raw – mature, ripe, adult, seasoned.
useful – useless, worthless, unserviceable, valueless, unproductive, ineffectual, idle, fruitless.
14. Name all possible word expressions with following verbs and nouns:
| to process | characters | to display | to set up |
| to install | a computer | a keyboard | data |
| information | to type | a floppy disk | to house |
| a mouse | instruction | input | procedure |
| to perform | device | to store | output |
15. Complete the sentences with suitable compounds from this list.
| expansion slots
magnification software |
database
voice recognition screen reader |
websites
word processor |
1. …. can enlarge text appearing on the screen by up to 16 times.
2. Blind users can’t use a typical … to write letters or faxes. They need Braille and a speech-synthesis system.
3. A … allows blind users to hear the text from the screen.
4. … interprets human speech, transforming the words into digitized text.
5. … let users install expansion boards (modems, graphics boards, etc.) to improve the computer system.
6. A … contains a set of structured data.
7. There are … which give information about assistive technologies for the disabled.
16. Read and translate the following expressions.
| hardware pieces
to produce hardware to process information word processor a disk drive to type a letter to press any key to read a manual carefully to produce the software a screen of the display a long pointer 3½-inch diskette temporary storage system spinning platters hard disk |
to communicate with a computer
to display a character to put all the files on the table a floppy disk to refer to the experimental data a great amount of information (data) the access to this important information to access the main highway to be compatible with most computers the compatibility of computers nonmagnetic technology a pointing device display monitor (screen) two inches square diskette drive |
17. Match the following:
|
|
|
|
|
a) nonvolatile, nonmodifiable computer memory, used to hold programmed instructions to the system.
b) the part of a television or computer on which a picture is formed or information is displayed.
c) rigid disk coated with magnetic material, for storing computer programs and relatively large amounts of data.
d) an electronic device that makes possible the transmission of data to or from computer via telephone or other communication lines.
e) a set of keys, usually arranged in tiers for operating a typewriter, typesetting machine, computer terminal, or the like.
f) volatile computer memory, used for creating, loading, and running programs and for manipulating and temporarily storing data; main memory.
g) central processing unit: the key component of a computer system, containing the circuitry necessary to interpret and execute program instructions.
h) a palm-sized device equipped with one or more buttons, used to point at and select items on a computer display screen and for controlling the cursor by means of analogous movement on a nearby surface.
i) a thin, usually flexible plastic disk coated with magnetic material, for storing computer data and programs.
g) the system of the computer component in which information is stored.
18. Try to complete the following crossword.
1. The device, which function is to execute program instruction and coordinate the activities of all other units.
2. A CRT device which displays the computer output.
3. The process of keeping information on a computer.
4. The section which holds the instructions and data currently being processed.
5. Disks made of a flexible plastic material upon which data is stored on magnetic tracks.
6. A small input device with a ball underneath that is rolled by the user to specify the position of the cursor or to make choices from the menu.
7. The component in the processor or other chip which holds the instruction from the memory while it is being executed.
8. An object or a piece of equipment that has been designed to do a particular job.
9. An output device which converts data into printed form.
| 1 | ||||||||||
| 3 | ||||||||||
| 4 | ||||||||||
| 5 | 2 | |||||||||
| 6 | ||||||||||
| 7 | ||||||||||
| 8 | ||||||||||
| 9 | ||||||||||
Word-building
Model 12
| Prefix | Meaning | Examples |
| deci-
hexadeci- kilo- mega- giga- mini- micro- bi- tri- multi- mono- |
ten
sixteen one thousand (1,000) (1,024 in binary: 210) large; one million very large; one thousand million small very small two three many one |
decimal, decimalize, decibel
hexadecimal kilocycle, kilogram(me), kilowatt megahertz, megalith, megaton gigantic, gigabyte, gigahertz minibus, minimum, minimize microfilm, microphone, microwave bidirectional, bidimensional, binary tripartite, tricycle, trilingual multi-racial, multi-user, multitasking monologue, monosyllable, monolingual |
Model 13
Compound adjectives
| battery-powered systems | hands-free operations | waist-mounted computer | head-mounted display | voice-activated device |
19. Explain these expressions, taking into account the prefixes and root word, using the model 12.
Example: the binary system — the binary system is a notation which uses two digits, 0 and 1.
