed, it is highly recommended to restart your PC.
Ransomware Automatic Removal — Video Guide
Step 5 (Optional): Try to Restore Files Encrypted by Word Virus.
Ransomware infections and Word Virus aim to encrypt your files using an encryption algorithm which may be very difficult to decrypt. This is why we have suggested a data recovery method that may help you go around direct decryption and try to restore your files. Bear in mind that this method may not be 100% effective but may also help you a little or a lot in different situations.
1. Download the recommended Data Recovery software by clicking on the link underneath:
Simply click on the link and on the website menus on the top, choose Data Recovery — Data Recovery Wizard for Windows or Mac (depending on your OS), and then download and run the tool.
Word Virus FAQ
What is Word Virus Ransomware?
Word Virus is a ransomware infection — the malicious software that enters your computer silently and blocks either access to the computer itself or encrypt your files.
Many ransomware viruses use sophisticated encryption algorithms to make your files inaccessible. The goal of ransomware infections is to demand that you pay a ransom payment to get access to your files back.
Can Word Virus Ransomware Damage My Computer?
Yes, ransomware can damage your computer. Ransomware is a malicious software that is designed to block access to your computer or files until a ransom is paid. It can encrypt your files and make them inaccessible, preventing you from using your computer or accessing your data. Ransomware can also damage your system, corrupt data and delete files, resulting in the permanent loss of important files.
Should I Ignore Ransomware, like Word Virus?
No, you should never ignore ransomware. Ransomware can encrypt your data and block access to your computer, making it impossible to access your files until you pay a ransom. Ignoring ransomware could lead to the permanent loss of your data, as well as the potential for the ransomware to spread to other computers on your network. Additionally, paying the ransom does not guarantee that your data will be recovered. The best way to protect yourself is to invest in robust cyber security measures, such as backup solutions and anti-malware software.
How Does Word Virus Ransomware Infect My Computer?
Via several ways.Word Virus Ransomware infects computers by being sent via phishing emails, containing virus attachment.
This attachment is usually masked as an important document, like an invoice, bank document or even a plane ticket and it looks very convincing to users.
After you download and execute this attachment, a drive-by download occurs and your computer is infected with the ransomware virus.
Another way you may become a victim of Word Virus is if you download a fake installer, crack or patch from a low reputation website or if you click on a virus link. Many users report getting a ransomware infection by downloading torrents.
How to Open .Word Virus files?
You can’t. At this point, the .Word Virus files are encrypted. You can only open them once they are decrypted using a specific decryptionkey for the particular algorithm.
What to Do If Ransomware Decryptor Does Not Work?
Do not panic, and backup the files. If a decryptor did not decrypt your .Word Virus files successfully, then do not despair, because this virus is still new.
One way to restore files, encrypted by Word Virus ransomware is to use a decryptor for it. But since it’s a new virus, be advised that the decryption keys for it may not be out yet and available to the public. We will update this article and keep you posted as soon as this decryptor is released.
Can I Restore «.Word Virus» Files (Other Methods)?
Yes, sometimes files can be restored. We have suggested several file recovery methods that could work if you want to restore .Word Virus files.
These methods are in no way 100% guaranteed that you will be able to get your files back. But if you have a backup, your chances of success are much greater.
How Do I Get Rid of Word Virus Ransomware Virus?
The safest way and the most efficient one for the removal of this ransomware infection is the use a professional anti-malware program. It will scan for and locate Word Virus ransomware and then remove it without causing any additional harm to your important .Word Virus files.
Also, keep in mind that viruses like Word Virus ransomware also install Trojans and keyloggers that can steal your passwords and accounts. Scanning your computer with anti-malware software will make sure that all of these virus components are removed and your computer is protected in the future.
What to Do If I Cannot Recover Ransomware Encrypted Files?
There is still a lot you can do. If none of the above methods seem to work for you, then try these methods:
-Try to find a safe computer from where you can can login on your own line accounts like One Drive, iDrive, Google Drive and so on.
-Try to contact your friends, relatives and other people so that they can check if they have some of your important photos or documents just in case you sent them.