| 1. a minicomputer
2. a microcomputer 3. the decimal system 4. the hexadecimal system 5. a multi-user configuration |
6. a bidimensional chessboard
7. a tricycle 8. a monochrome computer 9. a CPU with 256 MB of RAM 10. a document of 3 kilobytes |
20. Prefixes are commonly used in computer science. With the help of a dictionary, find two additional examples for each prefix.
super- more than super-computer
hyper- extremely hyper-media
mini- small mini-computer
micro- very small micro-computer
semi- partly, half semi-conductor
ultra- beyond ultra-modern
uni- one…………… unilateral
mono- one…………… monochromatic
kilo- thousand…….. kilobit
21. Think of suitable compound nouns for these definitions.
Example: A device which displays or prints the output — An output device.
- A secret word used to receive e-mail — ………………………………….
- A pool that we swim in — ………………………………………………..
- A book which has cheques — …………………………………………….
- A room where you eat meals — …………………………………………..
- Lights used to control the traffic — ……………………………………….
- A card used instead of coins to make phone calls — ………………………
22. Making wordwebs will help you to organize and remember vocabulary. Use the words in the box to make three different wordwebs with compounds.
| floppy
optical soft |
error
free designer |
mail
firm hard |
share
pal directory |
word
site drive |
page
compact server |
23. Find the expression from the model 13 in the text and explain their meaning.
The Mail-to-Blogger «Secret» Word Is An Address
Some blog owners use Mail-to-Blogger, for publishing to their blogs, without considering the issues.
Some owners can’t get Mail-to-Blogger to work.
I get
Delivery to the following recipient failed permanently:
or
I don’t get any error — and the post never shows up in my Posts list.
Other owners have no problems getting theirs to work, and later find posts that they didn’t send — and don’t appreciate.
Where did all of the spam come from?
Using Mail-to-Blogger seems simple — but maybe should not be treated so. The Mail-to-Blogger email address, at Settings — Mobile and email, is a major part of the challenge, in this case.
The legendary Mail-to-Blogger «secret» word has two complementary — and competing — functions.
- It’s an email address.
- It’s a password.
You need to keep both requirements in mind — and balance the two, carefully.
The «secret» word is an email address.
Email addresses need to be kept simple. Similar to URLs, remember that any email, that you send, will be passing through various email systems.
- You (and any other authors) will send email, through an outgoing email system.
- Blogger will receive email, through the Google email system.
- Depending upon the location of the system that you (and the other blog authors) use, there could be other email systems.
- Each email system will have its own rules, for accepting and / or translating addresses.
If you want your email to get to Blogger — and to your blog — you will want to keep the 12 to 24 characters simple.
- 26 lower case letters, «a» — «z».
- 10 digits, «0» — «9».
- Possibly a dash («—«), dot («.«), and / or underscore («_«).
- Begin and end any «secret» word with an alphanumeric character, only. No leading or trailing dashes, dots, or underscores. Remember, the format of the Mail-to-Blogger address is «public.private@blogger.com» (and «private» is the «secret» word).
- No upper case letters, no special characters, and no non «Roman» alphabetic characters.
WikiPedia: Email address notes
Organizations are free to restrict the forms of their own email addresses as desired, e.g., Windows Live Hotmail, for example, only allows creation of email addresses using alphanumerics, dot (.), underscore (_) and hyphen (-).
If you want to use Mail-to-Blogger successfully, be conservative with the address.
The «secret» word is a password.
Passwords need to be complex, and non guessable.
- First, do not use details from your real life, like your social security number, street address, name of husband / wife, and so on. If you can remember it, the bad guys can — and will — guess it.
- Second, avoid words found in the dictionary of your native language. Dictionary based password guessing is a very popular technique, used by many hackers.
- 12 to 24 character random strings, combining lower case letters (26 character, «a» — «z»), and numbers (10 character, «0» — «9»), are best. It’s your blog, just know the risks — and learn to live with the limitations. See WikiPedia: Password strength, for more details.
- See Blogger Help: Post via email, for general guidelines — but consider the password character limitations too.
You want any Mail-to-Blogger posts to be published, so keep the character set simple. You want Mail-to-Blogger to be secure, so keep it non guessable. Keep your blog under your control — but be able to publish to it, as necessary.