-Also, check if some of the files that were encrypted it can be re-downloaded from the web.
-Another clever way to get back some of your files is to find another old computer, a flash drive or even a CD or a DVD where you may have saved your older documents. You might be surprised what will turn up.
-You can also go to your email account to check if you can send any attachments to other people. Usually what is sent the email is saved on your account and you can re-download it. But most importantly, make sure that this is done from a safe computer and make sure to remove the virus first.
More tips you can find on our forums, where you can also asks any questions about your ransomware problem.
How to Report Ransomware to Authorities?
Can You Prevent Word Virus Ransomware from Encrypting Your Files?
Yes, you can prevent ransomware. The best way to do this is to ensure your computer system is updated with the latest security patches, use a reputable anti-malware program and firewall, backup your important files frequently, and avoid clicking on malicious links or downloading unknown files. In addition, it is also important to keep your passwords secure and to avoid visiting websites or downloading applications from untrusted sources. Finally, ensure you have adequate backup and recovery procedures in place to restore your system to its pre-attack state, should a ransomware attack occur.
Can Word Virus Ransomware Steal Your Data?
Yes, in most cases ransomware will steal your information. It is a form of malware that steals data from a user’s computer, encrypts it, and then demands a ransom in order to decrypt it. In many cases, the malware authors or attackers will threaten to delete the data or publish it online unless the ransom is paid. This means that if a user is infected with ransomware, their data can be stolen and held for ransom. It is important to be aware of this threat and take precautions to protect yourself and your data.
Can Ransomware Affect WiFi?
Yes, ransomware can affect WiFi networks, as malicious actors can use it to gain control of the network, steal confidential data, and lock out users. If a ransomware attack is successful, it could lead to a loss of service and/or data, and in some cases, financial losses.
Should I Pay Ransomware?
No, you should not pay ransomware extortionists. Paying them only encourages criminals and does not guarantee that the files or data will be restored. The better approach is to have a secure backup of important data and be vigilant about security in the first place.
What Happens If I Don’t Pay Ransom?
If you don’t pay the ransom, the hackers may still have access to your computer, data, or files and may continue to threaten to expose or delete them, or even to use them to commit cybercrimes. In some cases, they may even continue to demand additional ransom payments.
Why Is the Ransom Paid in Crypto?
Cryptocurrency is a secure and untraceable form of payment, making it the ideal choice for ransom payments. It is difficult to trace, and the transactions are almost instantaneous. This means it is nearly impossible for authorities to track the payment and recover the money.
Can Ransomware Be Detected?
Yes, ransomware can be detected. Anti-malware software and other advanced security tools can detect ransomware and alert the user when it is present on a machine. It is important to stay up-to-date on the latest security measures and to keep security software updated to ensure ransomware can be detected and prevented.
Do Ransomware Criminals Get Caught?
Yes, ransomware criminals do get caught. Law enforcement agencies, such as the FBI, have been successful in tracking down and prosecuting ransomware criminals in the US and other countries. As ransomware threats continue to increase, so does the enforcement activity.
What is a File Virus and How Do You Remove it?
A «file virus» (ransomware) is a type of malicious software that infects a computer system and encrypts its files and data, preventing the user from accessing them unless they pay a ransom. The virus is usually spread through malicious links, emails, and downloads from untrusted websites. To remove such a virus, it is best to use professional security software to detect and remove it, as well as to restore any encrypted files. It is also important to practice safe computing by avoiding suspicious links, emails, and downloads, and keeping your computer and software up to date with the latest security patches.
Different Types of File Viruses and How to Understand Them?
File viruses are a type of malicious software that can attach themselves to files, such as documents, spreadsheets, and images, and then spread themselves to other computers. The most common types of file viruses are boot sector, macro, file-infecting (ransomware), and multipartite. Each type of virus has its own set of characteristics and behaviors, which can help users identify them and take the necessary steps to protect their data from infection.
What Steps Should You Take to Protect Your Computer from File Viruses?