- Authentication
- Fingerprints
- Privacy Levels
- Multiple Sessions
Authentication
You’ve probably received email from people pretending to be banks, credit
agencies, even wealthy Nigerian expatriates. People lie about who they
are all the time on the Internet. Authentication is a way to make
sure that nobody can lie to you about who they are when they use OTR.
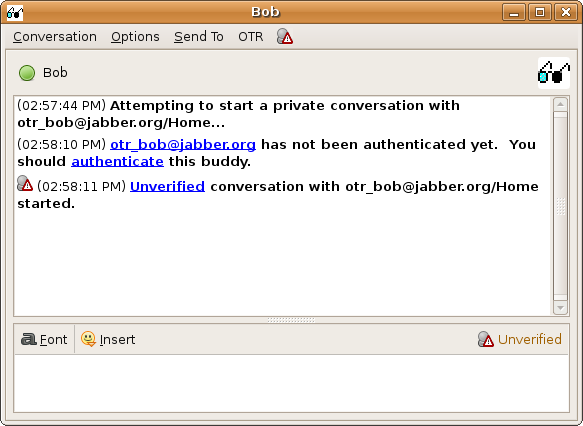
When to authenticate
You should authenticate a buddy the very first time that you talk to
them using OTR. If you don’t, then you can’t really be sure that
someone else isn’t impersonating them or trying to listen in on your
conversation. However, once you’ve authenticated your buddy, you
don’t have to do it again. OTR will automatically do the authentication
for all of your future conversations with that buddy.
The only exceptions occur when your buddy switches between multiple
computers or multiple IM accounts. In this case, you will need to
authenticate once for each computer and account. Once you’ve done this,
your buddy can freely use any of the computers you’ve authenticated them
on, and OTR will recognize them automatically. If your buddy uses
a new computer or account that OTR does not recognize, a message will pop up
in your conversation window telling you about it:
How to authenticate
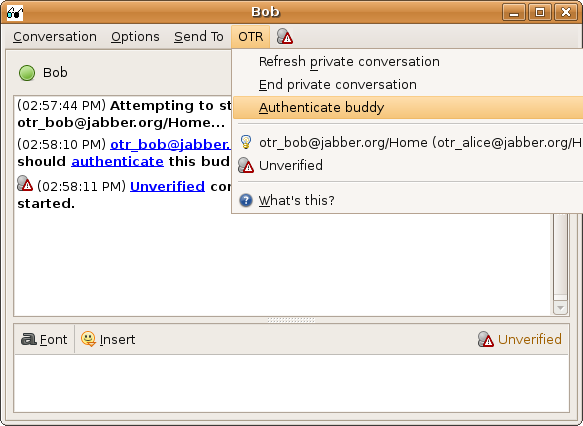
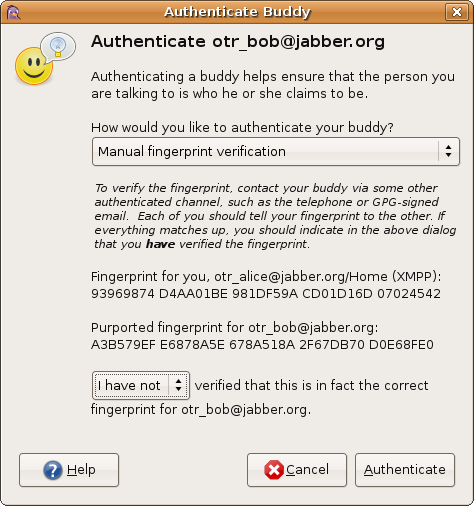
OTR provides three ways to authenticate your buddy:
- Question and answer
- Shared secret
- Manual fingerprint verification
To start the authentication process, you need to first be
communicating with your buddy in the «Unverified» or «Private»
states. [Note that the «Private» state indicates that you have
already successfully authenticated your buddy, and it is not
necessary to do it again.] Choose «Authenticate buddy» from the OTR
menu.
The Authenticate Buddy dialog will pop up. Use the combo box
to select which of the three authentication methods you would like
to use.