To protect your computer from file viruses, the first step is to install up-to-date antivirus software. Make sure you keep the software updated and run regular scans to detect and remove any viruses. Additionally, you should be careful when downloading and opening files from unknown sources. If you receive an email with an attachment, be sure to scan the file before opening it. Finally, you should back up all of your important data regularly in case a virus wipes out your files.
How to Identify and Remove Common File Viruses?
Identifying and removing common file viruses can be a tricky process. The first step is to ensure you have an up-to-date anti-virus program installed on your computer. This will help to identify any malicious software on your system. Once identified, it is important to remove the virus as soon as possible.
To do this, you can use a variety of tools such as anti-virus scanners, malware removal programs and system restore points. It is also important to keep your computer up-to-date with the latest security patches to protect your system from future infections.
How to Diagnose and Treat File Viruses?
Ransomware file viruses are a type of malicious software that can cause serious damage to a computer system. To diagnose and treat a ransomware file virus, you must first identify the type of virus and its source. Once identified, you can then use an antivirus program to scan the system and remove the malicious files. Finally, you should create a backup of your system in case the virus returns and update your system’s security settings to prevent future infections.
What is the Most Common File Virus?
The most common ransomware virus is called CryptoLocker. It is a malicious software that encrypts files on a computer and demands a ransom in order to unlock them. It is spread through malicious emails, malicious attachments and links, and other malicious websites. CryptoLocker is considered one of the most dangerous ransomware viruses because it can encrypt important documents and data, making them inaccessible unless the ransom is paid.
What Causes File Viruses and How Can They Be Prevented?
File viruses are malicious software that infect computers and encrypt data until a ransom is paid. These viruses are typically spread through malicious emails, websites, and software downloads. To prevent them, it is important to only download software and documents from trusted sources, keep your operating system and applications up to date, and use a reliable anti-malware program.
How to Repair Corrupted Files Due to File Viruses?
Repairing corrupted files due to file viruses is possible, but it requires the use of specialized file recovery or decryptor software. The first step is to scan the system for malicious files and then use the software to repair any affected files. Additionally, it is important to ensure that the system is regularly updated and scanned for any new threats. Finally, it is important to ensure that the system is regularly backed up so that any lost files can be recovered.
How To Avoid File Viruses When Downloading Files From the Internet?
To protect yourself from file viruses when downloading from the web, firstly, only download files from trusted websites or sources. Additionally, use anti-virus software or firewalls to help protect your system from malicious software. Before downloading a file, always make sure to scan it with an anti-malware program to check for any viruses. It is also important to keep your operating system up to date with the latest security patches. Finally, make sure to backup your important files regularly to ensure you can restore them in the event of a ransomware attack.
About the Word Virus Research
The content we publish on SensorsTechForum.com, this Word Virus how-to removal guide included, is the outcome of extensive research, hard work and our team’s devotion to help you remove the specific malware and restore your encrypted files.
How did we conduct the research on this ransomware?
Our research is based on an independent investigation. We are in contact with independent security researchers, and as such, we receive daily updates on the latest malware and ransomware definitions.
Furthermore, the research behind the Word Virus ransomware threat is backed with VirusTotal and the NoMoreRansom project.
To better understand the ransomware threat, please refer to the following articles which provide knowledgeable details.
References
1. How to Recognize Spam Emails with Ransomware
2. How Does Ransomware Encryption Work?
3. How to Decrypt Ransomware Files
4. Ransomware Getting Greedier and Bigger, Attacks Increase by 40%
5. 1 in 5 Americans Victim of Ransomware
Attention! SensorsTechForum strongly recommends that all malware victims should look for assistance only by reputable sources. Many guides out there claim to offer free recovery and decryption for files encrypted by ransomware viruses. Be advised that some of them may only be after your money.
As a site that has been dedicated to providing free removal instructions for ransomware and malware since 2014, SensorsTechForum’s recommendation is to only pay attention to trustworthy sources.
How to recognize trustworthy sources:
- Always check «About Us» web page.
- Profile of the content creator.
- Make sure that real people are behind the site and not fake names and profiles.
- Verify Facebook, LinkedIn and Twitter personal profiles.