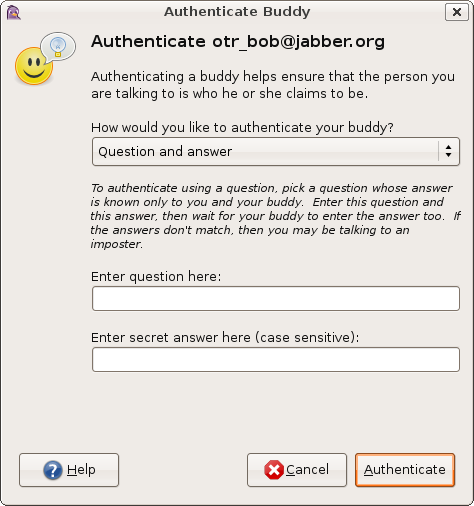
Question and answer
To authenticate using a question, pick a question whose answer is
known only to you and your buddy. Enter this question and this
answer, then wait for your buddy to enter the answer too. If the
answers don’t match, then either your buddy made a mistake typing in the
answer, or you may be talking to an imposter.
If your buddy answers correctly, then you have successfully
authenticated him or her, and the OTR status of this conversation
will change to «Private».
Your buddy will probably also want to ask you a question as well in
order for him or her to authenticate you back.
Note that this method first appeared in pidgin-otr 3.2.0; if your
buddy is using an older version, this will not work.
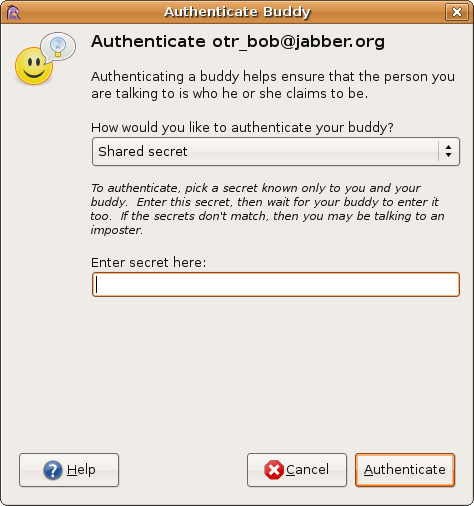
Shared secret
To authenticate someone with the shared secret method, you and your
buddy should decide on a secret word or phrase in advance. This can
be done however you like, but you shouldn’t type the phrase directly
into your conversation.
Enter the shared secret into the field provided in the Authenticate
Buddy dialog box. Once you enter the secret and hit OK, your buddy
will be asked to do exactly the same thing. If you both enter the
same text, then OTR will accept that you are really talking to your
buddy. Otherwise, OTR reports that authentication has failed. This
either means that your buddy made a mistake typing in the text, or
it may mean that someone is intercepting your communication.
Note that this method first appeared in pidgin-otr 3.1.0; if your
buddy is using an older version, this will not work.
Manual fingerprint verification
If your buddy is using a version of pidgin-otr before 3.1.0, or a
different OTR client that does not support the other authentication
methods, you will need to use manual fingerprint verification.
You will need some other authenticated communication channel (such
as speaking to your buddy on the telephone, or sending gpg-signed
messages). You should tell each other your own fingerprints. If
the fingerprint your buddy tells you matches the one listed as his
or her «purported fingerprint», pull down the selection that says «I
have not» (verified that this is in fact the correct fingerprint),
and change it to «I have».
Once you do this, the OTR status will change to «Private». Note
that you only need to do this once per buddy (or once per
fingerprint, if your buddy has more than one fingerprint).
pidgin-otr will remember which fingerprints you have marked as
verified.
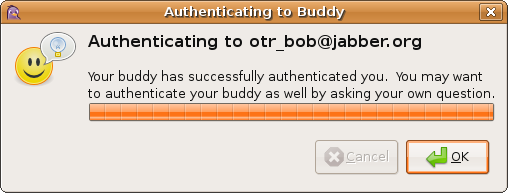
What the results mean
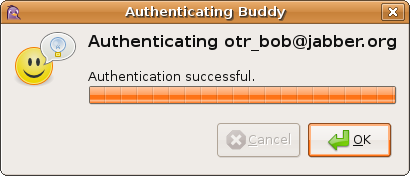
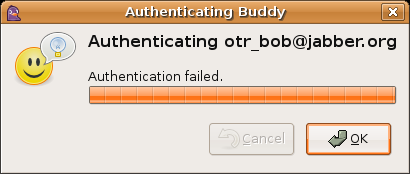
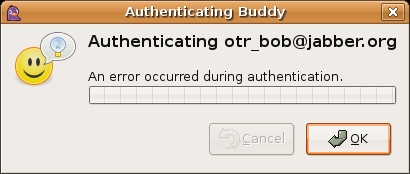
When you have entered your secret and hit OK, a progress bar pops up. This
bar should fill up to 100% and then display one of the following messages:
This means that authentication has been a complete success.
The OTR button will automatically change to «Private», showing that
conversations with this buddy are safe.
This means that although there were no errors, your buddy did not enter
the same text as you. You should try again, making sure that you are clear
about what to type (for example, «the restaurant name in lower case«).
If you repeatedly get this result, you should not trust that your buddy is who you think he or she is.
This means that something has gone wrong and the process could not complete
normally. This will happen if your buddy hits «cancel» or fails to receive
one of your messages. In this case, you should simply try again. If you try
several times and keep getting an error, you should not trust that your buddy is who you think he or she is.
This means that you answered your buddy’s authentication question successfully, so you have authenticated yourself to your buddy. However, your buddy has not yet authenticated to you. You may want to ask your buddy an authentication question by selecting «Authenticate buddy» from the OTR menu yourself.
A. Complete using a word formed from the letters given.
1 You can tell Martin is from Denmark by his ………………. . N C E C T A
2 Did the ………………. say that our plane was delayed or cancelled? E U N T N E C M A N O N
3 We’ve got relatives in Canada, but we don’t have much ………………. with them. T T A C N C O
4 You need to save what you’ve written as a ………………. and then send it to me by e-mail. E I L F
5 The first ………………. that was sent by radio from New York to London was a picture of the American president. A I E G M
6 The ………………. started in the 1980s and now it connects millions of computers around the world. T N R T N E I E
7 You need to ………………. the computers together and then you can send things directly from one to the other. N I K L
8 You shouldn’t believe everything you read or hear in the ………………. . D E A I M
9 According to the ………………. on the TV news, the Prime Minister is coming to our town soon. T O E P R R
10 You can’t listen to the radio when you’re on the underground because the ………………. isn’t strong enough. A N G S I L
11 If you’re a regular ………………. of our programme, then you’ll know that we often interview ordinary people. I E V R E W
12 I got the information from a ………………. . Hang on and I’ll give you the address. I B E S W T E
Answers
1 accent 2 announcement 3 contact 4 file
5 image 6 Internet 7 link 8 media
9 report 10 signal 11 viewer 12 website
B. Complete using the correct form of the verbs in the box.
broadcast • click • interrupt • pause • publish • ring • swear • type
1 You have to …………………… on the picture by pressing the left button on your mouse.
2 Writing and sending e-mails is a lot faster if you learn how to …………………… properly.
3 I couldn’t believe it when Greg …………………… in front of the head teacher!
4 The man on the telephone …………………… for a moment and then said, ‘Tell no one!’
5 This programme was first …………………… in 1967 and hasn’t been shown on TV since then.
6 Please don’t …………………… me. Let me finish what I wanted to say.
7 Our school might …………………… a weekly magazine to keep parents and students informed about what’s happening.
8 You should …………………… Michael and let him know about the plan for this evening.
Answers
1 click 2 type 3 swore 4 paused 5 broadcast
6 interrupt 7 publish 8 ring
C. Circle the correct word or phrase.
1 What John said on the phone wasn’t very clear / online so I asked him to repeat it.
2 Sandy waited until the teacher was looking the other way. ‘Meet me after school,’ he whispered / requested quietly in my ear.
3 How do you persuade / pronounce your name?
4 You should use formal / informal language when you’re writing to someone you don’t know personally.
5 Why do you keep on switching channels / mobile phones? I’m trying to watch this film!
Answers
1 clear 2 whispered 3 pronounce 4 formal 5 channels
D. Complete using the correct form of the phrasal verbs in the box.
call back • come out • cut off • fill in • hang up • log off • log on(to) • print out