-
#1
Poster here to attract a larger audience base !
Hello all,
As my title says it all. Is that even possible? My Landlord’s computer recently had an attack from a virus called CryptoLocker. Apparently it claims that all (Excel and word) files on the computer including ones that were on a removable disk (that was connected at the time of attack) has been encrypted. It says encrypted, but technically it is not. It has just corrupted the files. Not sure how to go around fixing it. He is quiet old and does not know anything about having multiple backups. So he is at loss, so am I. I thought to give a helping hand…
The above are the two errors that come up for all the documents. The virus has been removed using multiple malware/antivirus program. Unfortunately none of the documents could be recovered.
I am trying almost everything that could be found on the internet, the only thing I have not tried is complete uninstall of the MS package. The problem is he does not have the Key to the MS office package. So reinstallation would be a pain.
I have followed most of the steps provided on:
http://www.techrepublic.com/blog/10-things/10-plus-ways-to-recover-a-corrupted-word-document/ (except for step 10, I am looking at 3rd party softwares right now)
http://office.microsoft.com/en-gb/w…text-from-a-damaged-document-HP005189610.aspx
http://support.microsoft.com/kb/918429
All proved to be in vain !
Has anyone had this kinda attack. Is there any hope for recovering?
-
openErr.jpg
57.8 KB · Views: 1,920
Rx_
Nothing In Moderation
-
#2
Could you tell us what virus checker found Crypto Locker?
I read that all virus checks are not equal. I use three different ones out of total fear.
I thought that I had something too on some files I left open too often. It turned out that the wiring to my electrical outlet was faulty. The constant brown-outs that were barely noticeable on the desklamp. But, it eventually destroyed two internal PC power supplies.
The excel file with many tabs, was left open. I now close spreadsheets. They won’t open as excel. All my other excel files (that were not left open) work just fine.
I searched in vain for a solution. These were really big, detailed files.
So, if you find anything, please post it. Please.
-
#3
CryptoLocker is a nasty piece of $***. The Gaurdian has covered a recent article on this issue.
Unfortunately all is lost ! It says only 3% of the victims paid the money, however it did not say how many actually got their data back.
Well one lesson to take away from this is 10 ways to beat CryptoLocker
-
#4
Can a virus corrupt Excel/Word file
Certainly yes! A computer virus can easily corrupt a file by deleting some part or by overwriting the file. Therefore, it is always recommended to use an Antivirus program to avoid virus attacks.
The errors shown above definitely indicate corruption in the files. As you have mentioned that you are looking for third-party recovery software right now, I would recommend you some best software here.
You can try SysInfoTools products here to recover your data from corrupt Excel and Word files. I will suggest you to check demo version of these SysInfoTools software:
- SysInfoTools MS Excel XLSX Recovery software to recover data from corrupt Excel spreadsheets
- SysInfoTools MS Word DOC Repair and SysInfoTools MS Word DOCX Recovery and to recover data from corrupt Word documents.
These software are available with free demo version which can be used to examine the software before buying the full version.
Thanks.
-
#5
Certainly yes! A computer virus can easily corrupt a file by deleting some part or by overwriting the file. Therefore, it is always recommended to use an Antivirus program to avoid virus attacks.
The errors shown above definitely indicate corruption in the files. As you have mentioned that you are looking for third-party recovery software right now, I would recommend you some best software here.
You can try SysInfoTools products here to recover your data from corrupt Excel and Word files. I will suggest you to check demo version of these SysInfoTools software:
- SysInfoTools MS Excel XLSX Recovery software to recover data from corrupt Excel spreadsheets
- SysInfoTools MS Word DOC Repair and SysInfoTools MS Word DOCX Recovery and to recover data from corrupt Word documents.
These software are available with free demo version which can be used to examine the software before buying the full version.
Thanks.
I would not suggest any third party tool. Please peform manual operation. There are many manual operations available by Microsoft free of cost. If error still persist then you can provide answer to Social Technet forum. Here so many MVP’s will provide correct answer.
@jon_R Please don’t spread spam here.