1 I’ve got an e-mail from Mick! Wait a second and I’ll ……………….. it ……………….. so you don’t have to read it on the screen.
2 I was talking to Matt on the phone when the train went into a tunnel and we were ……………….. .
3 You just have to ……………….. this form and we’ll send the money for you.
4 My favourite magazine, Teen Scene, ……………….. every Friday.
5 Len was talking on the phone, but when I entered the room he ……………….. .
6 I can’t ……………….. because I can’t remember my password.
7 I’m afraid Mr Brown isn’t here. Could you ……………….. in an hour?
8 Tom surfed the Internet for hours and ……………….. at three in the morning!
Answers
1 print/out 2 cut off 3 fill in 4 comes out
5 hung up 6 log on 7 call back 8 logged off
E. Write one word in each gap.
News travels fast
These days, there’s no excuse for not knowing what’s happening in the world. (1) ………………… TV and on (2) ………………… radio, news programmes keep us up to date with all the important events. We read about problems on the other side of the world (3) ………………… the Internet as soon as they happen, and we see live pictures (4) ………………… the news 24 hours a day.
Even personal news travels fast today. Whether we keep in touch (5) ………………… phone or e-mail, we’re never more than a few seconds away from friends and family. The days when the only means of communication was (6) ………………… letter are gone forever. So, the next time you’re (7) ………………… the phone, just remember how things have changed.
Answers
1 On 2 the 3 on 4 on 5 by 6 by 7 on
F. Complete by changing the form of the word in capitals.
1 My ………………….. is that one day all phone calls will be free. PREDICT
2 Politicians often have a ………………….. with them when they go to other countries. TRANSLATE
3 I would hate to give a ………………….. in front of hundreds of people! SPEAK
4 Who knows what means of ………………….. will be invented in the future? COMMUNICATE
5 There’s something wrong with my ………………….. to the Internet, so I can’t send and receive e-mails. CONNECT
6 The mobile phone has ………………….. made life a lot easier. CERTAN
Answers
1 prediction 2 translator 3 speech
4 communication 5 connection 6 certainly
G. Use the word given in capitals to form a word that fits in the gap.
The Secret Message
I was walking down the street when a woman appeared in front of me. ‘Please! You must help me!’ she cried. I could tell from her (1) …………………. (EXPRESS) that she was frightened. She (2) …………………. (SPEAK) English with a Russian accent. She put a piece of paper into my hand. ‘This contains important (3) …………………. (INFORM). I can’t say any more, but there will be a (4) …………………. (DELIVER) tonight.’ She started to leave. ‘Contact the person in the message. But do it (5) …………………. (SECRET)! No one must know!’ I looked at the message but didn’t understand. When I looked up, she was gone. That was how my adventures began …
Answers
1 expression 2 spoke 3 information
4 delivery 5 secretly
H. Write one word in each gap.
1 I didn’t read the newspaper properly. I just glanced …………………. it, really.
2 I’ve got an e-mail in Spanish. Could you translate it …………………. English for me?
3 My grandma says people don’t talk …………………. each other like they used to.
4 You should receive a letter …………………. our company in the next few days.
5 Press this button to reply …………………. the e-mail.
6 I got a letter from Alex …………………. her new job. It sounds interesting.
Answers
1 at 2 into 3 to 4 from 5 to 6 about
I. Complete each second sentence using the word given, so that it has a similar meaning to the first sentence. Write between two and five words.
1 Did Olivia say anything about your website? comment
Did Olivia …………………………… your website?
2 Carl described his new mobile phone to me. told
Carl …………………………… his new mobile phone.
3 This website describes the history of communication. information
This website has …………………………… the history of communication.
4 Remind me to send Nigel a letter about our plans. write
Remind me to …………………………… our plans.
5 Some chimpanzees use sign language to talk to people. communicate
Some chimpanzees …………………………… people through sign language.
6 Could you tell Gail about the party by e-mail? send
Could you …………………………… Gail about the party?
Answers
1 comment on
2 told me about
3 information about
4 write to Nigel about
5 communicate with
6 send an e-mail to
Related Posts
- Practice English Vocabulary B1 Exercises – Vocabulary Test 1
- Practice English Vocabulary B1 Exercises – Vocabulary Review 14
- Practice English Vocabulary B1 Exercises – Vocabulary Review 13
- Practice English Vocabulary B1 Exercises – Vocabulary Review 12
- Practice English Vocabulary B1 Exercises – Vocabulary Review 11
- Practice English Vocabulary B1 Exercises – Vocabulary Review 10